Today’s cybersecurity landscape is increasingly complex. Threat actors now use AI to carry out sophisticated attacks that continuously evolve. As new AI technologies become more integrated into business operations, these intelligent threats adapt and grow more dangerous. As a result, every industry faces rising risks, especially those that are highly regulated, such as healthcare, finance, and governance.
Traditional cybersecurity measures cannot effectively counter these AI-driven strategies. A new approach has emerged: AI-powered DevSecOps integrated into the entire Software Development Lifecycle (SDLC), along with Runtime Application Self-Protection (RASP) as the last line of defense. RASP protects applications from within by detecting and stopping threats before they can take effect.
Enterprises report significant drops in phishing attacks on their AI-powered apps after Intellivon integrated DevSecOps and RASP into their platforms. We have also helped many enterprises achieve similar results. In this blog, we discuss our experience with how enterprise DevSecOps and RASP can outsmart new AI-powered cyber threats. This ensures smooth platform lifecycles, allowing you to concentrate on scaling.
Understanding the AI-Powered Cybersecurity Market
The global AI cybersecurity market will reach $93.75 billion by 2030, growing at a 24.4% CAGR from 2025 to 2030, according to Grand View Research. The global AI cybersecurity market demonstrates explosive growth patterns. Therefore, understanding these trends helps enterprises make informed security decisions.
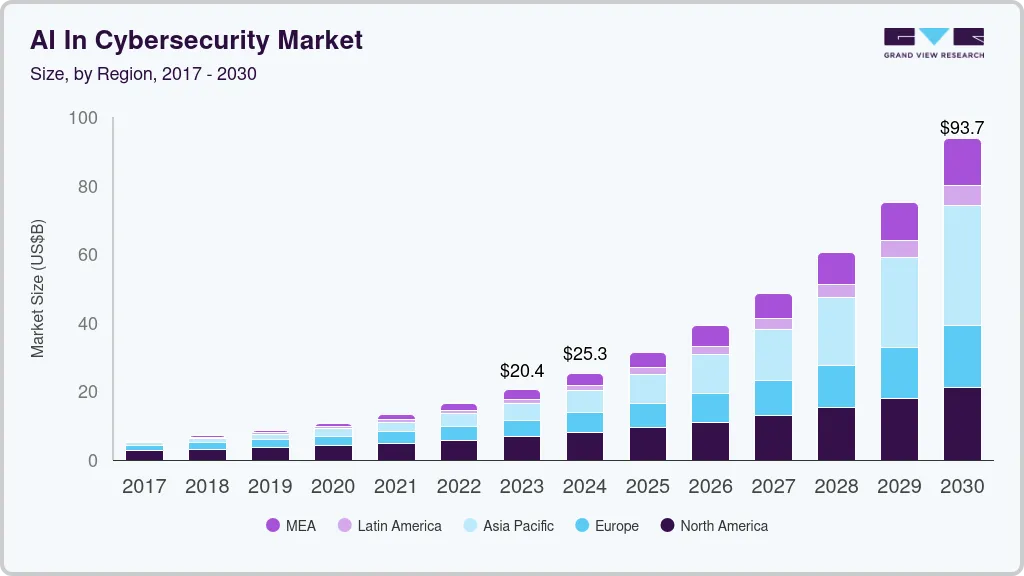
Key Market Takwaways:
- Furthermore, the RASP market is expected to cross $23.4 billion by 2025, growing at more than 33% CAGR per LLC Buddy statistics
- Hackers now use AI tools like ChatGPT to write more convincing phishing emails, according to Tech-Adv research.
- Additionally, phishing attacks show 8.4 out of every 1,000 users clicking phishing links monthly, nearly triple the previous rates per ISC2 analysis
- For instance, financial services demonstrate the critical need for AI-powered fraud detection tools.
Enterprise AI Security Adoption:
- Currently, 30% of organizations integrate AI security tools into operations, according to ISC2’s 2025 AI Pulse Survey.
- In addition, another 42% actively evaluate these solutions.
- Notably, 70% users of AI tools report measurable security efficiency improvements.
The bottom line is clear. AI-powered threats are becoming more sophisticated as the technology evolves. They manage to surpass AI-powered threat detection technology, so traditional methods cannot keep up anymore.
AI-Powered Threats in Enterprise Applications
AI-driven attacks are quickly changing the cyber-threat landscape today. Adversaries now use machine learning and generative AI to automate traditional attacks. These new threats are faster, more personalized, and much harder to detect. Here are some of the common AI-powered attacks that enterprises constantly face.
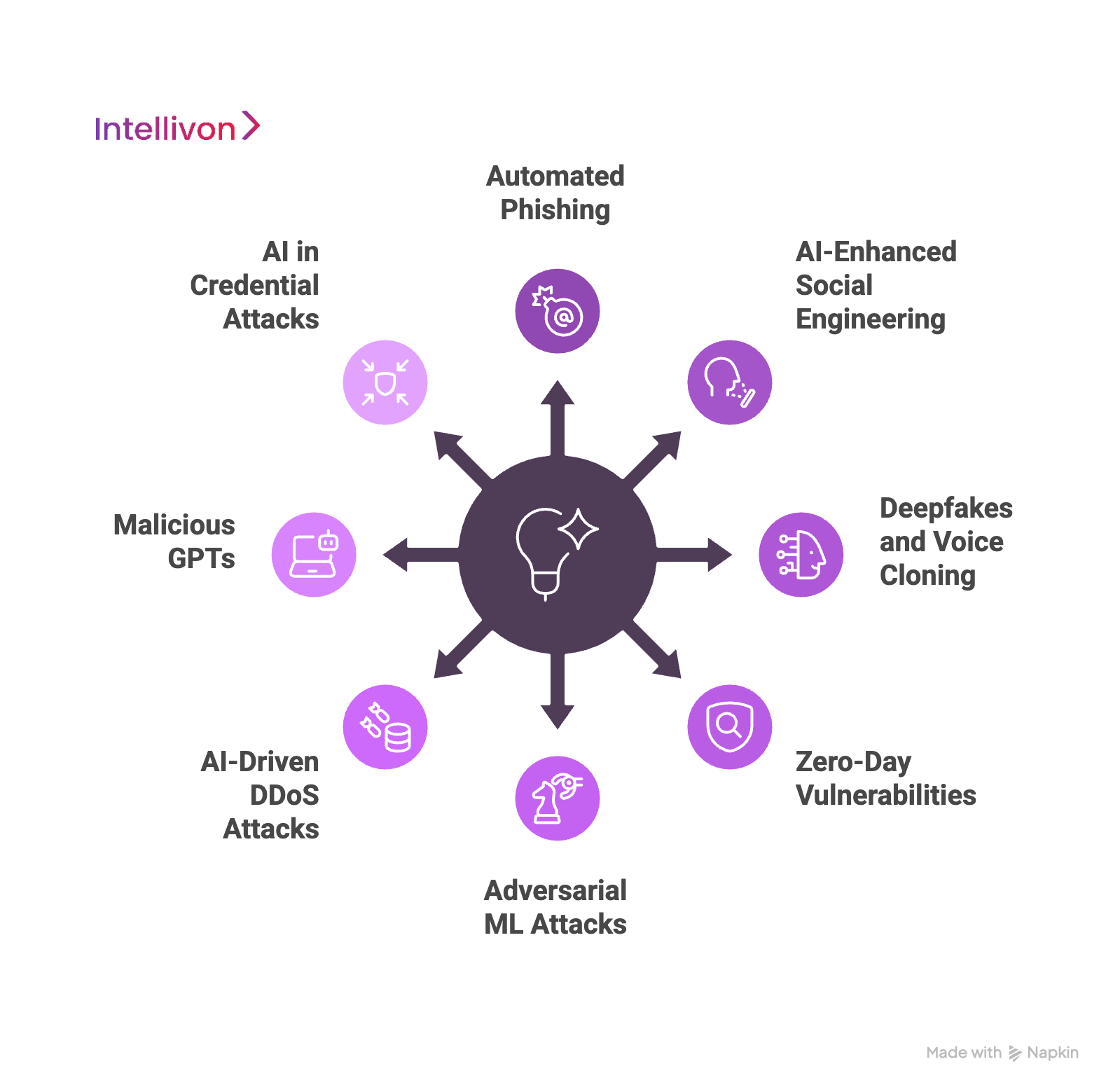
1. Automated Phishing and Spear-Phishing
Attackers leverage AI tools like ChatGPT to generate highly convincing emails and messages. Moreover, AI systems learn the company’s writing styles and create personalized lures.
Consequently, these sophisticated attacks improve success rates while evading traditional email filters.
2. AI-Enhanced Social Engineering
AI analyzes social media and corporate data to build detailed employee profiles. Similarly, attackers use this intelligence to craft hyper-personalized voice or text scams.
For example, deepfake audio/video impersonations of executives trick staff into revealing credentials or transferring funds.
3. Deepfakes and Voice Cloning
AI-generated audio/video content impersonates leaders or clients with alarming accuracy. Notably, attackers used AI voice cloning to impersonate a CFO, resulting in a $25 million fraudulent transfer at engineering firm Arup.
Additionally, the elaborate scam involved a multi-person video conference where everyone was in deepfake recreations, as reported by CNN. Therefore, these deepfakes enable new forms of insider-style fraud and disinformation campaigns.
4. Zero-Day Vulnerabilities
AI accelerates the search for unknown software flaws dramatically. Furthermore, ML tools rapidly scan codebases to find zero-day vulnerabilities. Consequently, attackers get shorter windows to exploit vulnerabilities before patches become available.
Additionally, AI enables polymorphic malware that constantly mutates its code to evade signature-based detection systems.
5. Adversarial ML Attacks
Attackers increasingly target AI/ML systems themselves through sophisticated methods. For instance, they poison training data or craft adversarial inputs that fool models completely.
Moreover, these attacks bypass image recognition systems and undermine AI-based defenses. Therefore, adversarial ML attacks represent an emerging enterprise risk requiring immediate attention.
6. AI-Driven DDoS Attacks
Leveraging AI capabilities, attackers craft adaptive distributed-denial-of-service campaigns with precision targeting. Notably, Cloudflare blocked 20.5 million DDoS attacks in Q1 2025, representing a 358% year-over-year increase. Furthermore, these smart DDoS floods target specific application layers while evading legacy defense mechanisms.
7. Malicious GPTs
Adversaries modify public LLMs into “malicious GPTs” that auto-generate attack content continuously. For example, these tools create new malware code, phishing emails, or exploitation prompts automatically.
Consequently, malicious GPTs lower the skill barrier, allowing less-experienced hackers to mount sophisticated campaigns.
8. AI in Credential Attacks
AI accelerates brute-force and credential-stuffing attacks by predicting passwords intelligently. Additionally, it powers “bot farms” that adapt strategies in real time. Therefore, traditional password protection methods become increasingly ineffective against AI-powered credential attacks.
These AI-powered threats already impact enterprises worldwide significantly. For instance, rising AI-based DDoS waves overwhelm traditional defenses completely. Moreover, enterprises facing these threats report higher volumes of stealthy, polymorphic attacks. Notably, 79% of detections in 2024 were malware-free, indicating a shift to fileless AI tactics. In summary, AI enables new attack types while empowering attackers to launch them faster and at greater scale.
Enterprise Adoption of DevSecOps and RASP
In response to AI-driven risks, enterprises embed security deeper into development and runtime processes. Therefore, organizations recognize that traditional perimeter defenses cannot handle modern threat landscapes.
DevSecOps Adoption Accelerates
DevSecOps practices shift security “left” into DevOps pipelines, gaining significant enterprise traction.
- Currently, 36% of respondents develop software using DevSecOps, compared with only 27% in 2020.
- DevSecOps market is forecast to reach $41.66 billion by 2030, with a CAGR of 30.76%.
- Additionally, 54% of organizations adopting DevSecOps report improved security, quality, and resilience as their primary goal.
Organizations invest heavily in DevSecOps platform enhancements as top IT priorities. Moreover, these shifts result from the need to catch vulnerabilities earlier in development cycles.
RASP Market Growth
RASP emerges as the final line of defense for enterprise applications.
- Notably, the global RASP market was valued at $3.08 billion in 2024 and is expected to reach $13.96 billion by 2032, expanding at a CAGR of 20.80%.
- Market analysts note that cloud adoption, machine learning integration, and regulatory pressures drive RASP uptake significantly.
- GDPR compliance requirements accelerate RASP adoption, particularly alongside DevSecOps practices.
- In addition, the U.S. RASP market alone grows from approximately $0.97 billion in 2024 to over $4.1 billion by 2032.
Combined Strategy Benefits
Both DevSecOps and RASP serve as key barriers against AI cyber threats through complementary approaches. For instance, DevSecOps ensures code remains secure from the development start. Similarly, RASP enforces protection in real time at runtime execution.
Their combined adoption reflects a layered security strategy: build protection into development while maintaining vigilance over live systems. Consequently, industry data support this trend as more organizations embed AI into security operations. Additionally, enterprises implementing both approaches report tangible security improvements and reduced incident response times.
AI-Powered DevSecOps for Enterprises
AI-Powered DevSecOps transforms enterprise security by integrating AI throughout the software development lifecycle. Therefore, this approach embeds AI-driven security tools directly into CI/CD pipelines. Furthermore, ML-based analysis automatically scans new code for vulnerabilities while dependency-scanning bots flag outdated libraries.
This methodology “bakes” security into every development stage, making defenses proactive rather than reactive. Additionally, building security from the start helps organizations catch vulnerabilities earlier. Consequently, enterprises improve compliance while reducing costly late-stage fixes significantly.
How AI-Powered DevSecOps Works
Understanding AI-powered workflows helps enterprises implement effective security automation. Therefore, examining these processes reveals how continuous protection works.
1. Automated Security Integration
An AI-DevSecOps workflow layers multiple security checks into automated build and deploy steps seamlessly. After each code commit, AI-powered SAST tools perform deep code reviews within seconds. Moreover, these tools find issues that manual reviews typically miss completely.
Dynamic analysis (DAST) with AI runs automated penetration tests against builds continuously. Similarly, continuous configuration scanning ensures cloud and container settings remain secure throughout deployment cycles. Additionally, AI/ML models analyze logs and telemetry to detect anomalies before deployment occurs.
2. Adaptive Learning Systems
These intelligent systems learn from each iteration, creating adaptive security feedback loops. For instance, failing tests or alerts help refine detection rules automatically. Therefore, the security posture improves continuously as the AI models encounter new threat patterns.
Importantly, AI agents can triage results and suggest fixes based on historical data. Furthermore, this reduces manual intervention while maintaining high-security standards across development teams.
Key Benefits of Enterprise DevSecOps Integration
AI-driven security delivers measurable improvements in threat detection. Furthermore, these benefits translate into reduced risk and faster development.
1. Accelerated Threat Detection
AI-enabled solutions provide predictive threat detection and real-time defense capabilities that outperform legacy tools significantly. Moreover, these platforms analyze development and runtime data to foresee potential risks. For example, AI can predict which new code patterns are likely vulnerable before deployment.
2. Enhanced Team Effectiveness
ISC2 found that 70% of organizations using AI security tools see significant improvements in team effectiveness. Additionally, security teams can focus on the riskiest alerts while routine vulnerabilities receive auto-remediation.
3. Faster Resolution Times
Enterprises adopting AI-DevSecOps report faster time-to-fix and fewer security breaches overall. Furthermore, automated threat response reduces mean time to resolution dramatically. Consequently, development velocity increases without compromising security standards.
4. Dynamic Attack Prevention
These platforms block attacks dynamically by analyzing behavioral patterns in real time. Therefore, organizations can prevent zero-day exploits and advanced persistent threats more effectively than traditional approaches allow.
Therefore, enterprises experience significant security improvements with AI-powered DevSecOps. Additionally, these benefits compound as AI systems learn organizational patterns.
Industry-Specific Use Cases
Different industries use AI-powered DevSecOps for unique security challenges. Moreover, real implementations show tangible results across sectors.
1. Financial Services Security
- Financial institutions use AI to scan and protect online banking applications continuously. Moreover, these systems detect fraud patterns in code changes before deployment occurs. For instance, Visa blocked $80 million in fraudulent transactions using ML fraud detection.
- Banks implement AI-powered DevSecOps to secure payment processing systems against sophisticated attacks. Additionally, regulatory compliance requirements drive the adoption of automated security scanning throughout development pipelines.
2. Healthcare Data Protection
- Healthcare firms apply AI scanning to ensure patient-data applications comply with HIPAA regulations. Furthermore, these tools detect anomalies in medical IoT deployments that could compromise patient privacy. Therefore, healthcare organizations maintain strict data protection standards while accelerating digital transformation initiatives.
- AI-driven security helps identify potential vulnerabilities in electronic health record systems before they reach production environments. Consequently, patient data remains protected throughout the development lifecycle.
3. Retail and E-commerce Security
- Retail companies use AI-driven tests to secure payment and point-of-sale systems comprehensively. Moreover, these solutions protect customer payment information during online transactions continuously. Additionally, AI tools detect suspicious patterns in shopping cart abandonment that might indicate security issues.
- E-commerce platforms implement continuous security monitoring to protect against credential stuffing and account takeover attacks. Therefore, customer trust remains high while reducing fraud-related losses significantly.
4. Government and Defense Applications
- Government agencies employ AI within DevSecOps to secure critical infrastructure projects effectively. Furthermore, the volume of code and threat of state-sponsored attacks demand automation capabilities.
- Defense contractors use AI-powered security scanning to meet stringent compliance requirements. Consequently, classified systems receive continuous protection throughout their development lifecycles.
Implementation Roadblocks and Challenges
Organizations face common obstacles when implementing AI-powered DevSecOps solutions. However, understanding challenges helps prepare effective mitigation strategies.
1. Technical Complexity Issues
According to industry surveys, 60% of respondents find DevSecOps technically challenging. Moreover, integrating disparate tools into unified pipelines requires significant expertise. Additionally, training AI models with relevant security data demands specialized knowledge.
Organizations struggle with tool compatibility and data integration across different development environments. Therefore, technical teams need comprehensive training to manage complex AI-powered security systems effectively.
2. Cost and Resource Constraints
Industry surveys show that 40% of organizations say DevSecOps is expensive to implement. Furthermore, licensing costs for enterprise AI security tools can be substantial. Additionally, organizations need skilled personnel to configure and maintain these systems properly.
Budget constraints often limit the scope of initial AI-DevSecOps implementations. Consequently, enterprises must prioritize high-risk applications for initial deployment phases.
3. AI Model Limitations
Organizations worry about AI false positives and “black-box” decision-making processes. Moreover, AI can auto-generate insecure code with hardcoded secrets or open permissions if left unchecked. Therefore, human oversight remains essential for critical security decisions.
Model drift and outdated training data can reduce effectiveness over time. Additionally, AI systems may miss novel attack patterns not present in historical training datasets.
Best Practices for Successful Implementation
Proven strategies help organizations maximize AI-powered DevSecOps benefits. Therefore, these practices ensure sustainable security improvements.
1. Shift-Left Security Integration
Integrate AI-based scanners (SAST/DAST/IAST) early in development cycles for immediate developer feedback. Furthermore, this approach catches vulnerabilities before they propagate through the pipeline. Additionally, developers receive real-time guidance on secure coding practices.
Early integration reduces remediation costs while improving overall code quality significantly. Therefore, security becomes a natural part of the development process rather than an afterthought.
2. AI-Augmented Code Reviews
Use ML-driven code review and dependency analysis to speed up security checks effectively. However, ensure human validation for critical security issues that require contextual understanding. Moreover, combine AI alerts with manual triage to reduce false positive rates.
Experienced security analysts should validate high-risk findings before blocking deployments. Consequently, development velocity remains high while maintaining security standards.
3. Continuous Model Updates
Regularly update AI threat models and training data to maintain effectiveness against evolving threats. Furthermore, keep security AI tools current with the latest threat intelligence. Additionally, monitor model performance metrics to identify degradation over time.
Establish feedback loops between security incidents and model training to improve detection capabilities continuously. Therefore, AI systems adapt to emerging attack patterns dynamically.
4. Explainable AI Implementation
Adopt AI tools with transparency features so analysts understand alert triggers clearly. Moreover, explainable AI builds trust among security teams and developers. Additionally, transparent decision-making helps refine tools based on real-world performance.
Documentation and audit trails ensure compliance with regulatory requirements. Consequently, organizations can demonstrate due diligence in security practices.
5. Security Culture Development
Provide comprehensive developer training on secure coding and AI tool usage. Furthermore, encourage security champions who work effectively with AI-powered tooling. Additionally, include AI-security training as part of DevSecOps adoption programs.
Regular workshops and hands-on training ensure teams maximize AI tool benefits. Therefore, security awareness becomes embedded in organizational culture rather than imposed externally.
When implemented correctly, AI-empowered DevSecOps dramatically improves enterprise security postures. It automates routine checks while uncovering subtle threats at scale. Organizations deliver secure applications faster with reduced manual effort and
RASP as a Final Enterprise Security Barrier
Runtime Application Self-Protection (RASP) is a powerful security technology that embeds sensors directly inside an application’s runtime environment. Unlike traditional perimeter tools such as Web Application Firewalls (WAFs), which protect traffic at the network edge, RASP works from within the application itself.
This approach gives RASP a unique advantage: it monitors real-time application behavior, inputs, data flow, and control logic. As a result, it can detect and block attacks that exploit the application’s internal logic or previously unknown vulnerabilities.
For example, imagine an attacker tries to send a malicious SQL query to your application. A WAF may block this only if it matches a known attack pattern. But if the payload looks normal, it might slip through. RASP, however, observes the query reaching the database layer and blocks it in real time because it understands the context of that call.
Key Benefits of RASP for Enterprise Threat Detection
Modern enterprises face increasingly sophisticated threats, especially as AI-powered attacks grow more adaptive. RASP provides powerful, real-time security by embedding directly into the application. Below are its key advantages in detail.
1. Behavioral Detection
RASP monitors the application’s internal logic as it runs. It identifies abnormal actions that could indicate an attack, such as unusual calls to high-privilege functions. This makes it effective against complex threats that do not match known signatures.
For example, a banking app using RASP can detect an API call that suddenly attempts to access an administrative function outside of normal workflows.
2. Zero-Day Protection
Because RASP makes decisions based on live application behavior rather than relying solely on threat signatures, it can block zero-day attacks as they happen. Traditional tools often fall behind since they require time to update signature databases.
With RASP, even previously unknown exploits are stopped in real time before they can cause damage.
3. Reduced False Positives
One common problem with perimeter security tools is high false positive rates. WAFs, for instance, may block legitimate traffic because they lack insight into the app’s inner workings.
RASP excels in this area because it understands the application’s intended behavior. This contextual awareness helps it more accurately distinguish malicious from legitimate actions, reducing unnecessary alerts.
4. Deep Threat Intelligence
RASP gathers detailed telemetry from within the application, such as user context, exploited endpoints, and call stacks.
This rich data helps security teams investigate attacks more effectively and fine-tune their defenses. It also supports compliance requirements by providing clear evidence of how an attack was prevented.
5. Real-Time Attack Mitigation
Unlike tools that alert after an attack has occurred, RASP actively blocks suspicious actions in real time. This prevents damage before it happens, giving enterprises an immediate response to unknown threats.
6. Seamless Integration with Application Workflows
RASP integrates directly into the application’s runtime environment without the need for extensive external configuration. This makes it easier to deploy compared to network-level defenses, reducing complexity in fast-moving development cycles.
6. Enhanced Developer Security Awareness
Because RASP runs within the app, it provides developers with direct feedback about security weaknesses during development and testing phases. This helps close security gaps early in the software development lifecycle.
How Enterprises Use RASP in Practice
Enterprises today face a wide variety of complex threats, especially from AI-powered attacks that adapt and evolve in real time. RASP acts as a final security barrier by embedding protection directly into applications. Below, we explore real-world use cases where enterprises benefit from RASP across industries.
1. Protecting Online Banking Systems
Financial institutions face constant attempts to exploit online banking systems. By embedding RASP, banks monitor API calls and transaction workflows.
If an attacker tries to bypass authentication or execute unauthorized transfers, RASP blocks the action in real time. This helps prevent fraud and protects sensitive customer data from abuse.
2. Securing E-Commerce Checkout Flows
E-commerce sites are prime targets for bot attacks and checkout manipulation. RASP monitors shopping cart and payment processes for suspicious behavior.
For example, it can detect bots trying to perform automated checkout fraud or attempts to tamper with price fields. This ensures genuine customer purchases aren’t interrupted while malicious activities are stopped immediately.
3. Guarding Mobile Application Backends
Mobile applications often expose APIs that are critical but vulnerable. RASP helps by analyzing every API request in context, blocking those that behave abnormally.
A retail chain using RASP in its mobile app backend, for example, prevents attackers from abusing APIs to extract customer data or manipulate loyalty points.
4. Protecting Microservices Architectures
Enterprises are rapidly adopting microservices for scalability and agility. However, each microservice is a potential attack surface.
RASP provides granular security by embedding protection into each microservice, watching inter-service calls and data exchanges. This prevents attackers from exploiting API chains or poorly secured endpoints to escalate privileges.
5. Safeguarding Critical Internal Applications
Large organizations run internal applications such as ERP and CRM systems that contain valuable business logic and sensitive data. Traditional network defenses often leave these systems exposed once an attacker bypasses the perimeter.
RASP guards these applications by monitoring internal workflows, such as unusual data export activities or unexpected access to sensitive modules, blocking them in real time.
6. API Abuse Prevention
APIs are the backbone of modern enterprise services, but are increasingly abused by attackers for data scraping, credential stuffing, or privilege escalation.
RASP enables fine-grained monitoring of API usage, detecting patterns such as repeated failed login attempts or unusual query patterns, and blocking them automatically.
These use cases demonstrate how RASP provides proactive, contextual protection for mission-critical applications in the face of modern AI-powered threats. By working from within the application, it offers a level of visibility and defense that traditional perimeter tools simply can’t match.
Roadblocks to Implementing RASP in Enterprise Applications
While RASP offers powerful, real-time protection, many enterprises face challenges when integrating it into their existing environments. Understanding these roadblocks helps organizations plan better and avoid common pitfalls.
1. Performance Overhead Concerns
One common concern is that embedding security directly into the application may slow it down. Since RASP continuously monitors application behavior at runtime, some worry it will add latency or affect user experience.
However, modern RASP solutions are designed to minimize performance impact through optimized code instrumentation and efficient telemetry collection.
2. Complexity in Integration
Integrating RASP into existing applications, especially large legacy systems, can be complicated. It requires careful instrumentation of application code and close collaboration between security and development teams.
Without proper planning, this integration may lead to instability or unexpected behavior in production environments.
3. Lack of Developer Security Expertise
Many development teams lack deep security knowledge, making it difficult to implement RASP effectively. Developers may not know where to instrument the code or how to handle RASP alerts properly.
This can lead to misconfigurations or the disabling of critical RASP functions, reducing its effectiveness.
4. False Sense of Security
Some organizations mistakenly treat RASP as a complete security solution. While powerful, RASP is designed to work in combination with other security layers, not as a standalone tool.
Relying solely on RASP without maintaining secure coding practices, proper access controls, and regular testing creates gaps in protection.
5. Cost and Licensing Challenges
Implementing RASP solutions can involve significant costs, especially in large enterprises with complex applications. Licensing models may be based on the number of applications, CPU usage, or other metrics, which can add up quickly.
Without a clear ROI calculation, some decision-makers hesitate to invest in RASP, viewing it as an added expense rather than a long-term security necessity.
6. Limited Visibility in Environments
In highly distributed or containerized environments, it can be difficult for RASP to maintain full visibility across all services and workloads. This can result in blind spots where some microservices or serverless functions are not adequately protected.
Enterprises must carefully plan their architecture to ensure RASP instruments every relevant component.
These roadblocks highlight why implementing RASP requires careful strategy and cross-team collaboration. Enterprises that address these challenges properly can unlock RASP’s full potential, turning it into a highly effective shield against modern AI-powered cyber threats. With Intellivon’s expertise in embedding RASP into enterprise applications, you can ensure that your business has used this technology to its full potential.
Best Practices to Implement RASP in Enterprise Applications
Implementing RASP effectively requires more than just installing a tool. It involves strategy, collaboration, and ongoing management. The following best practices help enterprises get the most from their RASP deployment while minimizing risks and complexity.
1. Early SDLC Integration
The best time to integrate RASP is during development and testing, not after the application is live. Embedding RASP from the start helps catch vulnerabilities early and allows developers to fine-tune protection without disrupting production.
This approach also improves security awareness across the development team.
2. Security-Development Collaboration
RASP implementation works best when security and development teams work together. Security experts help define appropriate protection policies, while developers understand where and how to instrument the application code.
This collaboration avoids misconfigurations and ensures the RASP engine aligns with business logic.
3. Prioritize High-Risk Applications
Not all applications need RASP from day one. Enterprises should prioritize protecting applications that handle sensitive data, financial transactions, or critical business processes.
For example, online banking apps or internal ERP systems should be secured before less sensitive tools like marketing websites.
4. Tune and Update Policies
RASP solutions rely on behavioral rules and policies to detect threats. To remain effective, these rules must be regularly reviewed and adjusted.
Analyzing attack patterns and telemetry helps security teams reduce false positives and improve detection accuracy over time.
5. Ensure Minimal Performance Impact
Performance should never be an afterthought. When implementing RASP, it’s important to monitor application performance closely and adjust configurations if needed.
Using lightweight instrumentation and prioritizing critical paths helps maintain smooth user experiences without compromising security.
6. Integrate with CI/CD
Embedding RASP into continuous integration and delivery (CI/CD) pipelines ensures security remains part of every software update.
This way, every new feature or code change is automatically tested for security weaknesses, and protection remains active in production without manual intervention.
Following these best practices allows enterprises to deploy RASP successfully while maximizing its security benefits. In doing so, they significantly reduce their risk of falling victim to advanced AI-powered attacks.
Our Integrated Approach: RASP + AI-Powered DevSecOps for Enterprises
At Intellivon, we understand that modern enterprise security can no longer rely on isolated tools. Today’s AI-powered threats are adaptive and fast-moving. That’s why we deliver comprehensive, end-to-end security by combining AI-driven DevSecOps with Runtime Application Self-Protection (RASP).
This integrated approach covers every stage of the software lifecycle, from code development to production runtime, ensuring continuous protection. Instead of patchwork solutions, we provide enterprises with a unified strategy that detects vulnerabilities during development and blocks active attacks in real time. This is because:
- By embedding AI-powered DevSecOps into the CI/CD pipeline, we prevent vulnerabilities from ever reaching production.
- Then, at runtime, RASP monitors application behavior in real time, stopping unknown or zero-day threats as they happen.
- This combination reduces the risk of breach, lowers false positives, and improves threat intelligence.
Enterprises adopting Intellivon’s solution achieve not only better security posture but also smoother application performance and faster development cycles, helping them stay secure without slowing down innovation.
Our Architectural Suite for Secure DevSecOps and RASP Enterprise Integration
At Intellivon, we design security solutions to meet the needs of large-scale global enterprises. Our architectural suite is built on a multi-layered, closed-loop system that delivers both proactive and runtime protection. This approach ensures continuous security across the entire software lifecycle, without slowing down development or impacting performance.
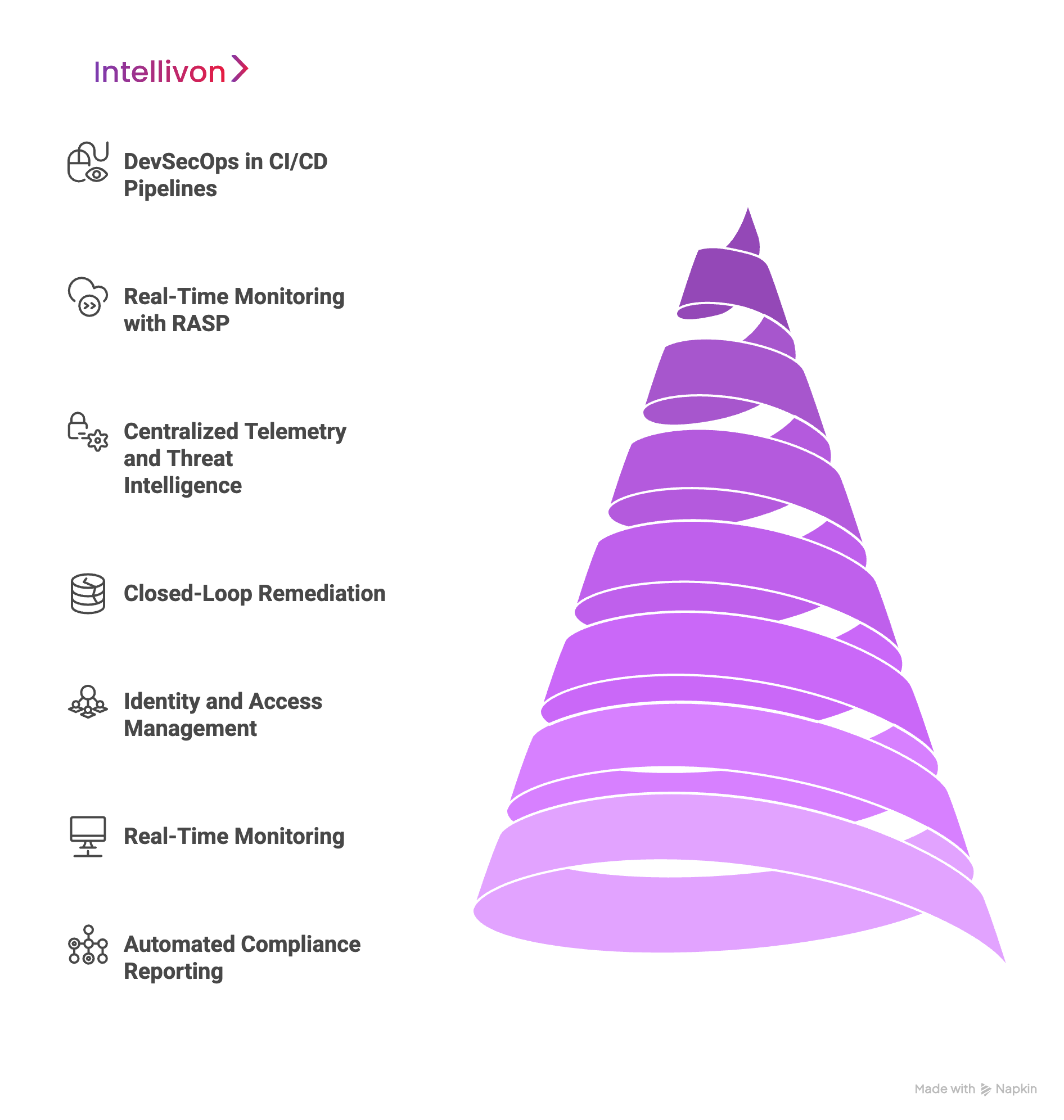
1. Layer 1: DevSecOps in CI/CD Pipelines
We start by embedding AI-driven DevSecOps directly into the CI/CD pipeline. Every code change passes through automated static and dynamic analysis tools powered by ML.
These checks identify security vulnerabilities, insecure coding patterns, and compliance gaps before they reach production. This layer prevents vulnerabilities from being built into the application in the first place, saving time and reducing risk.
2. Layer 2: Real-Time Monitoring with RASP
Once the application is in production, our RASP technology takes over. RASP continuously monitors application inputs, control flows, and data usage in real time.
It detects and blocks malicious behavior such as abnormal API calls, unexpected privilege escalations, or data tampering attempts. Because it operates within the application runtime, it has unmatched visibility into the actual business logic being executed.
3. Layer 3: Centralized Telemetry and Threat Intelligence
All security events and telemetry data from both CI/CD and RASP layers are aggregated into a centralized dashboard. This provides security and development teams with real-time insights into vulnerabilities, blocked threats, and application health.
The system continuously analyzes trends, allowing for faster incident response, intelligent policy adjustments, and precise threat forensics.
4. Layer 4: Closed-Loop Remediation
Our architecture follows a closed-loop approach. Insights from runtime threat intelligence feed directly back into the development process.
This allows teams to fix security gaps quickly and automatically tune detection rules for evolving threats. Continuous learning ensures that, as new attack patterns emerge, the solution adapts without manual intervention.
5. Layer 5: Identity and Access Management
Strong identity and access management (IAM) complements RASP and DevSecOps.
We integrate IAM controls to enforce role-based access across both development and runtime environments.
This limits who can deploy code, access production applications, and modify security policies. Such control prevents insider threats and ensures only authorized actions are allowed at every layer.
6. Layer 6: Container and Cloud-Native Environment Protection
As many enterprises move to containers and cloud-native applications, securing these environments becomes critical. Our solution instruments microservices and serverless functions with RASP technology.
It protects inter-service communication, prevents container escape attacks, and monitors workload behavior. This ensures security keeps up with highly dynamic environments without slowing down development velocity.
7. Layer 7: Automated Compliance Reporting
Compliance requirements like PCI DSS, HIPAA, and GDPR are essential for enterprises. Our architecture automatically collects and organizes telemetry data to generate compliance reports.
This gives security teams clear evidence of protected systems and prevents breaches. It also simplifies audits by providing up-to-date, actionable reports on security status.
This multi-layered architecture enables Intellivon to deliver seamless, automated security that grows stronger over time. Enterprises don’t need to piece together siloed tools. Instead, they get a robust, end-to-end solution that protects against AI-powered threats, secures critical business logic, and drives faster, safer development cycles.
Real-World Industry Use Cases of DevSecOps and RASP Integration
Combining AI-powered DevSecOps and RASP provides enterprises with a powerful, multi-layered defense.
This approach applies across industries, helping organizations fight modern AI-driven cyber threats in practical, high-impact ways. Below are five comprehensive industry use cases supported by real-world examples.
1. Financial Services
Financial institutions manage highly sensitive customer data and financial transactions, making them top targets for cybercriminals. In 2016, Bangladesh Bank was hit by an $81 million cyber heist through compromised SWIFT systems (source).
Using DevSecOps, banks scan and fix vulnerabilities in their applications during development, preventing security gaps from ever reaching production. At the same time, RASP monitors application behavior in real time.
For example, if a malicious API call tries to manipulate a funds transfer outside predefined workflows, RASP detects and blocks it instantly. This prevents fraudulent transactions while ensuring regulatory compliance such as PCI DSS.
2. E-Commerce
E-commerce platforms face constant risks from automated bots, carding attacks, and price manipulation schemes. British Airways experienced a massive data breach in 2018, exposing thousands of payment card records via a compromised web checkout.
In this use case, DevSecOps embeds automated security checks during development, ensuring new checkout features are free from vulnerabilities. Once in production, RASP continuously analyzes user interactions and API calls.
For example, RASP can block a bot that tries to abuse discount codes by repeatedly firing checkout requests. This protects revenue, prevents customer data loss, and preserves the user experience during high-traffic periods like Black Friday.
3. Healthcare
Healthcare organizations must protect sensitive patient information while maintaining system uptime. In 2019, the University of Washington Medicine disclosed a ransomware attack that exposed patient records.
With DevSecOps, developers scan EHR applications for insecure coding patterns and compliance violations early in the software lifecycle. In production, RASP protects APIs and backend services by detecting abnormal access patterns.
For example, if a user suddenly tries to retrieve large volumes of patient records outside expected usage patterns, RASP flags and blocks the attempt in real time.
This prevents data leaks while ensuring compliance with HIPAA.
4. Manufacturing
Industrial control systems in manufacturing are vulnerable to remote attacks that can disrupt production or cause physical damage. The Stuxnet worm attack on Iranian nuclear centrifuges in 2010 famously exploited ICS weaknesses.
DevSecOps ensures that software controlling ICS systems is regularly scanned for vulnerabilities during development. In production, RASP monitors interactions between control systems and human-machine interfaces (HMIs).
For example, if an attacker tries to send abnormal commands to a robotic assembly line, RASP detects this behavior and blocks the attempt before any harm is done. This ensures uninterrupted production while maintaining a strong defense against sophisticated threats.
5. Securing Internal Business Applications (ERP, CRM)
Large enterprises use ERP and CRM systems to manage internal workflows and critical data. In 2021, Accenture suffered a ransomware attack that compromised internal applications.
Using DevSecOps, enterprises prevent vulnerable code from entering production by performing automated vulnerability scans during development. Once deployed, RASP protects ERP and CRM applications by monitoring for unusual data exports or privilege escalations.
For example, if a user attempts to export thousands of customer records outside of normal reporting processes, RASP detects the behavior and stops it immediately. This ensures sensitive corporate data stays secure and compliance requirements are met without manual intervention.
These use cases show the real-world impact of combining AI-driven DevSecOps with RASP. They highlight how enterprises across industries secure their most critical systems by detecting vulnerabilities early and stopping active threats in real time.
Step-by-Step Process: How Intellivon Delivers Enterprise DevSecOps and RASP Solutions
At Intellivon, we follow a structured, proven process to integrate AI-powered DevSecOps and RASP into enterprise environments. This ensures maximum security with minimal disruption, helping enterprises detect vulnerabilities early and block advanced threats in real time. Here’s a detailed, step-by-step overview of our solution delivery process:
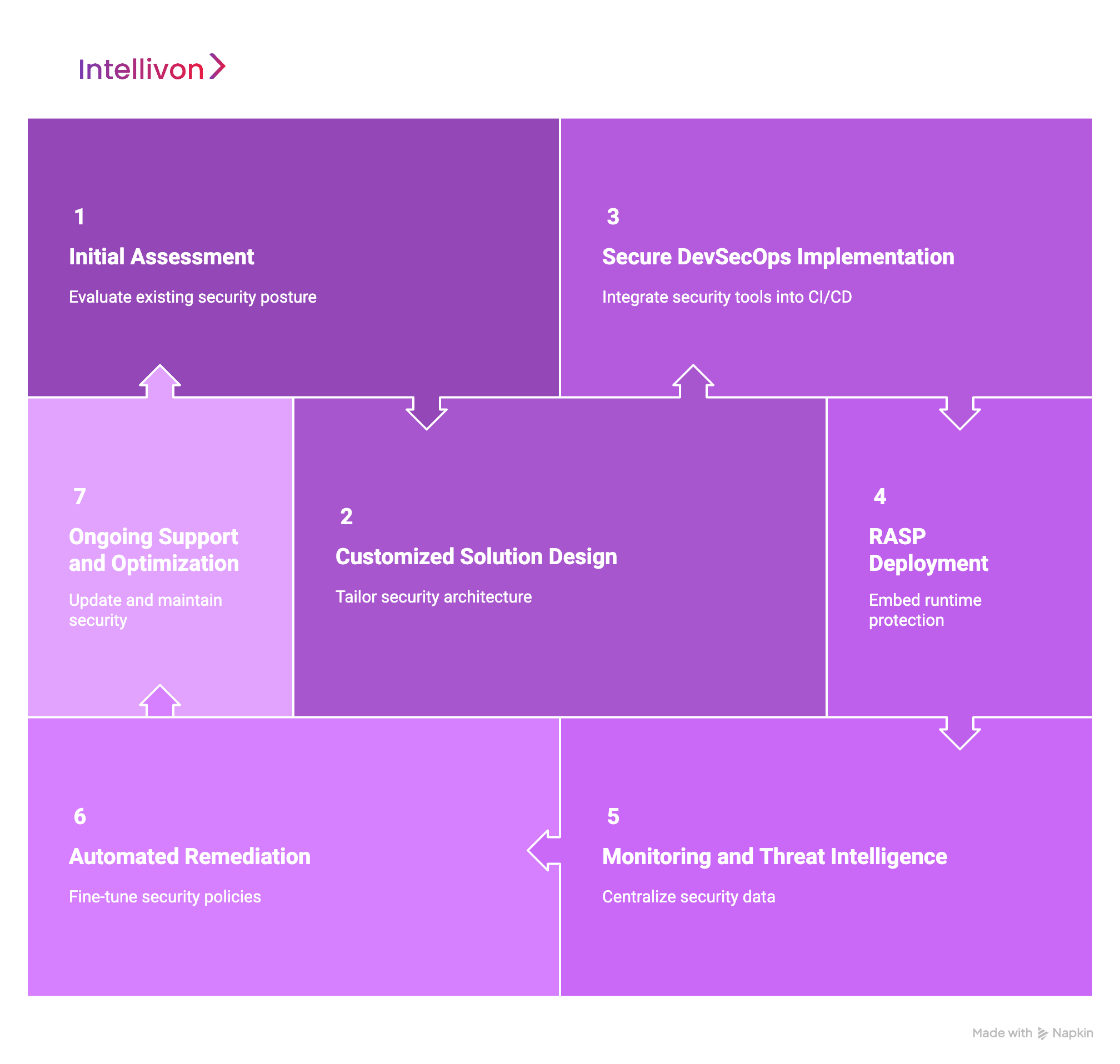
Step 1: Initial Assessment
We begin by conducting a thorough assessment of your enterprise’s software development workflows, application architecture, and security posture. Our experts analyze existing CI/CD pipelines, runtime environments, and key applications to understand potential security gaps.
We also gather business goals, compliance needs, and specific risk profiles. This helps us design a solution that fits your enterprise’s unique environment and priorities.
Step 2: Customized Solution Design
Based on the assessment, we design a tailored solution architecture that integrates AI-driven DevSecOps and RASP into your environment. This design includes:
- Automated security checks integrated into your CI/CD pipeline
- RASP instrumentation of critical applications for runtime protection
- Centralized telemetry and threat intelligence dashboards
- Closed-loop remediation mechanisms
The solution is flexible and adapts to hybrid environments, cloud-native stacks, and traditional infrastructure.
Step 3: Secure DevSecOps Implementation
We integrate AI-powered security tools directly into your CI/CD workflows. Static Application Security Testing (SAST) and Dynamic Application Security Testing (DAST) tools run automatically during code commits, builds, and deployments.
Our AI algorithms detect insecure coding patterns, vulnerable dependencies, and compliance violations before applications reach production. This helps developers fix vulnerabilities early, reducing remediation costs and accelerating time-to-market.
Step 4: RASP Deployment
RASP is embedded into your critical applications, such as web apps, APIs, and microservices. The RASP layer monitors real-time behavior, including user inputs, API calls, and control flow execution.
It flags and blocks suspicious activities like privilege escalation attempts, unexpected data exports, or abnormal API access patterns. This layer ensures zero-day threats are stopped in real time, even when no signature exists.
Step 5: Monitoring and Threat Intelligence
All security events and telemetry data flow into a centralized dashboard. This provides security teams and developers with actionable insights, including:
- Detailed attack logs
- Real-time alerts
- Anomaly detection trends
- Policy tuning recommendations
The dashboard simplifies compliance reporting and provides full visibility into security posture.
Step 6: Automated Remediation
Our solution closes the feedback loop by feeding runtime insights back into the development process. Detected threats, false positives, and blocked attack patterns are analyzed to fine-tune security policies automatically.
This helps ensure the system adapts to emerging threats over time. Continuous learning keeps protection strong without requiring manual effort from your teams.
Step 7: Ongoing Support and Optimization
Intellivon provides ongoing support to ensure your security solution evolves with your environment. We regularly update detection algorithms, optimize RASP configurations, and help you maintain compliance with changing regulations. Our proactive monitoring ensures that any newly discovered vulnerabilities or attack patterns are addressed immediately.
This step-by-step process helps enterprises embed strong, automated security throughout their software development and production environments. If you’re ready to strengthen your enterprise’s security posture and stay ahead of AI-powered threats, discover how a fully integrated DevSecOps and RASP strategy can protect your critical applications today. Let’s help you build security into your development lifecycle and stop threats in real time, without slowing down innovation.
Conclusion
AI-based cyber threats are growing faster, smarter, and more difficult to detect. Traditional security tools like WAFs and signature-based scanners can no longer keep pace with changing attack methods. Combining AI-driven DevSecOps with RASP provides a strong, flexible defense for businesses.
This method secures code during development and monitors applications in real time. It prevents vulnerabilities and halts attacks as they occur. It lowers risk, improves compliance, and encourages quicker innovation. Businesses that adopt this strategy achieve better visibility, fewer false positives, and stronger protection against zero-day exploits. This makes security a facilitator, not an obstacle.
Build a Resilient Enterprise App with AI-Powered DevSecOps and RASP
Securing modern enterprise applications requires more than traditional defenses. It means integrating intelligent security throughout development and runtime to prevent evolving AI-driven threats. With years of experience delivering advanced, enterprise-grade security solutions, we help you build software that stays secure by design.
Why Choose Us for Enterprise DevSecOps and RASP Integration?
- Comprehensive Security Coverage: Embed security checks in CI/CD pipelines and real-time application protection with RASP.
- Adaptive Threat Detection: Automatically block zero-day exploits and advanced attacks in production.
- Clear Compliance Reporting: Simplify audits with automated policy enforcement and rich telemetry.
- Seamless Integration: Fit into cloud-native, hybrid, and legacy environments without disrupting workflows.
- Optimized Development Speed: Security automation that lets your teams focus on innovation.
Our security experts are ready to help you:
- Assess your current development and runtime security posture.
- Design a tailored solution architecture based on your enterprise needs.
- Implement AI-powered DevSecOps and RASP for continuous protection.
- Provide ongoing support, monitoring, and policy tuning.
Get in touch today and start future-proofing your enterprise applications against advanced cyber threats.
FAQ’s
Q1. What is Enterprise DevSecOps and why is it important?
A1. Enterprise DevSecOps integrates security directly into the software development lifecycle. It ensures vulnerabilities are detected and fixed during development rather than after deployment. This approach reduces risks, improves compliance, and accelerates software delivery by making security a continuous, automated part of development.
Q2. How does RASP protect applications from AI-powered attacks?
A2. Runtime Application Self-Protection (RASP) monitors applications in real time.It detects unusual behavior, malicious inputs, or privilege escalations and blocks them instantly. Unlike perimeter tools, RASP sees inside the application, stopping zero-day threats that traditional security solutions often miss.
Q3. Can DevSecOps and RASP work in cloud-native or hybrid environments?
A3. Yes. Modern DevSecOps and RASP solutions are designed to integrate with cloud, hybrid, and on-premises infrastructures. They protect microservices, APIs, and containerized applications without slowing down deployment pipelines. This makes them suitable for enterprises of all sizes and architectures.
Q4. What are the main benefits of combining DevSecOps with RASP?
A4. Combining these approaches provides end-to-end protection. DevSecOps catches vulnerabilities during development, while RASP blocks live attacks in production. Together, they reduce risk, improve threat visibility, prevent zero-day exploits, and ensure faster, safer software delivery.
Q5. What challenges do enterprises face when implementing DevSecOps and RASP?
Common challenges include integrating with existing CI/CD pipelines, monitoring complex applications, and minimizing false positives. Proper planning, automated policies, and continuous learning help overcome these barriers. When implemented correctly, the combined approach strengthens security without impacting productivity.