The number of healthcare breaches keeps climbing, and attackers are going after high-value PHI. The Change Healthcare attack in 2024 exposed 190 million patient records, many tied to AI-powered documentation and billing workflows. When ambient scribes are not secured, audio capture and transcription become entry points for ransomware, data theft, and catastrophic loss. Securing these workflows is now a strategic requirement, and not just a technical upgrade.
Intellivon has supported healthcare enterprises through this shift. Our ambient scribe deployments operate inside secure data zones with strong encryption, access controls, and governance. We have delivered years of enterprise use without a single security incident or compliance violation. In this blog, we share how we ensure patient data is locked down and regulatory-ready at every step of the ambient scribe workflow.
Why Invest In Securing Patient Data in Ambient Scribe Workflows
HTF Market Intelligence reports that AI-enabled clinical documentation is becoming one of the fastest-growing segments in digital health. The market, valued at just over USD 3 billion today, is forecasted to surge past USD 26 billion, supported by a projected 24 percent annual growth rate.
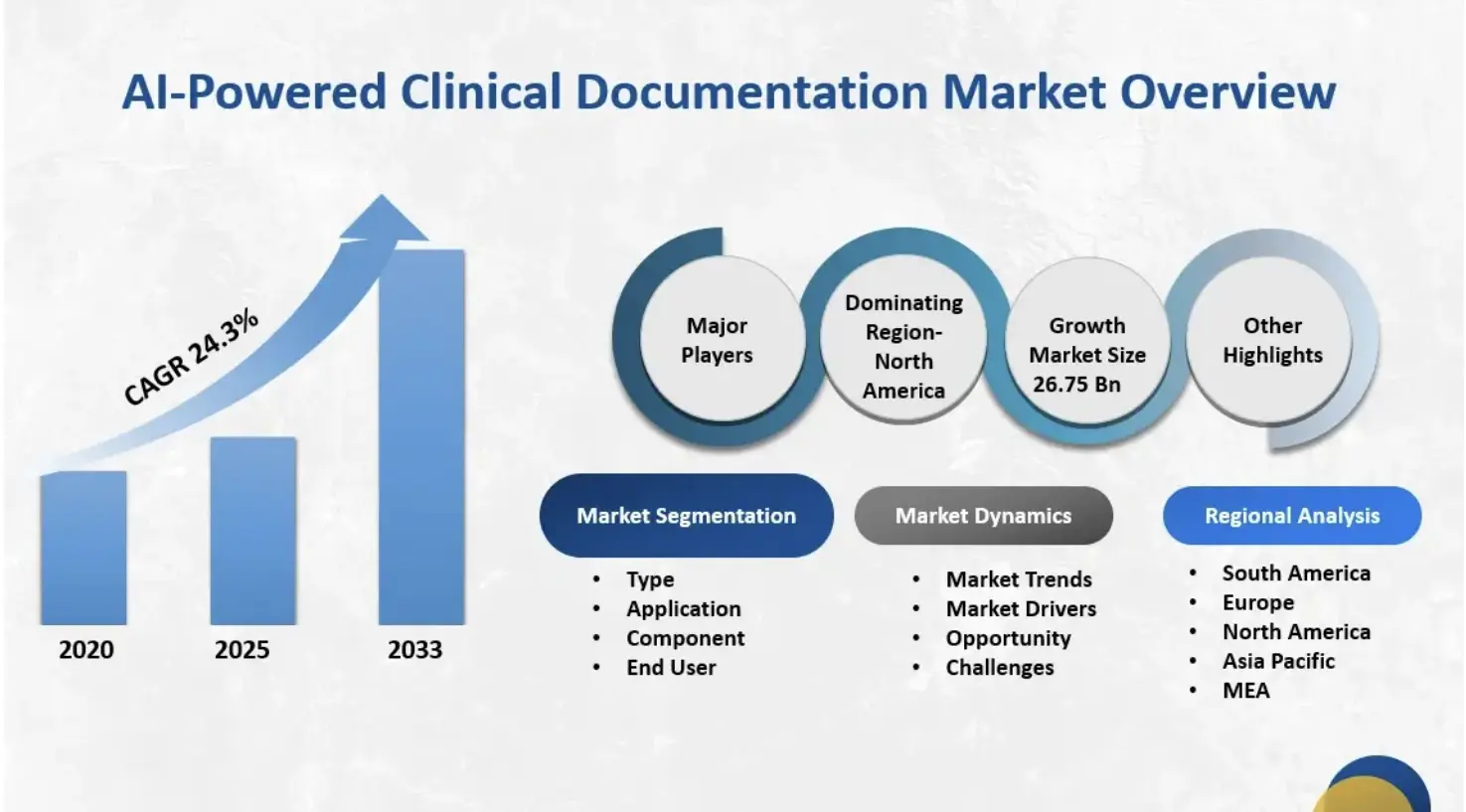
Key Market Insights:
- The ambient scribe category is the fastest-growing segment in clinical AI, generating an estimated $600 million in annual revenue in 2025.
- It exceeds revenue from any other single clinical AI application, growing 2.4x year-over-year.
- The global AI medical scribe software market reached approximately $1.12 billion in 2024.
- Forecasts suggest a compound annual growth rate of about 20.4% through 2033.
Adoption Rates and Penetration
- By the end of 2025, an estimated 30%–60% of healthcare providers will be using ambient scribe tools.
- Within large health systems, adoption is already near 35%.
- Market analysts expect adoption to level off at around 40% over the next three years as early demand stabilizes.
Key Drivers of Enterprise Adoption
- Burnout mitigation remains the primary driver influencing purchasing decisions.
- Additional motivators include improved care quality, revenue optimization, and faster deployment compared to human scribe models.
- Case studies show ambient scribes can save providers more than eight hours per week.
- Some systems report up to 75% lower documentation costs compared to traditional human scribe programs.
- These savings are central to ROI justification for enterprise buyers.
Competitive Landscape and Differentiators
- The U.S. market includes more than 60 vendors.
- Major EHR providers like Nuance (Microsoft), Oracle, and Epic control roughly 33% of the market.
- AI-native companies such as Abridge hold around 30%, while Ambience has close to 13%.
- Growing competition is pushing vendors to expand from “just scribing” to broader clinical and administrative automation.
- Many platforms now bundle documentation, coding support, compliance workflows, and revenue cycle automation.
Investment and Market Maturity
- More than $975 million has been invested in ambient AI scribe companies in 2025.
- These investments show strong confidence in the technology, but also indicate a crowded and rapidly maturing landscape.
- Analysts expect widespread saturation in ambulatory healthcare within the next 24–36 months.
Healthcare enterprises that secure ambient scribe workflows protect patient trust and shield themselves from legal, financial, and reputational damage. Strong safeguards turn automation into a sustainable advantage, not a cybersecurity risk.
What Are Ambient Scribe Workflows?
Ambient scribe workflows capture the clinical conversation in real time and turn it into structured documentation. Instead of typing, clicking through templates, or dictating into a microphone, the clinician speaks naturally with the patient. The system listens, extracts medical context, and prepares a clinical note that can be reviewed and sent into the EHR. The goal is to let the provider focus on the patient, not the screen.
How Ambient Scribing Differs From Traditional Documentation
Traditional documentation relies on typing, manual dictation, or templated note-building. Ambient scribing removes those steps. It works in the background, listening to the encounter and building the note automatically. This creates a smoother visit and less after-hours charting.
| Traditional Documentation Workflows | Ambient Scribe Workflows |
| Providers type notes during or after the visit | Notes generated automatically from the live conversation |
| Dictation requires commands and structured prompts | Natural speech, no special wording required |
| Heavy dependence on templates and point-and-click fields | AI models extract medical context and clinical intent |
| Documentation continues after hours | Notes are often completed in-session |
| High cognitive load | Lower documentation burden |
Example of an Ambient Scribe Workflow
To understand how this works inside an enterprise clinic, consider a standard outpatient visit. The provider consults with the patient, the system listens, and a draft note is ready before the encounter ends. Every step respects clinical control and data security.
Step 1: The encounter begins
The provider logs into the EHR and opens the patient record. The scribe session activates through a secure mobile or desktop interface. The patient is informed that the system will document the visit, and the consultation starts.
Step 2: The system listens
While the provider and patient talk, the platform captures speech through a secure audio stream. There is no need for special phrasing or commands. The system identifies symptoms, medications, history, and relevant clinical details.
Step 3: Draft note creation
Speech is converted into medical language and organized into sections such as HPI, ROS, and Assessment and Plan. The draft is usually ready before the encounter ends.
Step 4: Provider review and sign-off
The clinician reviews the draft, makes small edits, and approves it. The note is then saved directly into the EHR as an official part of the medical record.
Step 5: Data handling and deletion
Once the note is finalized, temporary data is removed according to the health system’s retention and compliance policies.
This workflow removes typing from the visit, supports accurate documentation, and protects valuable clinical time. It also creates a new responsibility: ensuring every layer of the process is secure, compliant, and traceable. That is why healthcare enterprises treat ambient scribe workflows as critical infrastructure, not just convenience software.
How Securing Patient Data in Scribes Saves You $10 Million from Data Breaches
Healthcare breaches are financially severe. The IBM Cost of a Data Breach Report (2024) places the average healthcare incident at roughly $9.77 million in total impact.
That cost includes incident response, legal exposure, operational disruption, regulatory action, and long-term damage to patient trust.
When ambient scribe platforms handle real-time audio and PHI across devices, cloud pipelines, and EHR systems, any gap in the chain can trigger the same level of financial loss.
1. Third-Party Exposure Drives the Largest Failures
Federal breach disclosures recorded in the U.S. Department of Health and Human Services OCR Breach Portal show that many of the largest healthcare incidents now originate from third-party vendors and business associates.
(Primary source: https://ocrportal.hhs.gov/ocr/breach/breach_report.jsf)
The Change Healthcare attack in 2024 exposed 190 million patient records, many tied to AI-powered documentation and billing workflows. Official filings published through the U.S. Securities and Exchange Commission document the scale of the incident and the impact across claims, authorizations, and clinical data.
That single breach exposed data linked to approximately 190 million individuals. The message for ambient workflows is clear: if automated documentation relies on external partners, those partners must be governed to the same security standard as the core health system.
2. Breach Duration Makes Costs Worse
The IBM report also highlights another critical problem: healthcare breaches take longer to identify and contain than almost any other sector, frequently exceeding 200 days before discovery.
If an ambient scribe workflow has an exposed audio stream, unsecured bucket, or permissive API, PHI can leak for months without detection. The longer a breach runs, the more expensive, disruptive, and legally complex the outcome becomes.
3. Turns Small Mistakes Into Huge Losses
Longitudinal breach research from the Ponemon Institute shows that healthcare continues to have the highest cost per exposed record, often exceeding $400+ per record.
Ambient platforms can process thousands of patient encounters per day. If even a fraction of those transcripts are exposed, the financial impact escalates quickly. Short retention windows, audit trails, and secure cloud processing reduce that risk significantly.
When you secure ambient scribe workflows, you are going beyond safeguarding PHI and avoiding the kind of breach that costs nearly $10 million on average and, in extreme cases, harms millions of patients at once.
Where Security Risks Appear in Ambient Scribe Workflows
Ambient scribe systems look simple on the outside. A clinician talks, the AI listens, and a note appears in the EHR. Under the hood, there is a complex chain of data capture, transmission, processing, and storage.
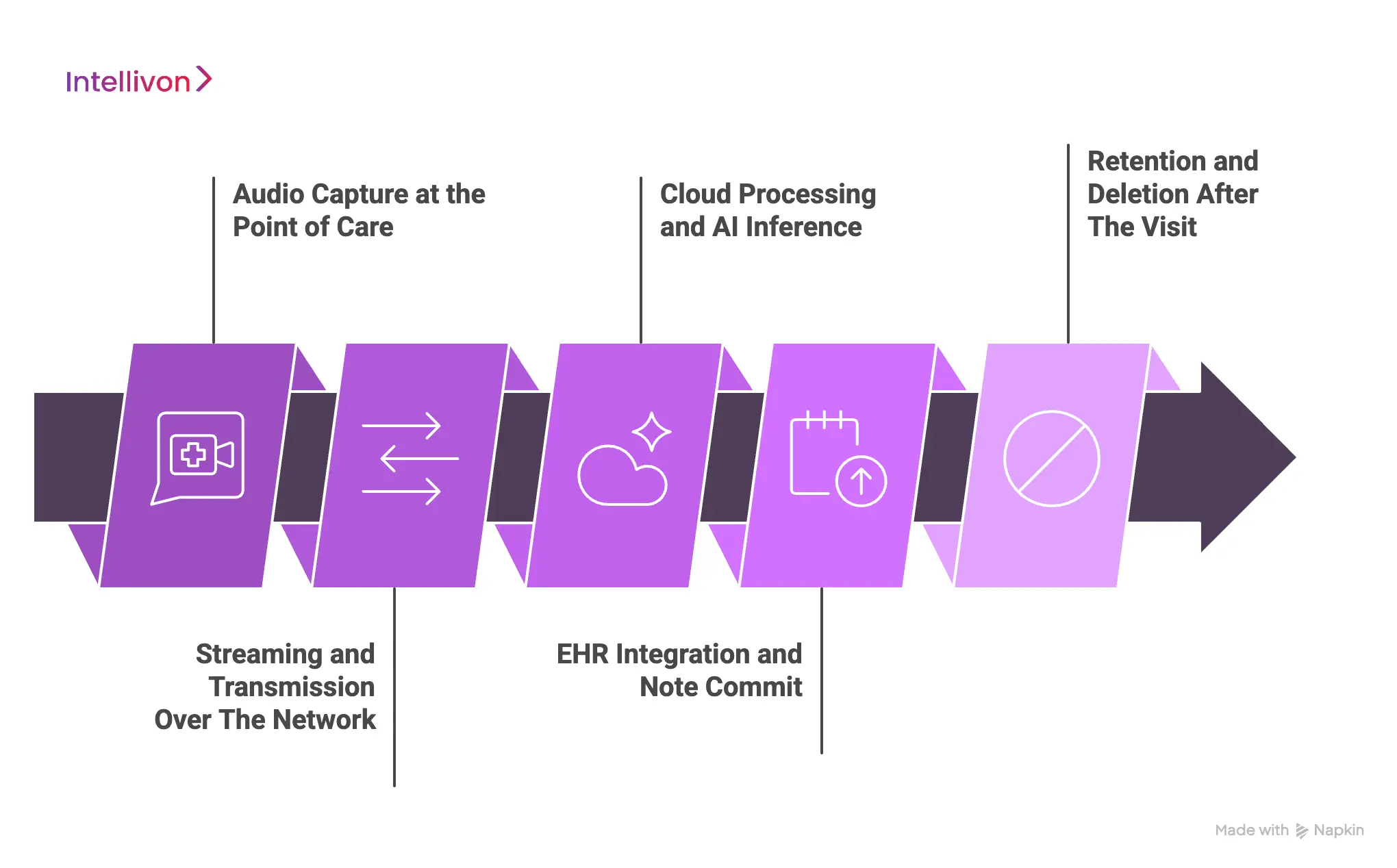
1. Audio Capture at the Point of Care
The workflow starts with a live recording. If the capture app stores audio on a phone or tablet, patient conversations can sit unprotected on local hardware. Lost devices, shared tablets, or personal phones make it risky.
A secure workflow streams audio directly into a controlled environment and verifies each device before recording begins. This prevents PHI from living on hardware that could be lost, borrowed, or accessed by the wrong person.
2. Streaming and Transmission Over the Network
After capture, audio moves across networks for processing. If it travels unencrypted, anyone on the network path could intercept it. Some lower-grade speech tools still send audio through public routes, creating unnecessary exposure.
Healthcare-grade ambient scribes use encrypted channels, private network paths, and updated TLS protocols to remove this risk.
3. Cloud Processing and AI Inference
Once the audio reaches the cloud, it passes through speech recognition and medical language models. This layer holds some of the most sensitive data in the workflow. If the platform mixes PHI with other workloads or allows broad access to model inputs, information can leak.
Enterprise-ready deployments isolate PHI, restrict access, and only keep temporary data for as long as the transcript is being generated. They also avoid using raw clinical conversations to train or improve models without explicit approval.
4. EHR Integration and Note Commit
The draft note eventually reaches the EHR. This sounds straightforward, but if the mapping is wrong, a note can land in the wrong chart. Even a single incorrect entry becomes a privacy event and a clinical safety issue.
Secure workflows authenticate through the health system’s identity controls and require clinician review before the note becomes part of the medical record. Nothing is committed automatically.
5. Retention and Deletion After the Visit
The last step is one many platforms ignore. Once the encounter is documented, temporary audio and transcripts must disappear. If an ambient system keeps raw recordings or stores them in unmanaged buckets, PHI begins to pile up.
The safest deployments use short retention windows, automated deletion routines, and audit logs that prove when data was removed.
Ambient scribing reduces documentation work, but it also expands the flow of PHI across devices, networks, and cloud systems. Without that discipline, a single encounter can become a data breach waiting to happen. Strong design turns ambient scribing from a risk into a reliable clinical tool.
Compliance Rules for Security in Ambient Scribe Workflows
Ambient scribe platforms touch-protect health information from the first word a patient speaks until the note reaches the EHR. Because of that, they must meet the same regulatory standards as any clinical system.
1. HIPAA Security and Privacy Requirements
HIPAA is the baseline. It defines how electronic patient data must be protected while being collected, transmitted, stored, or viewed. A secure ambient workflow encrypts every data stream, controls who can access recordings or transcripts, and keeps detailed records of every interaction with PHI.
If data is stored on unmanaged devices or moves through unsecured channels, the workflow no longer satisfies HIPAA obligations. Compliance is not optional, and health systems expect vendors to meet these standards from day one.
2. HITECH and Breach Notification Rules
HITECH adds enforcement power. Any unauthorized disclosure of clinical conversations or transcripts can trigger mandatory breach reporting. Even a small exposure, such as a lost tablet with cached recordings, falls under these requirements.
When an ambient scribe platform is designed with strong encryption and disciplined deletion policies, the likelihood of mandatory disclosure drops dramatically. The simplest way to avoid the cost and reputation damage of breach reporting is to prevent the breach in the first place.
3. State-Level Privacy Laws
Healthcare is governed at the federal level, but state laws are adding new expectations. California, New York, Colorado, Washington, and others have introduced privacy rules that apply to digital health data, including patient conversations processed by AI.
Many of these laws require greater transparency, more control for patients, and stricter handling of personal information. Ambient scribe platforms used across multiple states must be flexible enough to satisfy different regulatory environments without interrupting the clinical workflow.
4. Business Associate Agreements
Any technology company handling patient information must sign a Business Associate Agreement with the health system. The BAA establishes who owns the data, how long it can be stored, who can access it, and what happens if something goes wrong. Without a BAA, a vendor cannot legally process PHI.
For ambient scribe systems, this agreement is also what prevents vendors from secretly using raw patient conversations to train models or build new products. It is a legal safeguard that protects patients and the organization.
5. Data Integrity and EHR Commit Rules
Once an AI-generated note enters the EHR, it becomes part of the legal medical record. That record must be accurate, traceable, and approved by a licensed clinician. If a system writes directly into the EHR without human review, it exposes the organization to clinical and legal risk.
The safest deployments require a clinician to approve each note before it becomes permanent. That step preserves clinical authority and prevents errors from becoming official documentation.
Compliance is the structure that keeps patient information protected while allowing automation to improve care. When ambient scribe workflows follow HIPAA, HITECH, state regulations, and BAA requirements, and when every note is verified before entering the EHR, the system becomes a trusted part of clinical operations.
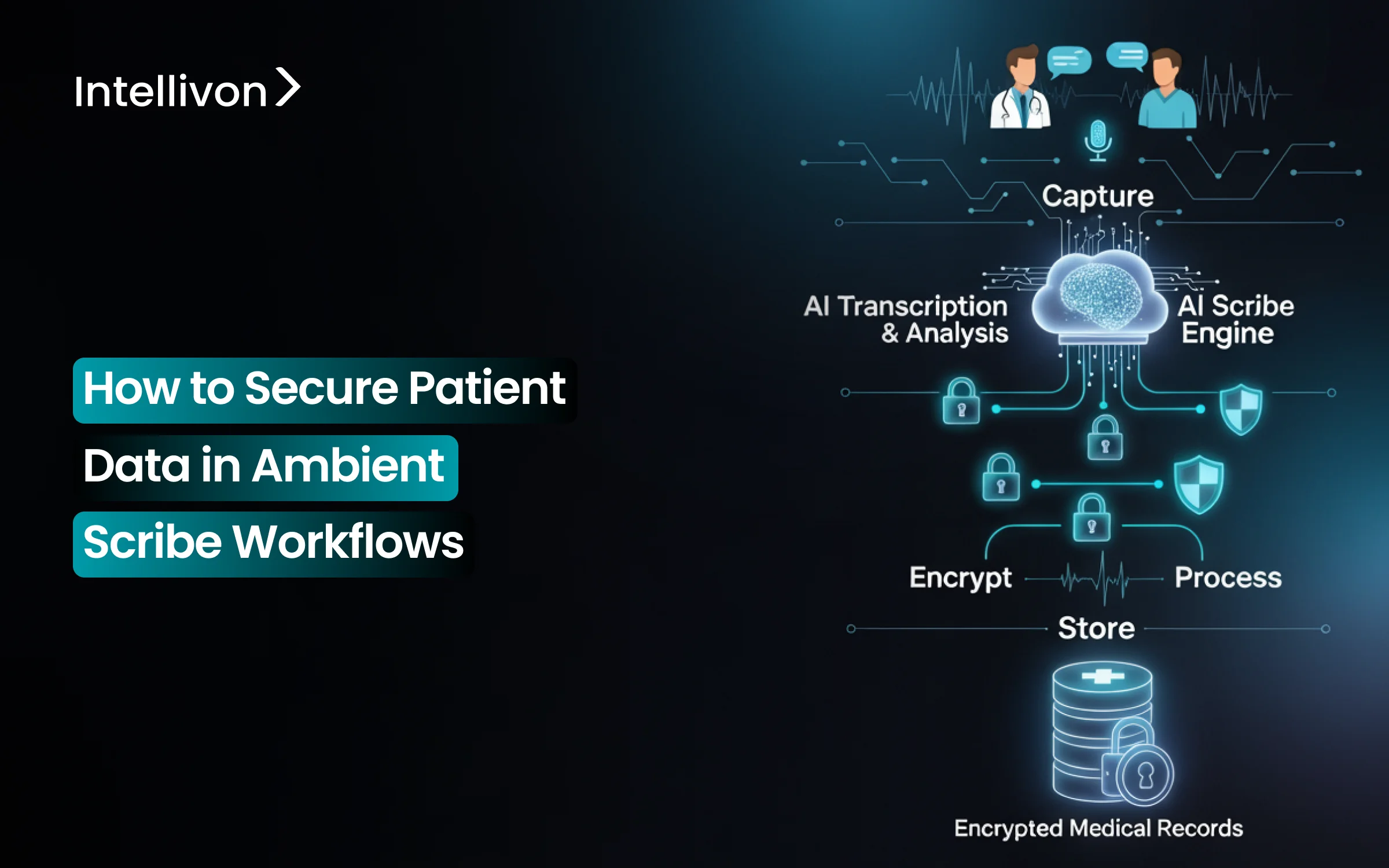
Platform Architecture for Securing Patient Data In Ambient Scribe Workflows
A secure ambient scribe platform is never a single feature. It is a layered architecture that protects PHI from the first audio packet to the final EHR commit. Each layer verifies the one before it, creating a closed system that attackers cannot easily enter or exploit.
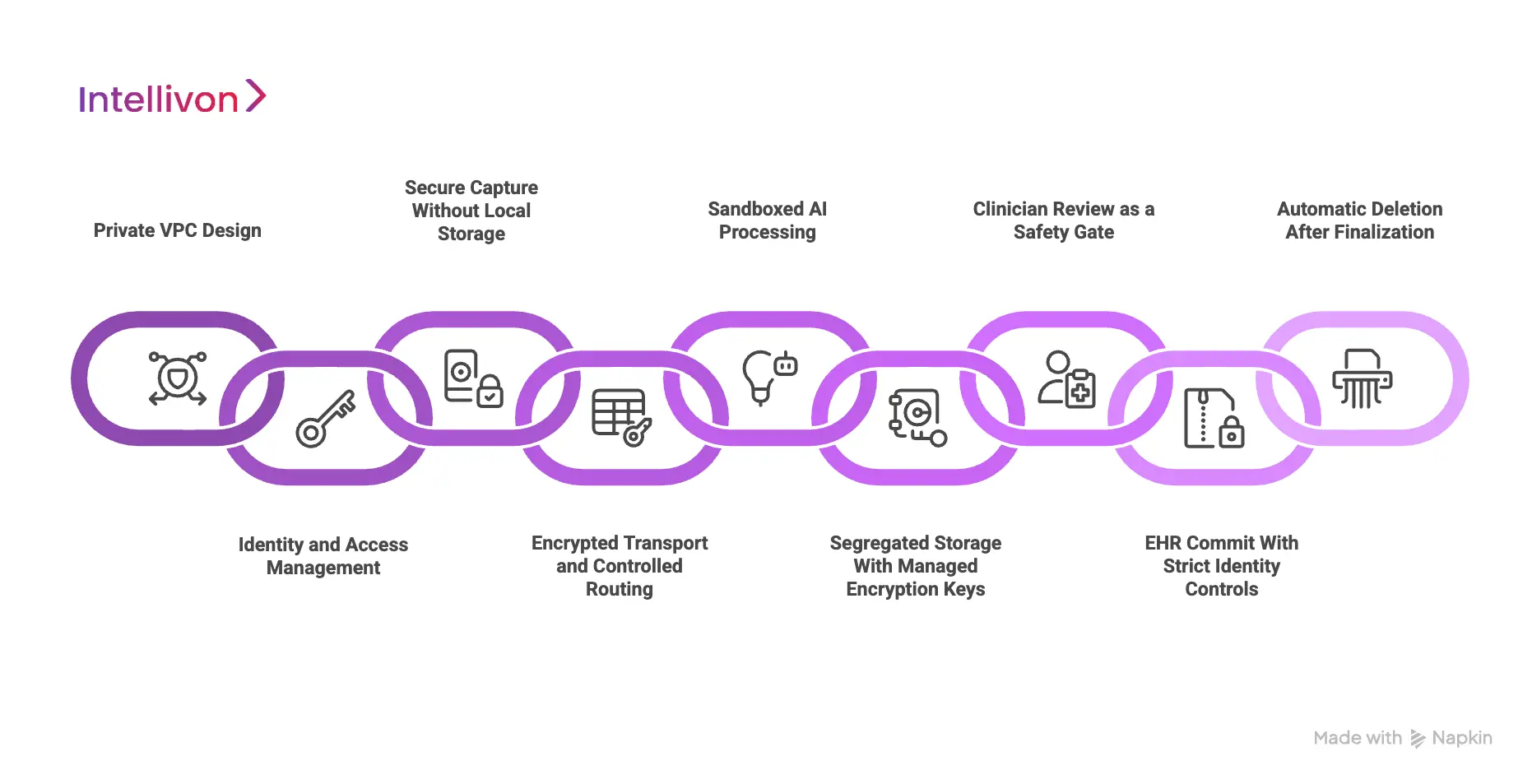
1. Private VPC Design
The platform runs inside a private virtual network, not on public endpoints. All traffic enters through controlled gateways that enforce encrypted connections and strict routing rules.
PHI never travels across the open internet, and sensitive services are inaccessible from outside the network. This creates a contained environment where audio, transcripts, and structured data stay inside a trusted boundary.
2. Identity and Access Management
Every user, device, and backend process must authenticate. Short-lived tokens, role-based permissions, and device validation prevent unknown devices or unapproved users from touching PHI.
Even internal components of the platform cannot overreach. If a device is lost or stolen, its session cannot be reused, and no data can be recovered from it.
3. Secure Capture Without Local Storage
The platform does not store audio on phones, tablets, or clinic workstations. Conversations stream directly into the secure cloud environment. This prevents the common failure mode where raw recordings remain on mobile devices that can be misplaced, borrowed, or accessed by unauthorized staff.
The recording client itself validates its integrity before starting a session and rotates session keys so recordings cannot be replayed.
4. Encrypted Transport and Controlled Routing
During transmission, audio moves through mutually authenticated, encrypted channels. Older or weaker protocols are rejected.
The system ties every stream to a specific encounter and tenant, which prevents mixing or accidental cross-routing of PHI. The encryption protects against interception at the network layer.
5. Sandboxed AI Processing
Speech recognition and language modeling run inside isolated inference environments. These sandboxes separate sensitive workloads so PHI cannot leak into shared compute or analytics systems.
Memory is cleared after each encounter, which prevents data remnants from being reassembled or accessed later. If the health system does not allow training on clinical data, the architecture enforces that restriction technically, not just contractually.
6. Segregated Storage With Managed Encryption Keys
Temporary data lives in encrypted storage that is separated from non-PHI assets. Encryption keys are managed by the cloud provider’s key management system, and keys rotate automatically.
Large health systems can use their own managed keys if they require full custody. This design ensures that even if storage is accessed improperly, data remains unreadable.
7. Clinician Review as a Safety Gate
The platform generates drafts, but clinicians remain in control. Notes do not enter the EHR until a licensed provider signs off.
This protects clinical accuracy and prevents automated errors from becoming part of the legal record. It also ensures that unauthorized users cannot commit documentation without approval.
8. EHR Commit With Strict Identity Controls
When the physician approves a note, it is written into the EHR through standardized interfaces such as SMART and FHIR.
Token exchanges restrict access to a specific encounter, which stops notes from appearing in the wrong chart. The system logs the commit, making it possible to verify when documentation was added and by whom.
9. Automatic Deletion After Finalization
Once documentation is complete, temporary audio and transcripts are removed. Automated deletion jobs clear data on schedule and produce proof of disposal.
The platform does not accumulate recordings, which reduces long-term risk and shrinks the surface area of a potential breach.
A layered architecture like this protects PHI at every stage of the process. For large healthcare enterprises, this is what allows ambient scribing to scale safely, reliably, and compliantly.
Governance and Compliance in Ambient Scribe Workflows
Technology alone cannot secure patient data. Governance determines how the platform behaves in real clinical settings, how data is handled, and who is accountable when something goes wrong. It turns security from a technical feature into an operational standard that can be trusted at enterprise scale.
1. Patient Consent and Transparency
Every ambient session begins with patient consent. The patient must understand that the platform will capture their voice and turn the conversation into documentation.
Consent can be verbal or digital, but it must be clear, recorded, and easy to withdraw. The interface should show that recording is active, and patients should have the right to pause or decline at any point. When consent is transparent, patients see the system as part of their care, not surveillance.
2. Data Retention and Secure Deletion
Ambient systems create temporary audio and transcripts while building the final note. If that data remains in storage, it turns into a security risk over time. Strong governance limits retention windows and deletes temporary data automatically.
Deletion should be verifiable, not just assumed. When the note is complete and approved, the platform should remove what is no longer needed and log the action for compliance teams.
3. Business Associate Agreements With Vendors
Any platform that touches protected health information must operate under a Business Associate Agreement. The BAA clarifies who owns the data, how it can be used, and what happens if a breach occurs. It is also the contract that prevents vendors from training models on clinical conversations without explicit permission.
In mature healthcare organizations, the BAA is not a procurement formality. It is a legal boundary that keeps data within the organization’s control.
4. Continuous Monitoring and Risk Audits
Even the best architecture needs oversight. Audit logs must show who accessed data, when they accessed it, and whether anything changed. Risk teams should be able to trace the lifecycle of each note from recording to deletion.
When monitoring is active, unusual behavior is flagged early, and the organization can respond before a small issue turns into a reportable event. Continuous auditing is practical insurance.
Governance in ambient scribe workflows proves that every encounter is recorded legally, handled securely, and deleted responsibly. When these standards are in place, ambient scribing becomes a safe extension of clinical operations rather than a compliance risk hiding inside a workflow.
How We Secure Patient Data in Ambient Scribe Workflows
At Intellivon, security is built into the ambient scribe platform from the start of the encounter to the moment the note enters the EHR. Every stage has a defined control, so PHI never moves, sits, or is accessed without protection.
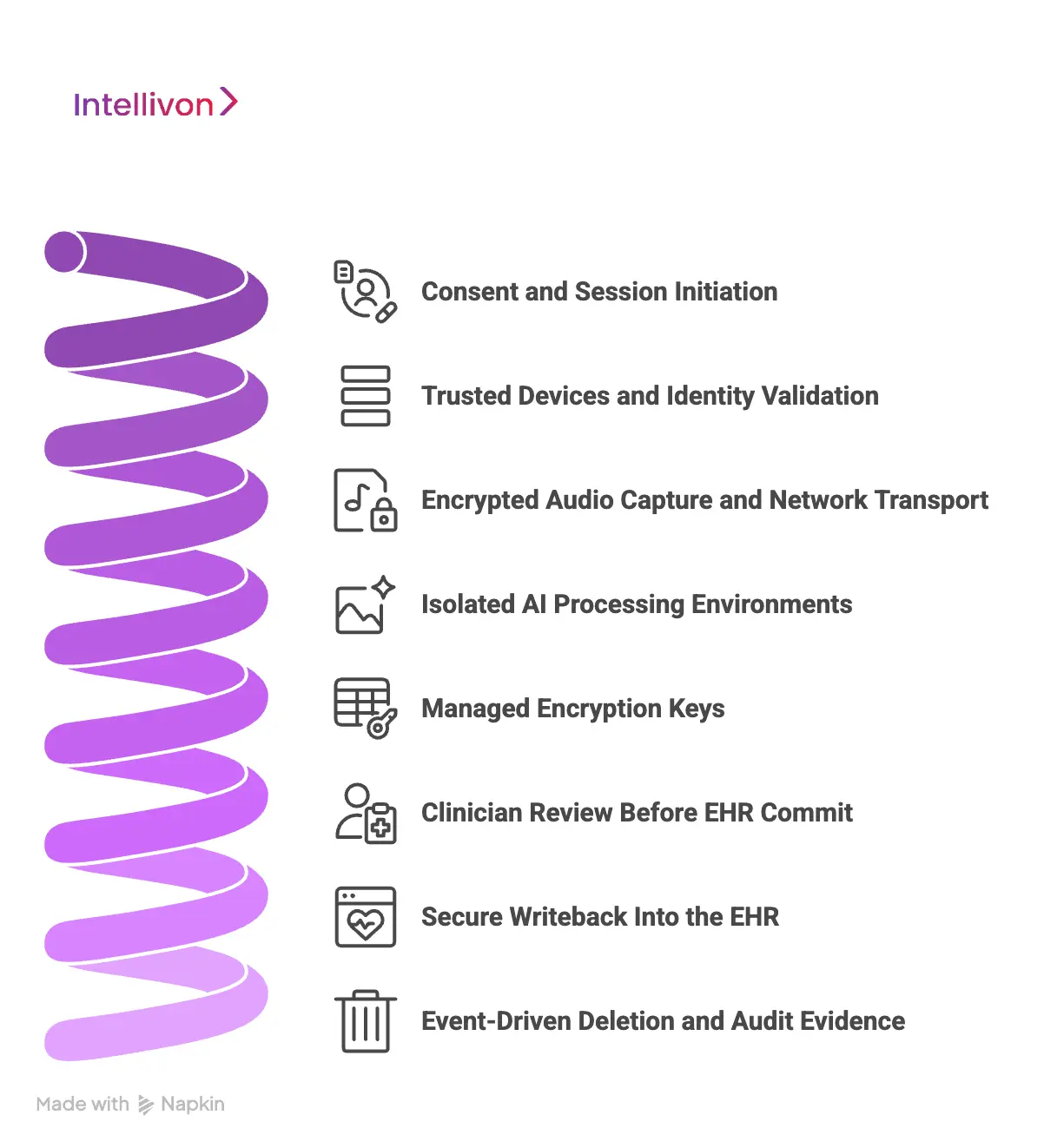
Step 1: Consent and Session Initiation
Every session begins with informed consent. Patients are told that the visit will be recorded for documentation, and the interface shows that recording is active.
Consent is stored as an event inside the audit log, so compliance teams can confirm that the recording was authorized and transparent. Patients can pause or opt out at any time, which keeps trust at the center of the workflow.
Step 2: Trusted Devices and Identity Validation
Only approved devices running verified software can begin a session. We enforce user authentication with short-lived tokens tied to clinical identity.
The platform verifies its integrity before recording starts, which prevents tampering or unauthorized clients from capturing PHI. Even if a device is lost or borrowed, no previous session can be accessed or replayed.
Step 3: Encrypted Audio Capture and Network Transport
Audio is never stored locally. It streams directly into our secure cloud over encrypted channels that meet healthcare security standards.
We use modern TLS protocols and private routing paths, so PHI does not travel across public networks. This prevents interception, replay, or unauthorized listening during transmission.
Step 4: Isolated AI Processing Environments
Speech recognition and medical language models run inside isolated inference environments. Each customer operates in a tenant-scoped sandbox, which prevents data from mixing across organizations.
Memory is cleared after each encounter, and temporary data is removed as soon as the draft note is generated. We do not use raw conversations to train models unless the health organization explicitly authorizes it.
Step 5: Managed Encryption Keys
Some temporary files exist while the note is being created. These files live in encrypted storage that is separated from non-PHI systems.
Encryption keys are managed and rotated automatically through KMS, and organizations with stricter requirements can use their own customer-managed keys. Every access request is logged so administrators can verify who touched data and when.
Step 6: Clinician Review Before EHR Commit
Draft notes appear in a secure workspace tied to the provider’s identity. A clinician reviews, edits, and approves the content before it becomes part of the medical record. Nothing writes to the EHR automatically.
This protects documentation accuracy and keeps clinical authority where it belongs, which is with the provider.
Step 7: Secure Writeback Into the EHR
Once approved, the note enters the EHR through structured FHIR or SMART integrations. Token-based authentication limits access to the correct encounter, and the system validates the mapping before commit.
This prevents wrong-patient documentation, privacy incidents, and legal exposure. Every commit is traceable to a user, a session, and a timestamp.
Step 8: Event-Driven Deletion and Audit Evidence
When a note is finalized, temporary audio and transcripts are deleted on schedule. The platform records proof of disposal, so compliance teams have visibility into what data existed and when it was removed.
Immutable audits track activity across the entire session, and monitoring services alert on anomalies such as unusual access or export patterns.
In the end, this eight-step system keeps PHI inside controlled boundaries and removes it as soon as it’s no longer needed. Intellivon delivers real-time documentation without turning patient conversations into long-term data liabilities.
Overcoming Challenges in Securing Patient Data Ambient Scribe Workflows
Securing ambient scribe workflows is complex. Audio moves through devices, networks, cloud services, and EHR systems while PHI remains active at every stage. One weak link can turn automation into a security liability. These are the challenges healthcare enterprises face when real-time documentation enters the clinical workflow.
1. Device and Network Exposure
Many ambient tools still record audio on mobile devices or transmit data over public networks. If a phone is lost or a stream is intercepted, private conversations can be exposed.
At Intellivon, we eliminate that risk by blocking local storage and routing audio only through encrypted, private channels inside isolated cloud environments. PHI never travels in the open and never sits on unmanaged hardware.
2. Cloud Processing Risks
Cloud processing introduces speed, but it also introduces risk. If workloads are not isolated, PHI can mix with other tenants or leak into analytics systems.
Our platform uses sandboxed inference and short-term memory, wiping data once each note is created. We separate PHI from all non-PHI assets and rotate encryption keys automatically, reducing exposure even if infrastructure is compromised.
3. Wrong-Chart Documentation
Wrong-patient documentation is both a safety issue and a privacy violation. Without strict identity controls, automated systems can misroute notes.
Intellivon stops that failure by requiring clinician approval and validating patient-encounter mapping before writing into the EHR. Each commit is tied to a user, a session, and a timestamp, which makes the process both safe and traceable.
4. Retaining PHI for Too Long
If audio or transcripts linger in storage, they become long-term liabilities. Some vendors keep raw data indefinitely, which makes every additional encounter another point of risk.
Our platform deletes temporary data as soon as the note is finalized. Proof of deletion appears in audit logs, giving compliance teams full visibility instead of vague assurances.
5. Third-Party Vendor Exposure
Many ambient scribes depend on external speech engines or billing partners. Each added vendor becomes an entry point for attackers.
Intellivon keeps speech processing, storage, and EHR integration inside our controlled environment. When a third-party component is required, we broker access through governed interfaces and restrict what data that service can see or store. Health systems stay in control instead of handing PHI to a chain of unknown processors.
When these challenges are addressed at the architecture and governance level, ambient scribing becomes a secure, scalable part of clinical operations instead of a cybersecurity risk.
Real-World Case Studies of Secure Ambient Scribe Deployments
Ambient scribe systems are no longer pilots or experimental tools. Large health systems use them every day, but only after proving that PHI can be captured, processed, and written into the EHR without adding cybersecurity risk. These deployments show how secure architecture makes real-time documentation safe to scale.
1. Mayo Clinic
Mayo Clinic partnered with Nuance to bring ambient documentation into multiple specialties. The priority was protecting patient conversations while delivering real-time notes.
Audio was streamed directly into encrypted channels and was processed inside Microsoft Azure’s HIPAA-compliant cloud. No recordings stayed on phones or tablets, and each transcript was tied to the correct encounter using identity tokens.
After approval, the temporary audio was removed automatically.
Security Measures:
Data remained inside a private cloud environment with strict access controls and full encryption in transit and at rest. Temporary artifacts expired on schedule, and training on clinical conversations required explicit approval.
Result:
Mayo reduced documentation workload, improved physician satisfaction, and reported zero reportable security incidents during live deployment.
2. UCSF Health
UCSF introduced ambient scribing for high-volume clinical settings where providers faced hours of after-visit charting. The platform used encrypted streaming and prevented raw audio from living on clinician devices.
Providers reviewed every draft before EHR commit, and data was deleted once the note was finalized. The workflow protected privacy without slowing care.
Security Measures:
Each session produced a complete audit record showing who accessed PHI, when processing occurred, and when deletion happened. Compliance teams gained full visibility without manual oversight.
Result:
Physicians charted faster, telehealth visits moved more efficiently, and thousands of encounters were processed without privacy violations.
3. Kaiser Permanente
Kaiser deployed ambient scribing across clinics and remote providers. The system blocked all local storage and streamed audio directly into secure cloud services. Temporary data existed only long enough to create the note, then disappeared on schedule. Identity controls ensured only authenticated clinicians could view drafts.
Security Measures:
Kaiser used isolated tenant environments, managed encryption keys, and proof of deletion for every encounter. Audit trails verified every action tied to PHI.
Result:
The organization reduced documentation time and avoided new cybersecurity exposure across a large, distributed clinical workforce.
These systems succeeded because security was designed into the architecture, and not added afterward. Encrypted streaming, isolated cloud processing, strict access controls, and short retention windows made it possible to scale ambient scribing without increasing privacy risk.
Conclusion
Securing patient data in ambient scribe workflows is not optional. It is the only way to deliver real-time documentation without turning clinical conversations into cybersecurity liabilities. When encryption, isolation, access control, and deletion are built into the platform, automation becomes a safe extension of everyday care.
The organizations that approach ambient scribing this way see fewer errors, faster documentation, and stronger compliance. Security turns AI from a risk into a long-term clinical infrastructure.
Secure Your Patient Data In Ambient Scribes With Intellivon
At Intellivon, ambient scribing is engineered for real enterprise environments. We build platforms that remove manual charting without creating new security liabilities for hospitals, payers, or physician groups.
Why Partner With Intellivon?
- Compliance-First Design: Every deployment aligns with HIPAA, HITECH, SOC 2, HITRUST, and major state privacy laws. PHI encryption, identity controls, and immutable logs ensure legal defensibility across regions.
- Cloud-Native Security Architecture Private VPCs, encrypted transport, isolated compute, and short-lived retention eliminate the common failure points seen in consumer-grade speech tools.
- Seamless EHR Integration: We write notes directly into Epic, Cerner, and custom EHRs using FHIR and SMART.
- Clinician-Centered Workflows: Drafts surface in a secure review screen, where providers edit and sign with confidence.
- Enterprise Reliability and Scale: Load balancing, multi-region availability, automated failover, and real-time monitoring keep workloads stable during peak volume.
Book a strategy call with Intellivon to explore how a secure ambient scribe platform can reduce documentation time, improve revenue integrity, and scale safely across your network.
FAQs
Q1. How do ambient scribe systems protect patient data?
A1. Secure platforms encrypt audio during capture and transmission, process PHI inside private cloud environments, and delete temporary data after the note is finalized. Access is identity-controlled and fully audited.
Q2. Can ambient scribes write notes into the wrong patient chart?
A2. Only if the platform lacks identity checks. Enterprise systems require clinicians to review and verify patient-encounter mapping before committing notes to the EHR.
Q3. Do ambient scribes store raw audio recordings?
A3. Best-practice deployments avoid local storage entirely. Audio streams directly into the cloud and is removed after documentation is complete, reducing long-term liability.
Q4. Are ambient scribe platforms HIPAA-compliant?
A4. They must be. Compliance requires encryption, access controls, retention limits, audit logs, and BAAs. If a vendor cannot prove these, the platform is not safe for PHI.
Q5. What security certifications should an ambient scribe platform have?
A5. Look for HIPAA, SOC 2 Type II, HITRUST, and ISO 27001. These confirm that the platform’s controls have been independently tested and validated.