Most COPPA violations in apps come from operational gaps rather than intentional choices. Data moves through kernels, SDKs, cloud services, and vendor tools in ways that are easy to overlook. Additionally, many of these flows start before any consent check.
A large-scale review found that 81.25 % of kids’ Android apps contained trackers that sent information to multiple destinations. This is why parents now demand better transparency through EdTech audits, vendor assessments, and privacy guarantees. Secure data structure is now the standard for gaining acceptance in educational apps.
At Intellivon, we create COPPA-compliant children’s apps that handle sensitive information responsibly from the first design meeting. Every system is designed for environments where regulators, school districts, and parents expect clear details about how data moves, who accesses it, and what controls are in place at every step. In this blog, we explain how we design secure COPPA-ready data flows, organize the surrounding structure, and create the protections that keep learning platforms compliant at scale.
Key Takeaways of the Global EdTech Regulatory Compliance Market
The global EdTech regulatory compliance market is expanding rapidly. It is projected to reach USD 17.7 billion by 2034, up from USD 4.7 billion in 2024, growing at a 14.2% CAGR. North America leads with 42% market share, generating USD 1.9 billion in 2024.
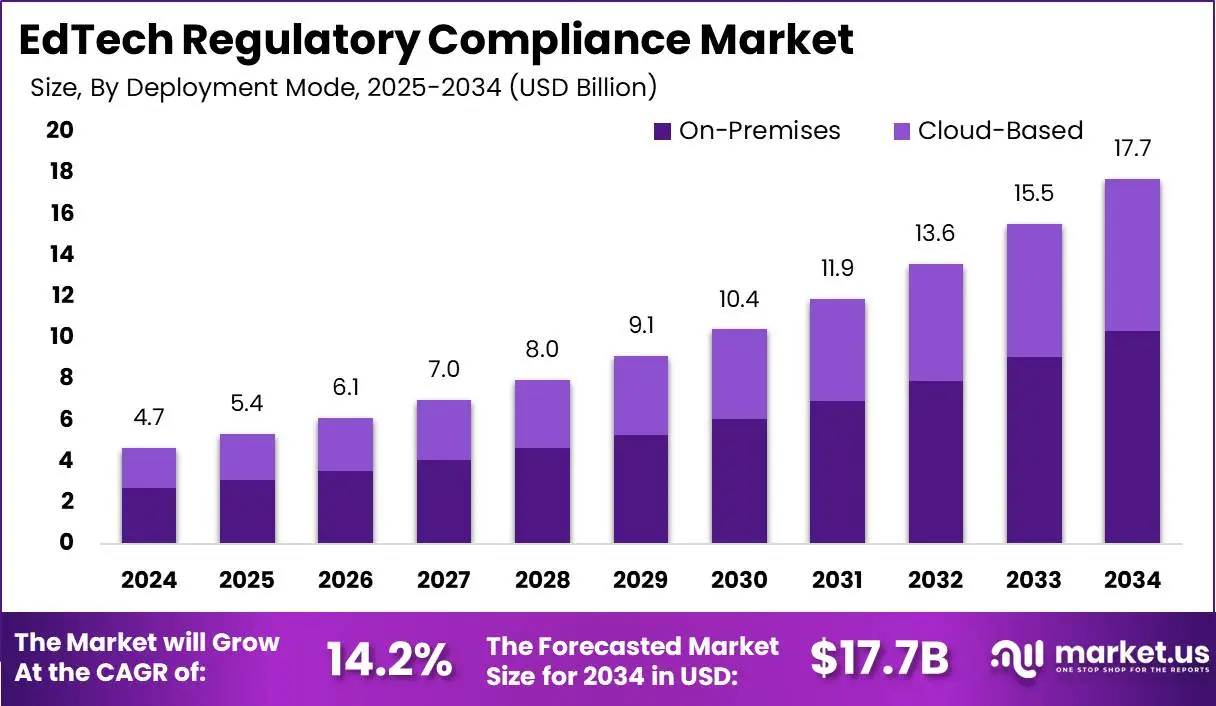
Key Trends
- Broader digital learning adoption is also accelerating, with the U.S. market expected to hit USD 300 billion by 2033. Mobile learning, which is one of the primary channels for kids’ learning apps, will reach USD 110.42 billion by 2025.
- Regulators have increased enforcement. The FTC updated COPPA rules in April 2025 to restrict data retention, require explicit opt-in for targeted ads, and demand higher transparency from vendors.
- Schools and districts are prioritizing platforms that emphasize data minimization, transparency, and parental or institutional consent mechanisms.
- There is a market shift toward privacy-first alternatives and privacy-focused audit tools, with many schools preferring vendors who provide clear data handling and deletion practices.
- Deployment preference remains with on-premises solutions for higher control and security (over 58% of compliance tool deployments in 2024), though cloud adoption is growing due to scalability and accessibility.
Business Impact
- Noncompliance risks are severe: FTC can levy substantial fines for every child’s privacy violation, with recent enforcement actions resulting in multi-million-dollar penalties and suspended contracts.
- Successful platforms build market share by integrating privacy compliance into their core value proposition, fostering trust with both educational buyers and parents.
If more detail or a competitor breakdown is needed, it can be provided for enterprise-level context.
What Are Data Flows in a COPPA Environment?
A COPPA platform depends on clear and predictable movements of information. These pathways show how data enters the system, how it travels between components, and how each step aligns with consent rules. When these movements are not mapped, compliance weakens and trust declines.
1. How Data Enters the System
Data flows in a COPPA platform describe how information enters the system, how it moves between services, and how each step impacts compliance. These pathways help teams track identifiers, manage consent, and prevent uncontrolled data movement across the application ecosystem.
2. Why Precision Matters
COPPA requires precise oversight of every data movement. Platforms must control identifiers, enforce consent-based access, and restrict third-party visibility. Clear pathways reduce the risk of unintended transmissions caused by SDK behaviour or loosely scoped vendor services.
3. How Clear Flows Improve Control
Defined data flows give product, engineering, and security teams control. They clarify which operations rely on consent, which services can access child data, and which outbound connections require monitoring, creating stronger oversight across the entire platform.
Structured data flows create predictability inside a COPPA environment. They support compliance, strengthen operational decision-making, and provide clarity during audits. Most importantly, they reinforce trust among families, districts, and regulators who expect disciplined handling of every piece of information within a learning platform.
Key Principles of Secure Data Flows for COPPA Compliance
Secure data flows rely on simple and predictable rules. These rules shape how information is collected, how it moves through the platform, and how it is protected. When teams design around these principles, the platform becomes easier to manage, easier to audit, and far more reliable in high-trust environments. They also help prevent the silent failures that lead to compliance gaps.
1. Data Minimization
A secure COPPA platform collects only the data it needs. This reduces the number of pathways that information can take. It also limits exposure during the earliest moments of app use. Smaller data footprints give teams more control and make unexpected behaviour easier to spot.
2. Purpose Limitation
Every data point must have a defined purpose. This principle prevents teams from adding optional fields or collecting information because “it might help later.”
Clear purpose rules also make audits smoother. Reviewers can see that each field supports a specific learning or operational need.
3. Isolation of Child Data
Child data requires its own environment. This means separate stores, separate keys, and restricted services.
Isolation prevents a child’s information from mixing with marketing tools or broad analytics systems. It also creates natural barriers that help teams manage risk as the platform grows.
4. Consent as a Gate
Consent must guide how the system behaves. A platform should not process sensitive data until it verifies an adult’s approval.
This gate controls which services can activate and which datasets can load. When consent drives the architecture, unapproved data flows are less likely to appear.
5. Controls Around SDKs and Vendors
SDKs and vendors often create the least visible flows. Strong controls limit what they can see and where they can send data.
Scoped keys, strict allowlists, and monitored API routes help reduce risk. When these controls are in place, external tools operate within clear boundaries.
6. Encryption and Identity Governance
Encryption protects information as it moves through the platform. Identity governance ensures that only approved users and services can access it.
Together, they reduce the impact of errors or misconfigurations. They also create cleaner logs, which help during audits and incident reviews.
7. Predictable Retention and Deletion
COPPA expects clear rules for how long data stays in the system. Automated deletion and regular cleanup prevent old information from building up. These rules help teams avoid unnecessary exposure and simplify compliance with school and parent requests.
These principles form the backbone of a secure COPPA platform. They keep data flows predictable, reduce the noise created by third parties, and make compliance easier to maintain. When they guide system design, the platform becomes more resilient and earns greater trust across families and school districts.
Main Types Of Data Flows in COPPA Kids’ Platforms
Clear data flows define how information is collected, processed, and routed across a children’s platform. They show which events occur before consent, which features depend on verified approval, and which third parties receive specific fields. Teams rely on these pathways to maintain compliance, reduce risk, and demonstrate responsible data handling.
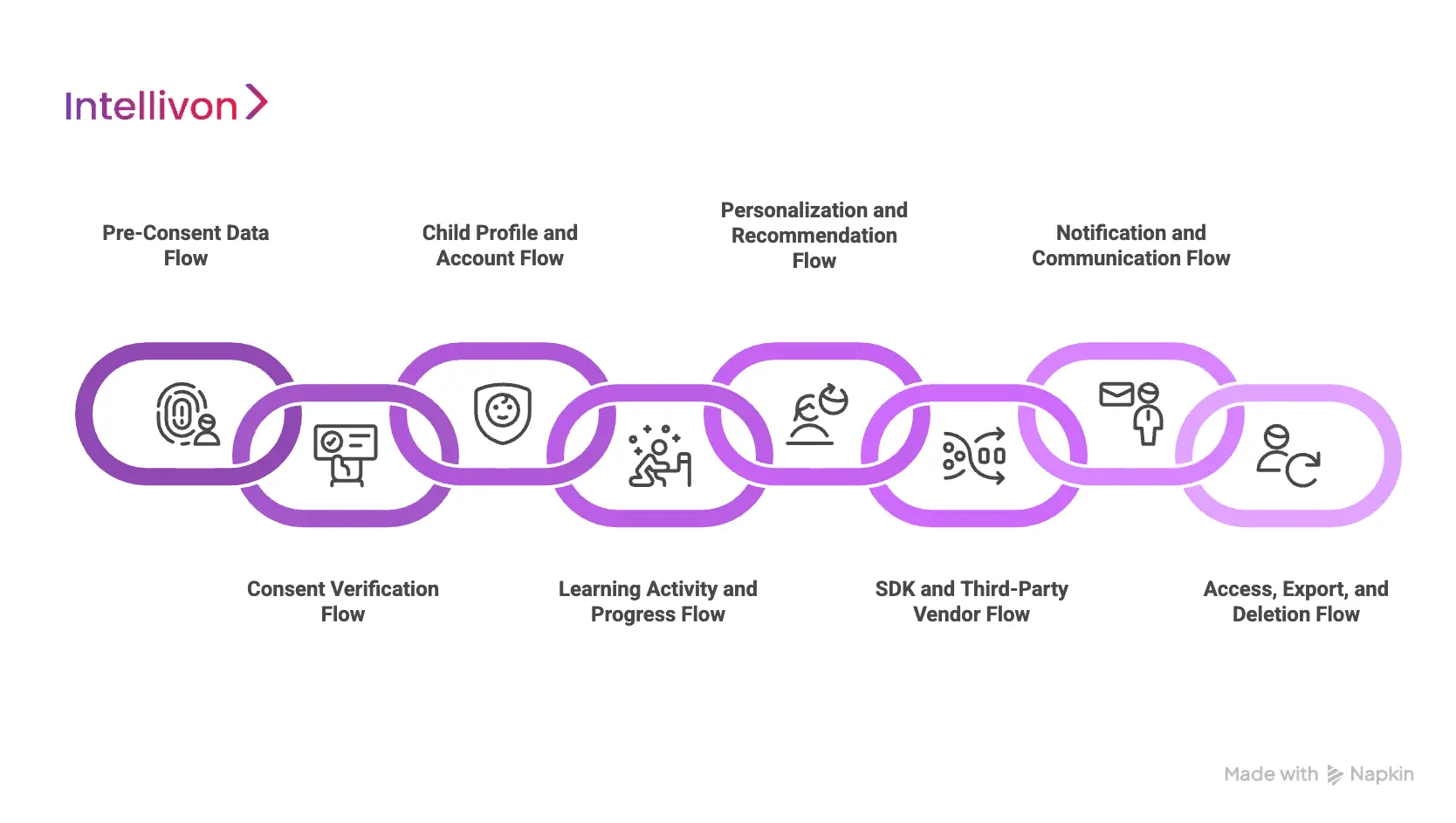
1. Pre-Consent Data Flow
This flow covers everything that happens before the platform confirms a verified parent or guardian. It includes device signals, app-start events, and limited technical identifiers.
These early movements must remain tightly restricted because they occur before any legal approval is granted. When unmanaged, this is where many COPPA violations begin.
2. Consent Verification Flow
This pathway governs how the system checks the adult’s identity and records approval. It includes account lookup, verification methods, validation logic, and event logging.
The flow must be secure, easy to audit, and capable of proving when a parent gave or renewed consent. It also determines which features unlock once consent is confirmed.
3. Child Profile and Account Flow
Once consent is verified, the platform creates a controlled account environment for the child. This flow covers profile creation, role assignment, and access settings. It ensures that learning features activate without exposing unnecessary fields. A well-designed profile flow also prevents child data from leaking into general analytics systems.
4. Learning Activity and Progress Flow
This pathway captures how a child interacts with lessons, quizzes, games, or activities. It records performance, adapts content difficulty, and updates dashboards for teachers or parents.
Strong compartmentalization prevents this data from being used for anything outside the learning experience, which is a core COPPA requirement.
5. Personalization and Recommendation Flow
Personalization must operate within strict boundaries. This flow uses learning patterns, progress signals, and curriculum to adjust the experience.
It must avoid behavioural profiling, advertising logic, or cross-app tracking. When designed properly, personalization improves learning without creating privacy risks.
6. SDK and Third-Party Vendor Flow
This is often the most unpredictable flow in a children’s product. It includes analytics SDKs, crash reporting tools, content services, and cloud vendors.
Each one has its own data expectations. Strong restrictions are needed to ensure they receive only what is essential. This flow must be monitored continuously because silent transmissions often start here.
7. Notification and Communication Flow
Platforms send reminders, updates, and learning summaries. These flows move through email services, push notification systems, and messaging tools.
They must use parent-level data, not child identifiers, and follow strict access roles. Clear routing ensures that messages never expose sensitive information.
8. Access, Export, and Deletion Flow
Parents and schools must be able to view, download, or remove a child’s information. This flow includes permission checks, export jobs, deletion routines, and propagation rules.
It ensures that data is removed from all systems, not just primary storage. Strong lifecycle management helps the platform meet both legal and contractual obligations.
These flows create the core structure of a COPPA-ready platform. They guide how data enters, how it moves, and how it is governed at each step. When companies design with these pathways in mind, they reduce the chance of hidden exposure and create systems that schools, regulators, and parents trust.
Why 72% of embedded SDKs Are High Risk In COPPA-Compliant Apps
Secure data flows shape the foundation of any children’s platform. Independent investigations show that most risks surface long before engineering teams notice unusual behaviour. Many issues begin with SDK activity that runs in the background, silent identifier transmissions during the first few seconds of use, and uncontrolled connections with external services.
These patterns demonstrate why compliance must extend beyond documentation. A COPPA-ready system needs controlled pathways for every event and every movement of data.
1. Hidden SDK Footprints Inside Kids’ Platforms
A national review by Internet Safety Labs revealed how extensive SDK footprints have become in children’s applications. The study found an average of 8.7 SDKs per app, with mandatory school tools reaching 9.3 SDKs.
The same benchmark showed that 72% of embedded SDKs were classified as high or very high risk, and 57% were tied to advertising or monetization systems, even when the apps were approved for school use. The report also noted that 70% of audited apps contained Google SDKs, and 68% sent data to Google during normal use.
These connections create outbound data pathways that internal policies cannot fully manage without structural controls. Only a well-designed architecture can limit the behaviour of these embedded components.
2. Massive Third-Party Data Spread
Network traffic analysis offers a closer look at how much data travels within a single session. A study published by JAMA Network found that 67% of 451 Android apps used by young children transmitted persistent identifiers to external entities
Another investigation, available through PubMed, recorded identifier transmissions ranging from 0 to 614 per session, with certain apps connecting to 399 external domains.
These behaviours reinforce the need for strict pre-consent isolation. Data should remain within a protected environment until the platform confirms verified parental approval.
3. High-Risk App Ecosystems Inside K–12 Schools
School ecosystems make the situation even more complex. According to another Internet Safety Labs benchmark, districts that maintain approved technology lists use an average of 214 apps. Independent reviews highlighted that 67–73% of children’s apps transmitted data to third parties, including advertising networks.
The same research showed that 23% of school-recommended apps displayed ads, and 13% used retargeting, both of which are clear concerns under COPPA.
This environment introduces enterprise-scale risk. Compliance cannot depend on individual app reviews because each product brings its own web of opaque connections and vendor dependencies.
4. Intensified Data-Flow Fragmentation
Children rarely use a single device. A white paper cited by the Future of Privacy Forum notes that 45% of parents report their child uses three or more connected devices, while 41% report one to two devices. These patterns create fragmented identity trails, multiple consent points, and more complex orchestration requirements. A platform needs central identity and consent services to maintain continuity across this landscape.
These findings make one point clear. Most COPPA failures originate from unmanaged or invisible data flows, not deliberate misuse. SDK activity, multi-device behaviour, uncontrolled third-party connections, and sprawling school ecosystems create pathways that teams overlook. A secure platform must map each flow, isolate child-specific data, enforce pre-consent controls, and audit every outbound connection with precision.
Compliance Principles to Apply Across All Data Flows
Strong compliance requires clear rules across every data movement. These rules include data minimization, purpose limitation, consent-driven access, strict vendor controls, role-based permissions, encryption standards, and predictable deletion routines. When enforced consistently, they reduce hidden exposure and help teams maintain a stable COPPA-ready environment.
1. Minimize Data at Every Step
Minimization limits the amount of information the system collects, processes, and stores. Smaller data footprints reduce risk and simplify audits.
This principle applies across all flows, including app launch events, learning progress updates, and communication systems. When minimization is consistent, the platform becomes easier to secure.
2. Align With Clear Purpose
Purpose limitation ensures each data point has a documented reason to exist. This rule helps teams avoid collecting optional fields or enabling features that do not support the learning experience.
Clear purpose mapping also strengthens the platform’s position during district reviews and compliance assessments.
3. Use Consent as a System Control
Consent must influence which services activate and which datasets become available. It cannot remain a simple interface element.
A secure platform blocks sensitive flows until a verified adult approves them. This design prevents information from reaching vendors or internal systems prematurely.
4. Govern Vendors and SDKs With Precision
External tools often create the most unpredictable behaviour. Scoped permissions, strict API rules, and monitored endpoints help keep their activity under control.
When governance is strong, vendors receive only what they need and cannot create shadow data flows in the background.
5. Apply Encryption Throughout the System
Encryption protects data at rest and during transmission. It reduces the impact of errors, misconfigurations, and vendor misuse.
Combined with identity controls, it helps teams maintain clear boundaries around who can access information and how it is processed across services.
6. Limit Access Through Permissions
Role-based access ensures only authorized users and systems can see or modify sensitive information. This principle applies to teachers, administrators, support teams, and internal tools.
When access follows clear rules, the platform becomes easier to monitor and defend during audits.
7. Maintain Predictable Retention and Deletion
Retention schedules and deletion routines help remove data that no longer serves any educational purpose. Automated cleanup and full deletion propagation prevent sensitive information from lingering in secondary systems.
This keeps the platform aligned with COPPA expectations and reduces long-term exposure.
These principles give structure to every data movement inside a COPPA platform. They help teams maintain consistent behaviour across services, prevent hidden pathways, and respond confidently during regulatory reviews. When applied across all flows, they form a strong foundation for privacy, security, and operational trust.
Key Architecture for Secure Data Flows in COPPA Kids’ Platforms
A secure COPPA architecture combines identity controls, gated consent workflows, isolated child-data environments, restricted third-party routing, encrypted communication layers, and predictable lifecycle management. These components create clear pathways that keep information protected from entry to deletion and allow teams to govern every data movement with confidence.
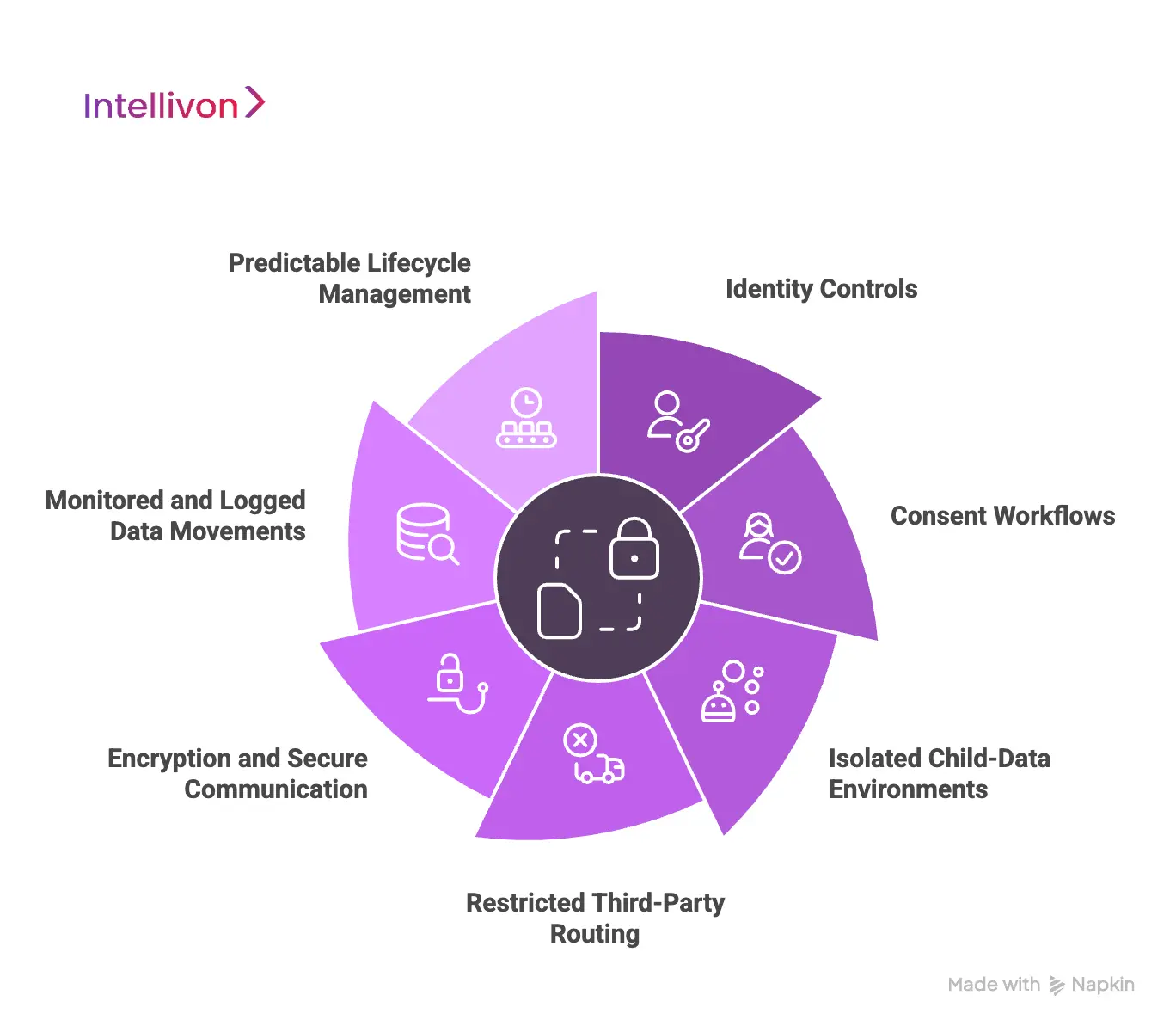
1. Isolated Child-Data Environments
A COPPA platform benefits from an isolated environment that handles all child-specific information. This separation keeps regulated data away from marketing tools, general analytics systems, and optional integrations.
It also reduces the impact of vendor misconfigurations. When data sits in its own environment, teams gain clearer control over how it moves and who can access it.
2. Consent Workflows
Consent must influence the system’s behaviour. A strong architecture blocks sensitive operations until a verified adult approves them. This includes analytics events, profile creation, SDK initialization, and communication features.
The consent check becomes a central gate that decides which flows can continue. This approach prevents early data exposure and reduces the surface area for legal risk.
3. Restricted Third-Party Routing
Third-party tools often introduce unpredictable routes that require strict boundaries. An effective architecture routes vendor traffic through controlled layers rather than letting SDKs communicate freely.
Scoped keys, allowlists, and throttled endpoints restrict what vendors can see. When these controls sit inside the architecture itself, external tools cannot create silent or unintended pathways.
4. Encryption and Secure Communication
Encryption protects data as it moves between services and during storage. Secure communication layers limit interception and prevent unauthorized systems from reading sensitive fields.
When encryption is universal, the platform can operate in school districts, government environments, and high-regulation markets with fewer exceptions. It also improves audit readiness, since encrypted pathways are easier to document.
5. Identity Controls
Identity governance anchors the entire architecture. A central service decides what each user type can access and which flows they can trigger. This includes teachers, parents, administrators, support teams, and automated systems.
Clear identity rules prevent accidental access and create predictable oversight. They also simplify compliance reviews by showing who touched which data and why.
6. Monitored and Logged Data Movements
The platform must log each significant event related to data movement. These logs support audits, help diagnose issues, and provide evidence for investigations.
Monitoring also reveals unusual patterns such as unexpected vendor calls or premature SDK activity. When monitoring is continuous, teams spot issues early and lower the chance of silent breaches.
7. Predictable Lifecycle Mechanisms
Lifecycle rules determine how long data stays in the system and how it is removed. Automated deletion workflows help remove stale information, while propagation logic ensures data disappears from secondary or vendor systems.
Clear lifecycle management shows regulators and districts that the platform respects retention limits and has full control over long-term exposure.
A strong architecture gives a COPPA platform its stability. It creates boundaries that guide how information enters, moves, and leaves the system. With isolation, gating, encryption, identity governance, vendor control, and lifecycle discipline in place, the platform becomes easier to trust and easier to defend during regulatory scrutiny.
Tools and Technologies for Secure COPPA Data Flows
Secure COPPA data flows depend on tools that manage identity, enforce consent gating, monitor SDK activity, encrypt communication, control vendor access, and automate lifecycle operations. These technologies bring structure to the system and help teams track, govern, and validate every data movement with confidence.
1. Identity and Access Governance Platforms
Identity governance tools define who can access child data and which flows they can trigger. Centralized identity services create consistent rules across parent accounts, child profiles, school administrators, and internal teams. This ensures every access point follows the same permissions and prevents accidental cross-environment exposure.
2. Consent Verification Systems
A COPPA-ready platform needs a secure method for capturing and validating parental consent. This includes identity checks, timestamped logs, and renewal workflows.
Consent tools connect directly with core services, allowing the system to block sensitive data movements until approval is confirmed. They also support audits by showing when and how consent was granted.
3. Data Isolation and Segmentation Layers
Isolation tools create dedicated environments for child data. These layers form boundaries that keep child-specific information separate from analytics, marketing systems, and optional vendor services.
Isolation also limits the impact of misconfigurations and gives engineering teams clearer visibility into how data travels through the platform.
4. Encryption and Secure Communication Services
Encryption frameworks protect information as it moves across APIs and between storage systems. They prevent unauthorized access and reduce the impact of network-level risks.
Secure communication layers also help platforms meet district and regulatory expectations, since encrypted flows are easier to document and validate during reviews.
5. SDK and Vendor Governance Tools
Monitoring tools track how SDKs behave inside the application. They identify unusual outbound calls, flag unauthorized endpoints, and enforce scoped permissions.
These tools help prevent silent transmissions that often occur in third-party components. Strong vendor governance also limits the amount of data external services can access.
6. Logging, Monitoring, and Audit Infrastructure
Audit-ready logging gives teams a clear record of data movement. Monitoring tools detect patterns that may indicate misrouting or unauthorized transmission.
Together, these technologies create the visibility required for investigations, district reviews, and periodic compliance assessments. They also help teams catch issues early, before they escalate.
7. Data Lifecycle and Deletion Automation
Lifecycle tools automate retention rules and deletion requests. They help remove older data and propagate deletions across connected systems.
Automated routines prevent partial deletion, which is a common COPPA concern when data sits in secondary stores or vendor services. Consistent lifecycle management reduces long-term exposure.
These technologies form the operational backbone of a secure COPPA environment. They strengthen identity control, reduce vendor risk, protect communication channels, and ensure that each data movement follows the rules. When combined, they create a platform that is easier to manage, easier to audit, and trusted by parents, districts, and regulators.
Common Data Flow Mistakes in COPPA Kids’ Platforms
Most COPPA gaps trace back to premature data transmissions, missing separation between systems, unmanaged vendor behaviour, over-permissioned internal roles, and weak lifecycle rules. Fixing these issues requires stronger architecture, clearer boundaries, and continuous oversight. These are the areas Intellivon focuses on when building compliant platforms.
1. Allowing Data Movement Before Consent
Many platforms transmit identifiers and analytics events during app launch. These early signals often fire before any consent step appears on-screen. It creates a COPPA violation within seconds, long before the parent has the chance to authorize anything.
Intellivon solves this by keeping every sensitive process in a dormant state until the system confirms verified adult approval. SDKs remain inactive, outbound calls stay blocked, and the startup sequence stays minimal and compliant.
2. Mixing Child Data With General Analytics
Teams sometimes send child data through broad analytics pipelines that also handle marketing events and A/B testing. This overlap creates exposure and makes it difficult to remove information during deletion requests, since it spreads across systems that were never designed for regulated data.
Our approach isolates child data into its own environment. Separate stores, restricted keys, and controlled pipelines ensure regulated information never touches open analytics stacks or external marketing tools.
3. Overlooking SDK and Vendor Behaviour
SDKs have their own logic. They initiate network calls, collect device details, or activate telemetry that teams were not fully aware of. These background transmissions account for a significant share of COPPA violations uncovered in third-party audits.
Intellivon addresses this by routing SDK activity through monitored gateways. Permissions are tightly scoped, unnecessary endpoints are blocked, and each outbound call is filtered or logged based on strict rules.
4. Treating Consent as a UI Step
Some products display a consent prompt but continue running features immediately. This disconnect means data flows begin before consent is validated, even when the interface suggests otherwise.
Our platforms embed consent deep into the system architecture. Approval controls which workflows activate, which data sets unlock, and which integrations can run. Until that approval is verified, the rest of the system remains restricted.
5. Granting Broad Internal Access
Teachers, administrators, support teams, and automated services sometimes have more visibility than they require. Broad permissions increase the risk of accidental exposure and complicate investigations, since it becomes unclear who accessed what and when.
Intellivon counters this with strict role-based access rules. Each user type receives only the visibility required for their function, while all privileged actions generate traceable logs.
6. Incomplete Retention and Deletion
Deletion is one of the most overlooked problem areas. Many platforms delete data from the primary database but leave copies in logs, caches, or vendor systems. This partial removal breaks compliance and harms trust with parents and districts.
Our lifecycle engine handles deletion across all storage layers. Once a parent requests removal, the system propagates it across internal services, vendors, backups, and caches to ensure a complete and verified outcome.
7. Limited Monitoring and Missing Audit Trails
Without strong logging, small issues go unnoticed. When an audit begins, teams struggle to explain where data went or which service handled a particular event. Missing audit trails weaken credibility with schools and regulators.
Intellivon strengthens visibility with detailed, continuous monitoring. Every significant data movement is captured, flagged when unusual, and stored in an audit-ready trail that supports investigations and compliance reviews.
These mistakes appear in many children’s platforms, but they can be prevented with careful design and disciplined governance. By aligning data flows with verification rules, isolating sensitive environments, managing SDKs, and enforcing clean lifecycle controls, organisations create platforms that operate with confidence and meet strict COPPA expectations.
How Intellivon Designs COPPA-Secure Data Flows For Kids’ Platforms
A COPPA-ready platform requires more than checklists. It needs an architecture where every movement of information has a purpose, a boundary, and a clear owner. Intellivon follows an eight-step process that brings structure to this environment and gives organisations a predictable, compliant foundation for children’s learning products.
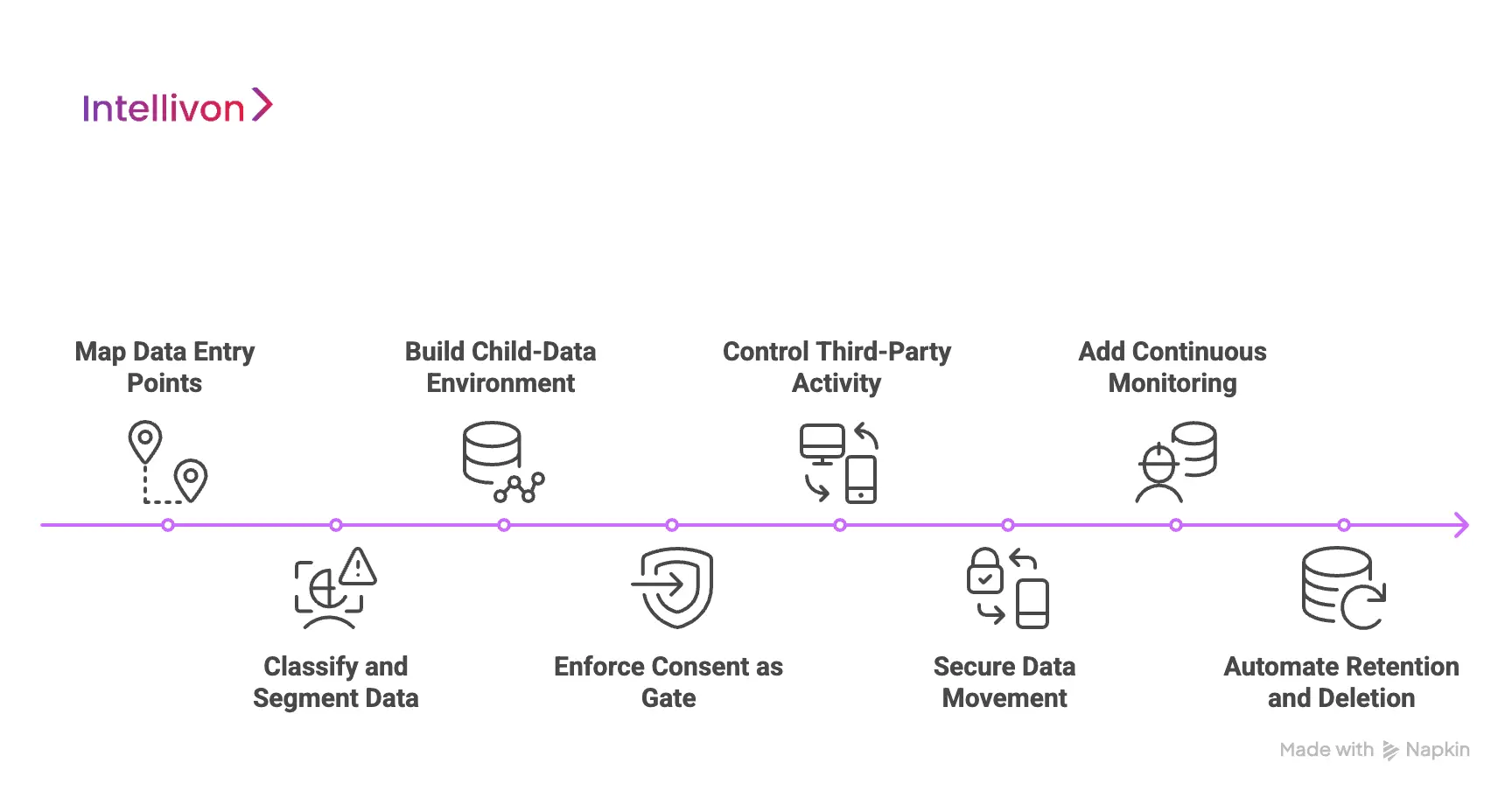
1. Map Every Data Entry Point
An effective data-flow design begins with visibility. Our team identifies every place where information enters the system, including app launch events, sign-up flows, classroom integrations, and backend APIs.
This mapping reveals what arrives before consent, what depends on verification, and which signals require immediate isolation. It creates the baseline that guides all future decisions.
2. Classify and Segment Data
Once the inputs are clear, we classify them based on sensitivity, purpose, and regulatory impact. Child-specific data receives the highest level of protection. Device signals, behaviour events, and profile attributes are kept separate.
This segmentation prevents unintended mixing and helps each service understand what type of information it is allowed to process. It also simplifies audits because the platform can explain exactly how each category is handled.
3. Build Dedicated Child-Data Environment
A secure design requires separation. We create an isolated environment that handles all child-related information. This includes dedicated storage, access rules, network paths, and monitoring.
The environment keeps regulated data away from analytics stacks, marketing systems, and optional integrations. It also reduces risk when vendors are added later, because there is no crossover between regulated and general-purpose flows.
4. Enforce Consent as System Gate
Consent is not a screen. It is a control point that dictates which flows can activate. Our architecture does not process sensitive information until an adult verifies their identity and grants approval.
This step unlocks only the necessary features, and everything else remains dormant. SDKs, analytics, profile creation, communication modules, and integrations stay blocked until consent is confirmed.
5. Control and Monitor Third-Party Activity
Third-party SDKs and vendors often create hidden pathways. We manage them through scoped permissions, monitored gateways, and restricted endpoints. If a vendor attempts to access or transmit information outside approved rules, the system blocks or logs the event.
This level of control prevents background transmissions and ensures vendors operate within the boundaries set by the organisation.
6. Secure Data Movement
Encryption supports every part of the design. Data is protected during transit and at rest, with identity rules controlling which internal users or services interact with it.
These safeguards prevent exposure during network communication, misrouting, or infrastructure changes. Strong governance also ensures keys, access tokens, and service credentials follow strict renewal and rotation practices.
7. Add Continuous Monitoring
A secure platform must be observable. We implement logging systems that capture every significant data movement, including outbound calls, consent checks, profile access, and deletion operations.
These trails support investigations, simplify district reviews, and help teams spot unusual behaviour early. They also show regulators that the platform maintains full visibility into how data travels.
8. Automate Retention and Deletion
Data should not stay longer than needed. We build automated routines that remove old records, purge unused identifiers, and propagate deletion across internal systems and external vendors.
These workflows prevent partial removal, which is a common issue in children’s products. Lifecycle automation keeps long-term exposure low and ensures every deletion request is honoured completely.
This eight-step process gives organisations a stable foundation for COPPA compliance. It brings structure to each flow, reduces reliance on assumptions, and ensures that child data is handled with discipline across the product’s entire lifecycle. With this approach, platforms become more predictable, easier to audit, and far more trustworthy for families and school districts.
Conclusion
Secure data flows define whether a children’s platform can operate responsibly, scale confidently, and meet the expectations of parents, districts, and regulators. They turn compliance into a structural feature rather than an afterthought. When every movement of information is mapped, gated, monitored, and isolated, the product becomes far easier to trust and far harder to misuse. It also becomes simpler to audit, simpler to maintain, and more resilient as new features, vendors, and integration points appear.
Many of the risks that lead to COPPA failures come from silent pathways, background SDK behaviour, and consent gaps that teams do not see until it is too late. A disciplined architecture solves this. It creates clear boundaries around child data and ensures that the platform respects those boundaries through every interaction.
Build COPPA-Secure Data Flows With Intellivon
At Intellivon, we design COPPA-secure data flows as the backbone of kids’ learning platforms. Our architectures map every movement of child data, locks down pre-consent signals, and controls every third-party touchpoint. The result is a platform that stays compliant under real-world traffic, passes district audits with confidence, and scales safely as new features and vendors are added.
Why Partner With Intellivon?
- Consent-First Data Architecture: We treat consent as a system gate, not a screen. Sensitive flows stay blocked until verified parental approval is confirmed, logged, and enforceable across services.
- Child Data Isolation by Design: We create a dedicated child-data environment with separate stores, keys, and pipelines.
- Zero-Tracking Vendor Governance: Our team audits SDK chains, scopes vendor permissions, and routes third-party calls through controlled gateways.
- Secure Flow Mapping and Monitoring: We map every entry, hop, and exit point across the platform.
- Encryption Across Every Pathway: Data is encrypted at rest and in transit, with strict identity governance for services and users.
- Lifecycle and Deletion Automation: We automate retention limits and full deletion propagation across primary systems, logs, caches, and vendors.
- Enterprise Deployment Readiness: Cloud or on-prem setups with hardened environments, access governance, and continuous compliance checks keep data flows stable across districts and regions.
Book a strategy call with Intellivon to design COPPA-secure data flows that protect children’s information, satisfy institutional scrutiny, and support long-term platform growth without privacy tradeoffs.
FAQs
Q1. What are secure data flows in a COPPA platform?
A1. Secure data flows define how a child’s information enters the system, moves between services, and reaches approved destinations. They use consent gates, isolated environments, encryption, and vendor controls to prevent unauthorized data movement during app launch, learning workflows, or third-party activity.
Q2. How does COPPA influence data-flow design in kids’ apps?
A2. COPPA requires platforms to block sensitive data until consent is verified, restrict third-party visibility, limit identifiers, and maintain full audit trails. These rules shape every system pathway, including SDK behaviour, profile creation, tracking signals, and data deletion.
Q3. What causes hidden data leakage in children’s platforms?
A3. Hidden leakage often comes from SDKs that run in the background, unverified consent flows, shared analytics pipelines, and incomplete deletion. These issues create silent transmissions that bypass UI checks and expose regulated data before the platform validates a parent’s identity.
Q4. How can enterprises control third-party SDKs in COPPA environments?
A4. Enterprises control SDKs by routing them through monitored gateways, enforcing scoped permissions, limiting endpoints, and blocking pre-consent activity. This prevents unexpected outbound calls, unauthorized identifier collection, and silent data sharing across external vendors.
Q5. What architecture supports COPPA-secure data flows at scale?
A5. A COPPA-secure architecture uses a separate child-data environment, consent-gated workflows, encrypted communication, identity governance, monitored SDK layers, and automated lifecycle controls. These components create predictable data pathways and help large platforms maintain compliance across districts and regulatory reviews.






