Telehealth platforms do not usually crash at launch. They break later when they grow into actual regulated care systems, and enterprise risk becomes real. What worked during a pilot with 50 users can fall apart fast when handling thousands of patients, with clinicians relying on AI-assisted tools and regulators asking questions. Security holes and compliance issues that seemed manageable suddenly become liabilities that cannot be ignored.
Once operating at scale, compliance and security need to be built into how the platform works. If the system does not control who sees what data, who can approve a prescription, or how clinical decisions get documented, no policy manual or training session can fix it when something goes wrong. So how does a platform actually handle this from day one? By building the rules into the system itself, so compliance happens automatically, and not through checklists or hoping people might follow the right steps.
Intellivon builds platforms for healthcare organizations that do not treat compliance as an add-on. Our proven approach treats regulatory compliance and security controls as part of the architecture itself, so when patient volumes triple or workflows evolve, the platform stays protected and auditable without creating any friction or new risk. This blog walks through how we build such compliance and security-ready telehealth apps from the ground up.
Key Takeaways Of The Telehealth Platforms Market
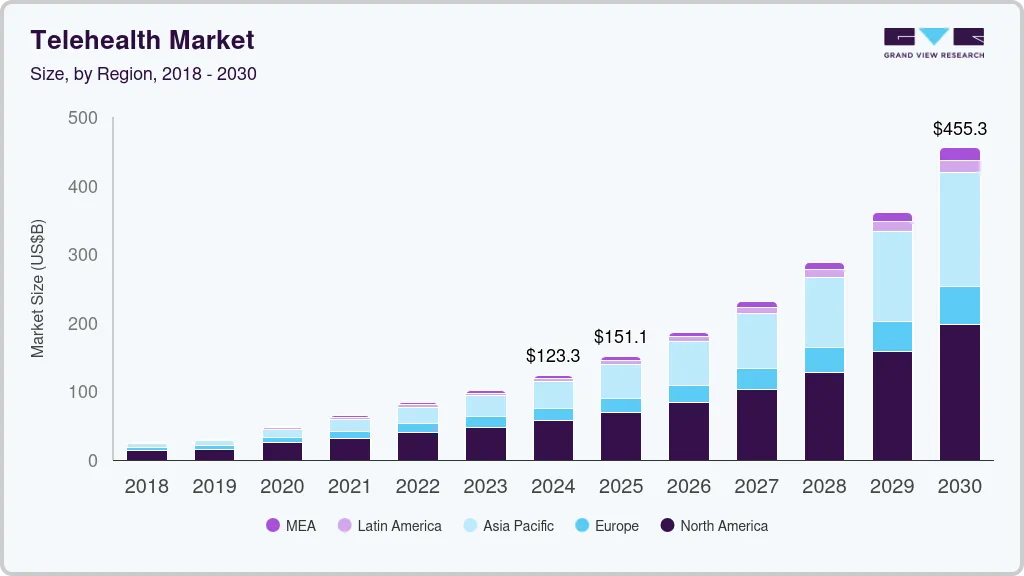
The global telehealth market was valued at approximately USD 123 billion in 2024 and is expected to expand to over USD 455 billion by 2030, growing at a compound annual rate of nearly 25% between 2025 and 2030. This rapid growth is being fueled by widespread adoption of digital health solutions, increasing smartphone penetration, stronger internet infrastructure, sustained investment activity, and ongoing advances in healthcare technology.
Market Insights:
- Telehealth usage remains nearly 40× higher than pre-COVID levels, indicating sustained, not temporary, adoption.
- In 2024, over 70% of physicians used telehealth weekly, nearly three times the 2018 adoption rate.
- On the patient side, more than half of U.S. adults have used telehealth, with close to 90% reporting satisfaction with recent virtual visits.
- Healthcare continues to be the most expensive sector for data breaches, with average incident costs reaching around USD 9.5 million per breach.
- Between 2009 and 2024, U.S. healthcare organizations reported over 6,700 large PHI breaches, impacting roughly 847 million records, far exceeding the U.S. population.
- In 2024 alone, providers disclosed more than 700 large breaches, averaging nearly two incidents per day for the third year in a row.
Taken together, these trends show that telehealth is no longer experimental, and data risk is no longer hypothetical. Usage has settled at scale, while breach frequency remains consistently high.
In this environment, security and compliance cannot sit on top of telehealth systems as policies or checklists. They must be built into the platform itself, shaping how access, data, and responsibility are handled as care delivery continues to expand.
What Are Compliant and Secure Telehealth Platforms?
Compliant and secure telehealth platforms are systems designed to support care delivery without exposing the organization to regulatory, financial, or operational risk. In plain terms, they ensure that telehealth programs operate within the rules as they scale.
A compliant telehealth platform follows healthcare regulations by default. It controls who can access patient data, records every clinical action, and ensures sensitive information is used only for approved purposes. Nothing relies on memory, training, or goodwill. The system enforces the rules.
A secure telehealth platform protects the business as much as it protects patient information. It limits how data moves between systems, prevents unauthorized access, and reduces the chance that routine mistakes become reportable incidents.
Together, compliance and security give leaders confidence. Telehealth can grow without creating audit pressure, eroding trust, or introducing hidden regulatory exposure.
The Real Cost of a Telehealth Data Breach
A telehealth data breach does not end when systems come back online. The real impact appears over time, across budgets, operations, and trust. In healthcare, breach data shows that these incidents create lasting business pressure, not short-term disruption.
1. Regulatory and Legal Fallout
Healthcare breaches remain the most expensive of any industry. According to IBM, the average cost of a healthcare data breach reached nearly USD 9.7 million in 2024, the highest across all sectors.
These costs extend beyond fines. Organizations face audits, legal reviews, corrective action plans, and long remediation cycles. Each step consumes leadership time and increases regulatory scrutiny.
2. Operational Disruption
Breach frequency adds operational strain. From 2009 to 2024, U.S. healthcare organizations reported over 6,700 large breaches, affecting more than 846 million patient records.
Each incident triggers investigations, access reviews, and workflow slowdowns. As a result, care teams lose focus while digital initiatives stall.
3. Financial Impact Beyond Penalties
Direct response costs are only part of the financial burden. Patient notification, monitoring services, and forensic reviews can cost tens of dollars per affected record. These expenses rise quickly for platforms serving large populations.
In extreme cases, breach fallout reaches enterprise scale. One recent healthcare cyberattack is expected to generate over USD 2 billion in total losses once all impacts are counted.
4. Trust and Brand Damage
Trust erosion is harder to quantify, yet deeply damaging. Large breaches increasingly affect millions of individuals in a single incident.
One attack alone exposed data tied to nearly 190 million people, cutting across patients, providers, and payers.
Once confidence drops, adoption slows. Partnerships become harder to close. Regulators and customers alike apply closer scrutiny. The cost of a telehealth data breach compounds over time. It slows execution, drains budgets, and weakens confidence just as platforms attempt to grow.
This is why compliance and security cannot remain reactive. When enforced through platform design, they reduce breach risk before it becomes a measurable business loss.
Why Security and Compliance Break as Telehealth Platforms Scale
Security and compliance issues rarely appear on day one. They surface when telehealth platforms move from limited use to enterprise-wide care delivery. Scale introduces new users, workflows, integrations, and expectations. If the platform is not designed to govern that growth, risk accumulates quietly.
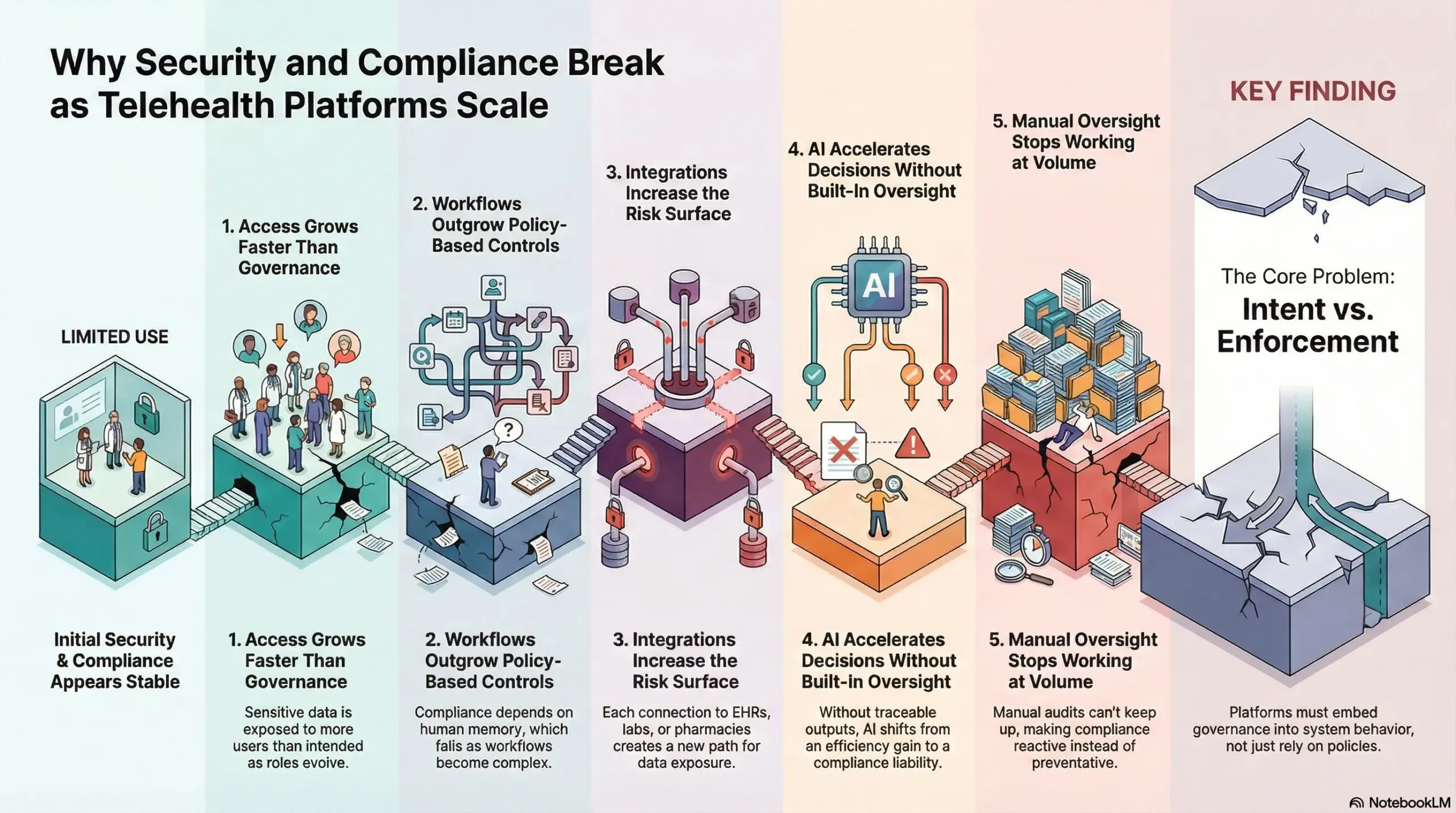
1. Access Grows Faster Than Governance
As telehealth platforms scale, access spreads across clinicians, care coordinators, vendors, and support teams. Roles evolve faster than permissions are reviewed.
Over time, access becomes inconsistent, and sensitive data is exposed to more users than intended. Without system-enforced controls, oversight weakens with every new user added.
2. Workflows Outgrow Policy-Based Controls
Early workflows are simple and easy to monitor. At scale, telehealth workflows span intake, triage, prescribing, follow-ups, and billing. Policies cannot enforce correct sequencing or accountability across these steps.
When the platform does not guide actions, compliance depends on human memory, which eventually fails.
3. Integrations Increase the Risk Surface
Enterprise telehealth platforms depend on integrations. EHRs, labs, pharmacies, devices, and analytics tools all exchange data. Each connection creates a new path for patient information.
If boundaries are unclear, data travels farther than expected, making exposure harder to track and contain.
4. AI Accelerates Decisions Without Built-In Oversight
AI adds speed to triage, documentation, and decision support. However, scale magnifies small gaps in oversight. When outputs are not traceable or reviewable, platforms struggle during audits.
Without clear controls, AI shifts from an efficiency gain to a compliance liability.
5. Manual Oversight Stops Working at Volume
Training, reviews, and periodic audits help early on. However, these methods do not scale with daily transaction volume. As usage grows, teams fall behind, and issues surface only after incidents occur. At that point, compliance becomes reactive instead of preventative.
Security and compliance break at scale when platforms rely on intent rather than enforcement. Growth exposes weaknesses that policies and manual checks cannot fix. Enterprise telehealth platforms must embed governance into system behavior so compliance strengthens as adoption expands, instead of eroding under pressure.
Telehealth Platform Breaches Increase to 82 Reports a Year
Telehealth has scaled faster than the systems designed to govern it. As platforms expand across patients, clinicians, devices, and third-party services, breach reporting has become routine rather than exceptional.
An average of 82 reported breaches per year is not just a security metric. It reflects how exposed telehealth platforms have become as they move deeper into regulated care delivery.
1. Breaches Are Becoming a Pattern
Telehealth breaches are no longer isolated incidents caused by a single misstep. They increasingly stem from always-on access, complex workflows, and growing integration surfaces.
As a result, breaches repeat in similar ways across platforms. When incidents occur this frequently, regulators begin to view them as signs of systemic weakness rather than bad luck.
2. The Real Cost of a Breach Goes Beyond Data
A reported breach triggers far more than patient notifications. It brings audits, legal reviews, internal investigations, and operational disruption.
For telehealth platforms embedded in care delivery, even one incident can slow clinical workflows and erode patient confidence. Over time, repeated breaches create a lasting drag on both operations and trust.
3. Rising Breach Volume Brings Deeper Regulatory Scrutiny
As breach volumes remain elevated, regulatory attention shifts. The focus moves away from how quickly incidents are resolved and toward whether platforms have adequate controls in place.
Regulators increasingly expect platforms to show how access is governed, how data flows are controlled, and how accountability is enforced at the system level.
When telehealth platforms generate dozens of reportable breaches each year, reactive compliance is no longer enough. Security and regulatory controls must shape how the platform operates every day. This is why compliance-first design matters. Platforms that enforce governance through architecture are better equipped to scale telehealth safely, without turning growth into recurring regulatory risk.
Where the Platform Must Enforce Compliance and Security
Once telehealth platforms scale, risk does not sit at the edges anymore. Instead, it moves into everyday system behavior, and this is where architecture matters. Compliance and security only hold when the platform itself enforces how people, data, and decisions move through care delivery. As a result, enforcement has to shift from policy to platform design.
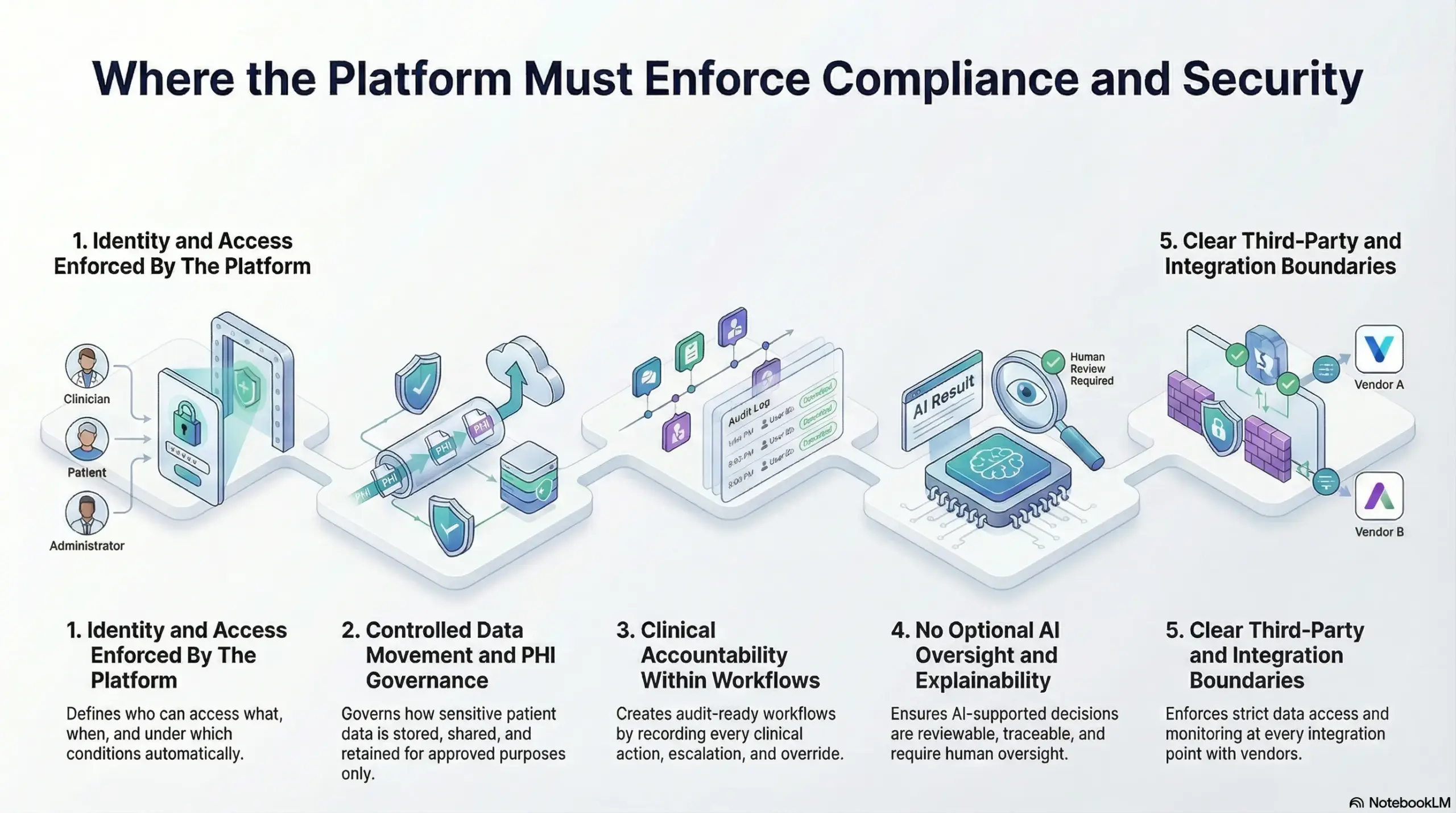
1. Identity and Access Enforced By The Platform
At scale, access control cannot rely on role descriptions or manual reviews. New clinicians join, vendors rotate, and support teams expand. Without system-enforced access rules, permissions spread faster than oversight can keep up.
A compliant platform defines who can access what, when, and under which conditions. Access adjusts automatically as roles change. This prevents overexposure without slowing operations.
2. Controlled Data Movement and PHI Governance
Telehealth platforms move sensitive data constantly. Records flow between visits, devices, analytics tools, and downstream systems. Risk emerges when data travels farther than intended.
The platform must govern how PHI is stored, shared, and retained. Data should only move for approved purposes. Anything else creates silent exposure that surfaces during audits or incidents.
3. Clinical Accountability Within Workflows
Compliance depends on knowing who did what, and why. In telehealth, that trail often spans multiple systems and handoffs.
A secure platform enforces accountability by design. Every clinical action is recorded. Escalations are tracked. Overrides are visible. This creates audit-ready workflows without adding manual burden to care teams.
4. No Optional AI Oversight and Explainability
In addition, AI now supports triage, documentation, and decision support. However, speed without control introduces risk.
The platform must ensure AI outputs are reviewable and traceable. Human oversight should be enforced, not implied. When questions arise, leaders need clear answers about how decisions were supported, not vague model references.
5. Clear Third-Party and Integration Boundaries
Beyond internal systems, enterprise telehealth platforms depend on integrations. EHRs, labs, pharmacies, and devices all play a role. Each connection expands the risk surface.
Strong platforms enforce boundaries at every integration point. Data access is scoped. Behavior is monitored. Vendors only see what they are allowed to see. This prevents one weak link from compromising the entire system.
Compliance and security do not emerge from policies alone. They are the result of consistent system behavior. When platforms enforce identity, data flow, accountability, AI oversight, and integration boundaries by design, risk stays contained as telehealth scales.
Regulatory and Compliance Obligations That Shape Enterprise Telehealth Platform Design
Regulations sit inside telehealth systems and not outside them. Every rule influences how identity, data, workflows, and automation must behave once telehealth operates at enterprise scale. When platforms ignore this reality, compliance becomes fragile and reactive. At the same time, when they accept it, regulation becomes a design input rather than an operational burden.
1. Patient Data Protection and Privacy Regulations
Patient data moves faster and farther in telehealth than in traditional care. Privacy regulations exist to prevent misuse, over-collection, and uncontrolled sharing as digital care scales.
What the platform must enforce
A compliant platform captures consent at the system level and respects revocation without manual intervention. Access is purpose-bound, not role-assumed. Data is stored, transmitted, and retained according to defined rules, not convenience.
Regulatory drivers
In the U.S., HIPAA defines baseline expectations for privacy and security. In Europe and the UK, GDPR and UK GDPR impose stricter requirements around lawful use, minimization, and accountability. Regional data protection laws extend these principles globally, forcing platforms to handle data deliberately rather than broadly.
2. Clinical Governance and Accountability Regulations
Virtual care increases the distance between decisions and decision-makers. Clinical governance rules exist to preserve responsibility, attribution, and patient safety when care is delivered remotely.
What the platform must enforce
Platforms must verify clinician identity and licensure before access is granted. The scope of practice cannot be assumed or overridden quietly. Supervision, escalation, and documentation must follow defined paths.
Every clinical action should leave an immutable audit trail that can be reviewed without reconstruction.
3. Security, Risk, and Enterprise Assurance Standards
Healthcare platforms operate under constant threat. Security standards exist to reduce systemic risk and limit the blast radius when something goes wrong.
What the platform must enforce
Access must follow least-privilege principles by default. Incidents need detection and response workflows that activate automatically, not after discovery. Vendor access and integrations must be constrained and monitored to prevent one weak link from exposing the broader system.
Frameworks influencing platform design
Standards such as SOC 2, ISO 27001, and NIST-aligned controls shape how enterprise platforms prove security maturity. They influence logging, access control, change management, and incident readiness across the platform.
4. AI, Automation, and Decision-Support Governance
AI accelerates care delivery, but it also obscures decision paths if left unchecked. Governance exists to ensure automation supports clinicians rather than replacing accountability.
What the platform must enforce
Platforms should disclose where AI is used and for what purpose. Human oversight must be enforced in workflows, not implied in policy.
Model versions, inputs, and outputs should be traceable. Bias and performance need monitoring as usage scales, not only during deployment.
5. Cross-Border and Jurisdictional Compliance Controls
Telehealth often crosses state, national, and regulatory boundaries. Jurisdictional rules exist to ensure care delivery respects local laws, licensure, and data protection expectations.
What the platform must enforce
Access and workflows must adapt based on location and jurisdiction. At the same time, data residency and localization controls need to be enforced automatically. Region-specific compliance rules should shape what services are available, not rely on staff interpretation.
Enterprise telehealth compliance is a set of constraints that shape how platforms are built and operated. When regulations are treated as architectural inputs, platforms gain predictability. Compliance scales with growth instead of breaking under it. This is the difference between telehealth systems that survive audits and those that struggle to explain themselves.
Core Platform Layers That Enforce Security and Compliance
In enterprise telehealth, compliance cannot be handled by a single control or system. It must be distributed across layers that reinforce each other. Each layer is responsible for enforcing a specific set of rules. Together, they create a platform that remains secure and auditable as complexity increases.
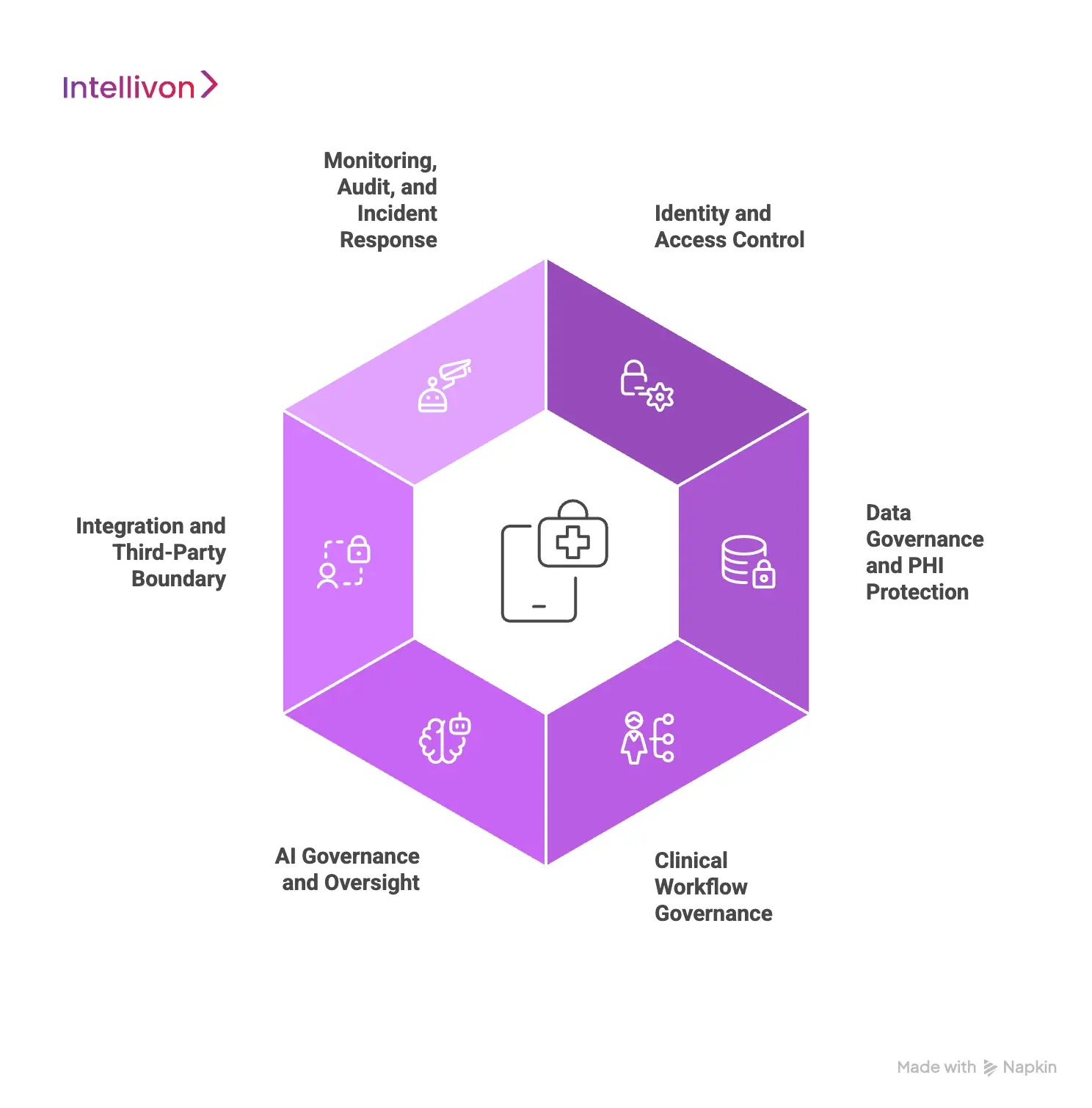
1. Identity and Access Control Layer
This layer governs who can enter the platform and what actions they can perform. It is the foundation of all other controls. At enterprise scale, access changes constantly. Clinicians onboard and offboard. Care teams expand. Vendors and support staff require limited, time-bound access.
This layer enforces verified identity, role-based permissions, and least-privilege access automatically. As roles evolve, permissions adjust in real time, preventing access sprawl without slowing day-to-day operations.
2. Data Governance and PHI Protection Layer
Telehealth platforms move patient data across visits, systems, and services every day. Risk grows when data flows are implicit rather than controlled. This layer governs how PHI is stored, shared, and retained. Data access is purpose-bound and auditable. Encryption is enforced both in transit and at rest. Retention and deletion rules are applied consistently across systems.
As a result, sensitive data stays within defined boundaries, even as the platform integrates with external tools.
3. Clinical Workflow Governance Layer
Compliance depends on accountability across clinical actions. This layer ensures workflows follow approved paths from start to finish.
Every step in care delivery is guided by system logic. Intake, triage, escalation, and follow-ups occur in the right sequence. Actions are logged automatically. Overrides and exceptions are visible and traceable. This reduces ambiguity during audits and removes the need for clinicians to document actions outside the system.
4. AI Governance and Oversight Layer
AI introduces efficiency, but it also increases scrutiny. This layer ensures automation supports care without obscuring responsibility. AI usage is clearly defined within workflows. Human review points are enforced where required. Model versions, inputs, and outputs are traceable over time.
Performance and bias are monitored as usage scales. When questions arise, leaders can explain how AI-supported decisions are made without relying on assumptions.
5. Integration and Third-Party Boundary Layer
Enterprise telehealth platforms depend on external systems. EHRs, labs, pharmacies, devices, and analytics tools all exchange data.
This layer enforces strict boundaries around every integration. Data access is scoped to specific purposes, vendor behavior is monitored continuously, and changes to integrations are controlled and logged. This ensures that one weak or misconfigured connection cannot expose the broader platform.
6. Monitoring, Audit, and Incident Response Layer
Prevention alone is not enough, and platforms must remain observable at all times. This layer provides continuous visibility into system activity. It detects anomalies, supports rapid incident response, and maintains immutable logs. Audit evidence is generated automatically as the platform operates.
As a result, compliance becomes proactive, and investigations do not disrupt ongoing care delivery.
Layered architecture turns compliance into a built-in capability rather than an afterthought. Each layer enforces specific controls, while the full stack provides resilience. This approach allows telehealth platforms to scale, integrate, and innovate without losing security, accountability, or regulatory confidence.
Risk, Policy, and Governance: The Operating Layer Around the Platform
Even the strongest platform architecture does not operate in isolation. In regulated healthcare, compliance begins with governance. Policies, risk assessments, training, and vendor oversight form the operating layer that surrounds the platform and gives technical controls their authority.
How Governance Anchors the Platform
Governance defines what the organization is accountable for and how decisions are made. This is where:
- Risk assessments identify where exposure exists.
- Policies set boundaries for acceptable use.
- Training ensures teams understand those boundaries.
The platform then enforces them consistently, without relying on manual interpretation.
Why This Matters at Enterprise Scale
As telehealth grows, informal controls break down. At the same time, new services launch, vendors are added, and care models evolve.
A clear governance framework keeps security and compliance aligned with business strategy, and not just technical execution.
How Architecture and Governance Work Together
The platform enforces access, data flow, auditability, and oversight. At the same time, governance provides ownership, escalation paths, and evidence for regulators. Together, they create a system where compliance is predictable, reviewable, and resilient under scrutiny.
When governance and platform design work as one, telehealth can scale with confidence. Risk stays managed, accountability stays clear, and compliance supports growth instead of slowing it down.
How We Build Compliance-First Telehealth Platforms
Compliance cannot be “added later” in enterprise telehealth. It has to be designed into the platform from the first workshop and verified before wide rollout. That requires a build approach that treats regulation, security, and clinical accountability as core requirements, not supporting tasks.
Below is the step-by-step process we use to deliver compliance-first telehealth platforms that can scale safely.
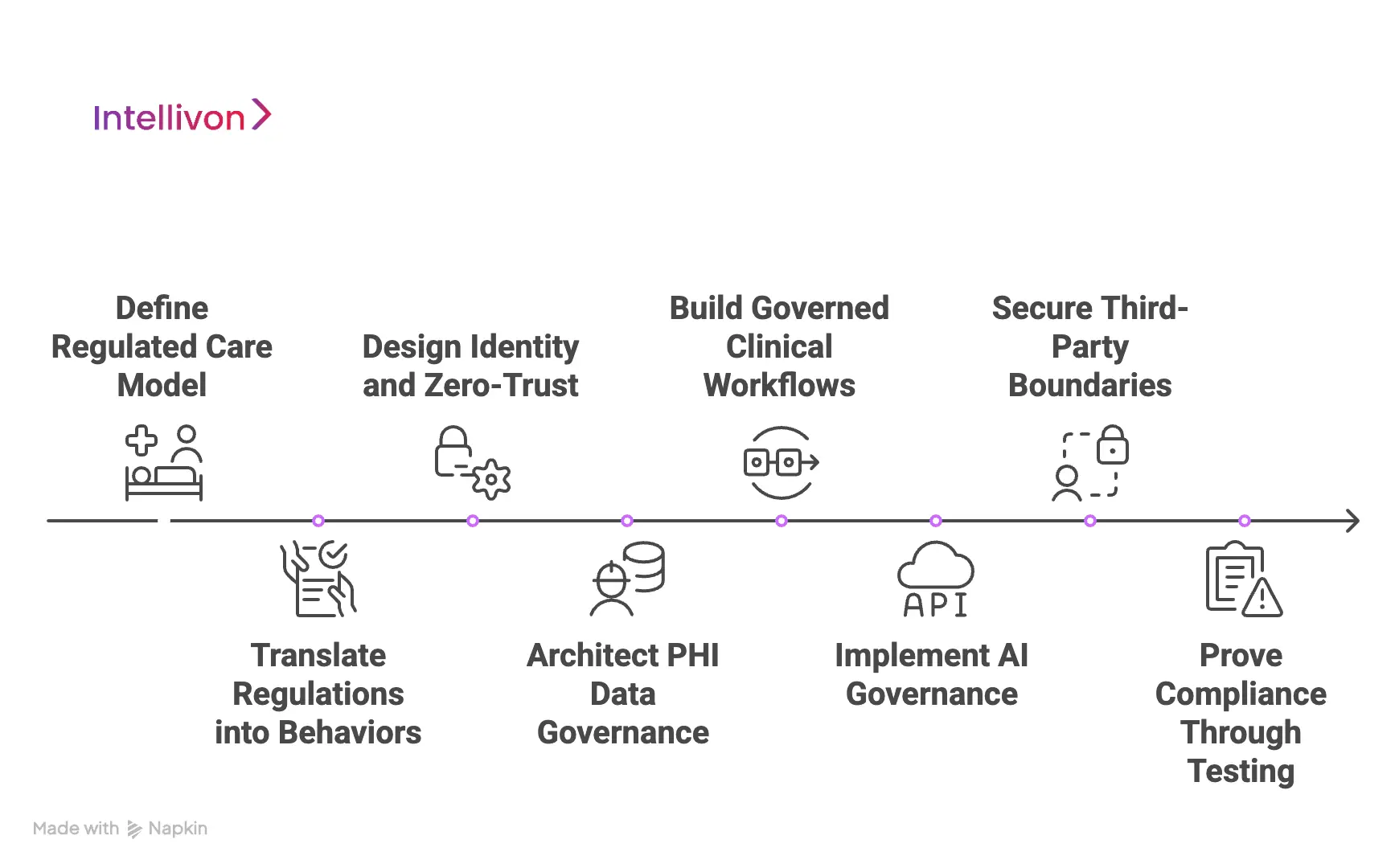
Step 1: Define the Regulated Care Model
We start by clarifying what care the platform will deliver and where regulatory risk concentrates. This includes service lines, patient cohorts, and the clinical actions the platform will enable. In addition, we map the systems that will connect to the platform, including EHRs, labs, pharmacy partners, identity providers, and device ecosystems.
Next, we define what data is handled and where it flows. We classify PHI, determine which workflows create the highest exposure, and document the “points of responsibility” that audits typically test. This step gives the platform a clear risk boundary. It also prevents later scope drift from weakening controls.
Step 2: Translate Regulations Into Platform Behaviors
Most compliance programs stop at policy. We go further and translate requirements into system behavior. The goal of the platform is to enforce the rules automatically, in daily operation, without relying on manual effort.
Here we define concrete enforcement logic, where we specify how consent is captured and revoked and how access is granted, reviewed, and removed. Additionally, we decide what must be logged for audit trails and what cannot be altered. As a result, compliance becomes measurable and testable, not interpretive.
Step 3: Design Identity and Zero-Trust Enforcement
We design access around verified roles, context, and least privilege. At the same time, we also define how the platform supports staff changes, vendor rotation, and multi-site operations without creating permission sprawl.
In parallel, we apply a zero-trust posture. Services do not trust each other implicitly. Integrations authenticate and authorize each interaction. This reduces lateral movement risk and supports clear accountability. It also prepares the platform for enterprise environments where segmentation and remote access controls are expected.
Step 4: Architect PHI Data Governance
Telehealth platforms fail when data governance is vague. We design the PHI layer with clear storage rules, controlled sharing, and purpose-bound access. Encryption is enforced across transport and storage. Retention and deletion logic is applied consistently, so data does not linger outside policy.
We also design for integrity and recovery, with tamper-evident logging supporting non-repudiation and integrity controls reducing silent corruption. This ensures the platform remains reliable during incidents, migrations, or outages.
Step 5: Build Governed Clinical Workflows
Compliance depends on how care flows through the system. We design workflows that preserve accountability from intake through follow-up. Each step has clear ownership, and escalation paths are enforced consistently.
Audit trails are captured automatically as care is delivered. Clinicians do not need to document actions elsewhere. When reviews or audits occur, evidence already exists inside the platforms.
Step 6: Implement AI Governance
AI can improve triage, documentation, and routing. However, it also increases scrutiny. We define where AI is allowed, what it can influence, and where human review must occur. These controls are enforced in workflow design, not left to training.
We then implement traceability where model versions, inputs, and outputs are logged, review actions are recorded, and performance is monitored after deployment, not only during pilots. This gives leadership a clear answer when questions arise about how decisions were supported.
Step 7: Secure Third-Party Boundaries
Enterprise telehealth platforms depend on integrations, and that is why we treat integration as a risk surface. Here, we scope data access to the minimum required, monitor behavior continuously, log changes, and enforce approval paths for updates.
Vendors and partners only see what they are authorized to see. Integrations operate inside segmented trust zones with explicit authentication. This reduces the chance that one misconfigured connection exposes broader PHI access.
Step 8: Prove Compliance Through Testing
Before scaling, we validate enforcement through real scenarios, test access edge cases, workflow exceptions, incident response paths, and audit evidence generation. We also stress test monitoring and alerting so the platform remains observable under volume.
Finally, we prepare audit-ready reporting. Logs, access records, consent trails, and workflow histories are organized so compliance teams can review without reconstruction. This is where “compliance-first” becomes provable. The platform is not only secure, but it is defensible under scrutiny.
Compliance-first telehealth platforms are built through discipline, not promises. Each phase locks controls early, validates them in real workflows, and proves evidence before scale. This approach reduces regulatory exposure while improving operational stability. It also gives leaders the confidence to expand telehealth services without turning growth into risk.
Cost To Build A Compliance-First Telehealth Platform
Ensuring compliance and security in a telehealth platform does not require a single, heavy upfront investment. Most enterprises begin with a focused foundation that enforces identity control, data protection, clinical accountability, and secure integrations.
The platform then evolves as user volume increases, new workflows are introduced, and regulatory exposure expands. This staged approach allows organizations to strengthen compliance early while scaling safely over time.
At Intellivon, we structure cost around regulatory durability and risk containment, not surface-level features. This allows teams to launch securely, pass audits confidently, and avoid expensive rework later.
Estimated Cost Breakdown (USD 50,000–150,000)
| Cost Component | What It Covers (Compliance & Security Focus) | Estimated Range |
|---|---|---|
| Regulatory Discovery & Risk Mapping | Regulatory scope analysis, HIPAA/GDPR mapping, risk boundaries, compliance architecture definition | $5,000 – $10,000 |
| Identity, Consent & Access Governance | User and clinician verification, consent capture, RBAC, least-privilege access, audit logs | $6,000 – $12,000 |
| Clinical Workflow Governance | Intake logic, escalation paths, supervision rules, accountable clinical workflows | $7,000 – $15,000 |
| Data Protection & PHI Governance Layer | Encryption, purpose-bound access, retention rules, tamper-evident logging | $6,000 – $12,000 |
| Prescribing & Regulatory Control Engine | Prescribing rules, contraindication checks, approval logic, audit evidence | $8,000 – $20,000 |
| Integration & Third-Party Security Controls | Secure APIs, scoped data sharing, vendor access boundaries, monitoring | $6,000 – $12,000 |
| Monitoring, Incident Response & Audit Readiness | Activity monitoring, anomaly detection, incident workflows, audit reporting | $5,000 – $10,000 |
| Testing, Validation & Stabilization | Compliance testing, workflow validation, security checks, early stabilization | $4,000 – $7,000 |
Typical Investment Ranges
Compliance-Ready Core Platform: $50,000 – $90,000
Suitable for early telehealth deployments that require strong security, auditability, and regulatory enforcement from day one.
Enterprise-Scale Compliance Platform: $100,000 – $150,000
Designed for higher volumes, prescribing workflows, multiple integrations, and sustained regulatory scrutiny.
Final cost depends on regulatory scope, prescribing complexity, integration depth, and the level of automation required at launch.
What Drives Compliance and Security Cost
Cost is driven by risk exposure and governance, not visual design.
-
Regulatory scope and jurisdictions: More regions and rules increase enforcement complexity.
-
Clinical accountability requirements: Supervision, escalation, and audit depth affect effort.
-
Prescribing and medication governance: Strong controls add cost early but reduce long-term exposure.
-
Integration landscape: Each external system introduces security and audit requirements.
-
Monitoring and automation depth: Proactive controls cost more upfront but prevent expensive incidents.
When built correctly, a compliance-first telehealth platform becomes a risk-reduction asset, not a cost center. Investing early in identity control, data governance, auditability, and secure integrations protects scale, trust, and regulatory confidence. Shortcuts may reduce initial spend, but they almost always increase long-term cost.
Common Compliance and Security Failures in Telehealth Platforms
Many telehealth platforms launch with good intentions and basic safeguards. Problems emerge later, when usage grows, and regulatory expectations tighten. At that point, weaknesses that felt manageable during the early stages become systemic risk.
Below are the most common compliance and security failures we see across telehealth platforms, and how Intellivon addresses them at the platform level.
1. Treating Compliance as Documentation
A common failure is relying on policies, SOPs, and training to manage compliance. While these are necessary, they do not control what actually happens inside the platform. As workflows expand, teams interpret rules differently, and enforcement becomes inconsistent.
At Intellivon, we design platforms where compliance is enforced through system behavior. Access rules, consent handling, audit logging, and escalation paths are built into workflows. This removes ambiguity and ensures the platform operates the same way every day, regardless of scale.
2. Overexposed Access Due to Sprawl
As telehealth platforms grow, access often spreads faster than oversight. Clinicians change roles, vendors rotate, and support teams gain broad permissions to “keep things moving.” Over time, sensitive data becomes accessible to more users than intended.
Intellivon addresses this by enforcing identity-centric, least-privilege access by design. Permissions adjust automatically as roles change, and access reviews are supported by real usage data, not assumptions. This keeps exposure controlled without slowing operations.
3. Uncontrolled Data Movement Across Systems
Many platforms focus on securing databases but overlook how data moves between services, integrations, and third parties. This creates silent exposure. PHI travels farther than expected, making audits and incident response difficult.
We build explicit data governance into the platform. Data access is purpose-bound, monitored, and auditable. Integrations operate within defined boundaries. This ensures sensitive information only moves where it is allowed, and always with traceability.
4. Clinical Workflows Without Clear Accountability
In virtual care, responsibility can blur across intake tools, clinicians, and automated systems. When something goes wrong, teams struggle to reconstruct who acted and why. This weakens audit readiness and increases regulatory risk.
Intellivon designs governed clinical workflows with accountability built in. Every action is logged automatically, escalations follow defined paths, and overrides are visible. This creates audit-ready care delivery without adding documentation burden to clinicians.
5. AI Used Without Oversight or Explainability
AI is often introduced to improve efficiency, but without clear governance. When outputs cannot be traced or reviewed, platforms struggle during audits and reviews. Over time, AI becomes a compliance liability rather than an advantage.
Our approach embeds AI governance directly into workflows, where AI usage is disclosed, human review points are enforced, and model versions, inputs, and outputs are traceable. This ensures AI supports decisions without obscuring responsibility.
6. Weak Integration and Vendor Controls
Telehealth platforms depend on external systems. When integrations are treated as extensions of the platform rather than controlled boundaries, a single misconfigured vendor connection can expose large volumes of data.
Intellivon enforces strict integration boundaries, where vendor access is scoped and monitored, and changes are controlled and logged. Each integration operates within segmented trust zones, reducing blast radius if issues occur.
7. Reactive Incident Response and Audit Preparation
Some platforms only think about audits and incidents after something goes wrong. At that point, teams scramble to collect logs, reconstruct timelines, and explain decisions. This reactive posture increases stress and regulatory scrutiny.
We design platforms to be audit-ready by default. Monitoring, logging, and reporting are continuous, and evidence is generated as the platform operates. When reviews or incidents occur, information is already available.
Most compliance and security failures in telehealth are predictable. Intellivon addresses these failures by engineering compliance and security into the platform itself. This approach reduces risk, supports scale, and gives leaders confidence that growth will not come at the cost of trust or regulatory stability.
Conclusion
Compliance and security are no longer secondary concerns in telehealth. They determine whether a platform can scale, earn trust, and survive regulatory scrutiny as demand grows. The difference between fragile systems and durable platforms lies in how deeply governance, enforcement, and accountability are embedded into everyday operations. When compliance is treated as architecture rather than paperwork, telehealth becomes predictable, auditable, and resilient.
At Intellivon, we build compliance-first telehealth platforms that support growth instead of slowing it down. Our approach helps enterprises launch confidently, scale responsibly, and operate with long-term regulatory certainty. If you are planning your next telehealth platform, this foundation matters.
Build a Compliance-Enforced Telehealth Platform With Intellivon
At Intellivon, we build compliance-enforced telehealth platforms as enterprise operating systems, not feature-driven virtual care tools. Our platforms are designed to govern how patients access care, how clinicians make and document decisions, and how security and accountability are maintained across regulated workflows.
Each solution is engineered for healthcare organizations operating at scale. Platforms are architecture-first and compliance-led, integrating cleanly with EHRs, identity frameworks, pharmacy networks, analytics systems, and enterprise security controls. As platforms expand across service lines, geographies, and user volumes, regulatory enforcement, data integrity, and operational control remain intact.
Why Partner With Intellivon?
- Compliance-first platform architecture aligned with enterprise risk, governance, and audit expectations
- Deep interoperability expertise across EHRs, pharmacy ecosystems, identity platforms, analytics, and security stacks
- Security and compliance enforced by design, supporting regulatory readiness and controlled access at scale
- AI-assisted orchestration that improves intake, triage, and operations without removing clinical accountability
- Proven enterprise delivery model with phased rollout, validation milestones, and predictable scale
Talk to Intellivon’s healthcare platform architects to explore how a compliance-enforced telehealth platform can integrate into your ecosystem, protect regulatory integrity, and support sustainable digital care growth with confidence.
FAQs
Q1. What makes a telehealth platform compliant at enterprise scale?
A1. A telehealth platform is compliant at enterprise scale when compliance is enforced by system design, not policies alone. This includes role-based access, governed data movement, audit-ready workflows, and traceable clinical accountability built directly into the platform architecture.
Q2. Why do telehealth platforms fail compliance audits as they scale?
A2. Most platforms fail audits because they were designed for pilots, not sustained growth. As users, integrations, and workflows expand, manual controls break down. Gaps appear in access governance, data traceability, and clinical accountability, creating regulatory exposure.
Q3. How is compliance different for DTC telehealth platforms?
A3. DTC telehealth platforms face additional compliance pressure due to online prescribing, subscription billing, pharmacy fulfillment, and consumer data handling. These models require stricter enforcement of consent, clinician oversight, prescribing rules, and audit trails to remain compliant as volumes grow.
Q4. Can AI be used safely in compliant telehealth platforms?
A4. Yes, when AI is governed properly. Safe use requires disclosure of AI involvement, enforced human review where needed, model traceability, and ongoing performance monitoring. Without these controls, AI becomes a compliance risk rather than an efficiency gain.
Q5. How do enterprises evaluate whether a telehealth platform is truly compliance-first?
A5. Enterprises should assess whether compliance is enforced by the platform itself. Key indicators include automated access control, purpose-bound data governance, immutable audit logs, controlled integrations, and evidence-ready reporting that supports audits without reconstruction.