Nothing erodes trust in a healthcare platform faster than a PHI leak. In large organizations, there is no room for mistakes. This is because once patient records, clinical notes, or test results slip through the cracks, things escalate quickly, and enterprises face risks they did not expect.
Nonetheless, this type of risk tends to go unnoticed. As healthcare technology within an enterprise keeps expanding, like EHRs, third-party apps, cloud systems, and AI tools, every new addition is a chance for a possible future data leak. That is why PHI-protected healthcare platforms make a huge difference. Within these platforms, protection is designed into the platform early, which means the right people see the right data at the right time, permissions stay tightly governed, and data movement remains fully traceable.
Intellivon works with large healthcare groups that cannot afford untimely risks. We create healthcare platforms for them, where PHI security is built in from the beginning. Further, we strengthen these platforms through sound engineering and maintain them as the system grows across new regions, partners, and complex care settings. In this blog, we break down how we design and build PHI-secure healthcare platforms that stay reliable as enterprise ecosystems grow.
Why Enterprises Need PHI-Secure Healthcare Platforms
Enterprises today need PHI secure healthcare platforms to protect sensitive patient data and meet strict rules such as HIPAA. At the same time, these platforms support day-to-day digital operations across the care ecosystem.
Strong PHI protection helps reduce breach risk, which continues to cost the healthcare industry billions each year. It also builds the trust that providers, partners, and patients expect from modern healthcare systems.
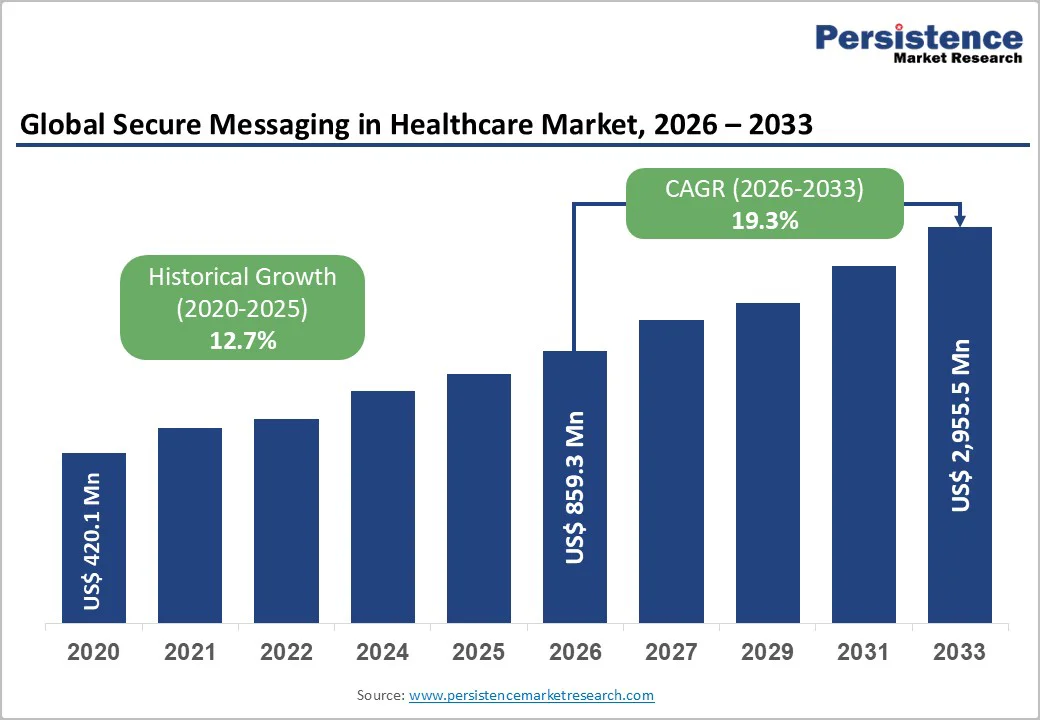
The global secure messaging in healthcare market is expected to reach US$ 859.3 million in 2026 and grow to US$ 2,955.5 million by 2033, at a CAGR of 19.3% during the forecast period.
Market Growth Drivers:
- Rising data breaches, with average healthcare incidents crossing $10M, are pushing stronger PHI protection across enterprises.
- Rapid cloud adoption is adding momentum, with about 70–90% of IT teams using compliant platforms such as AWS.
- Regulatory mandates for encryption and RBAC are forcing organizations to tighten access and data controls.
- AI-driven analytics is improving how enterprises detect and respond to PHI risk in real time.
- Telehealth growth is expanding the need for secure data exchange across distributed care environments.
- Zero-trust security models are gaining traction to protect PHI across EHR systems and healthcare SaaS platforms.
Enterprise healthcare systems handle large volumes of patient data every day. Without strong PHI protection, even a small gap can expose sensitive records and trigger compliance issues.
As digital care models expand, organizations need platforms that keep data protected while still supporting fast, connected workflows.
1. Protect patient trust and brand reputation
Patients expect their health information to stay private. When systems keep PHI properly controlled, organizations maintain credibility and avoid the reputational damage that follows a breach.
2. Meet strict regulatory requirements
Healthcare platforms must satisfy rules such as HIPAA and regional privacy laws. Built-in PHI controls help enterprises stay audit-ready and reduce the risk of penalties.
3. Support secure digital transformation
Hospitals and health networks are expanding telehealth, remote monitoring, and data sharing. PHI-secure platforms allow this growth to happen without exposing sensitive information.
4. Reduce financial and operational risk
Data breaches can lead to heavy response costs, legal pressure, and workflow disruption. Strong access controls and monitoring help limit these risks early.
Enterprises that treat PHI protection as a core platform capability are better positioned to scale digital healthcare safely and confidently.
What PHI Security Really Means in Enterprise Healthcare
PHI security in enterprise healthcare requires identity controls, governed data flows, continuous monitoring, and audit-ready architecture across connected systems.
The Regulatory Pressure Shaping PHI Security
Healthcare organizations work under strict privacy rules such as HIPAA and other regional data laws. These mandates set the baseline for how patient data must be handled. However, passing an audit does not always mean PHI is fully protected.
Real security depends on how systems manage identity, data movement, and day-to-day controls across the environment. As platforms grow and connect with more partners, the gap between compliance and actual protection can widen if controls are not designed carefully.
Key elements of PHI protection
1. Identity and access governance
Strong identity controls decide who can see or use patient data. Role design, least privilege, and regular access reviews keep exposure limited.
2. Data encryption at rest and in transit
Encryption keeps PHI protected when it is stored and while it moves between systems. This reduces the chance of data being read if intercepted.
3. API and integration security
Healthcare platforms depend heavily on APIs and external connections. Securing these touchpoints prevents unauthorized data access across EHRs and partner systems.
4. Audit logging and traceability
Complete activity logs help teams track who accessed what and when. This visibility supports faster investigations and smoother audits.
5. Consent and policy enforcement
Patient consent and data use rules must be enforced automatically. Policy-driven controls help maintain compliance as data flows expand.
Enterprise PHI protection works best when these controls function together as one coordinated system, not as isolated safeguards.
What Are PHI-Secure Enterprise Healthcare Platforms?
PHI secure enterprise healthcare platforms are software systems designed to protect sensitive patient information while supporting large-scale healthcare operations. They control who can view or use protected health information and keep data safe as it moves across EHRs, apps, and cloud environments.
These platforms combine identity management, encryption, monitoring, and policy enforcement into one coordinated environment. As a result, healthcare organizations can run digital services, share data with partners, and expand care programs without exposing patient records or falling out of compliance with regulations such as HIPAA.
How Do They Work?
PHI secure healthcare platforms follow a clear control flow from login to audit. Each step checks identity, limits data use, and records activity.
This helps large healthcare groups protect patient data while still running fast digital operations. Below is how the process usually works inside an enterprise environment.
1. A User Signs In And Gets Verified
The flow begins when a clinician, staff member, or partner logs in. The platform checks the username and password first.
Then it may ask for MFA, which means a second proof, like a code on the phone. The system can also check device and location risk. This first check stops many unauthorized users early.
2. The Platform Assigns The Right Role
After login, the platform links the user to a defined role. Roles are based on job duties and approved access levels.
Therefore, each user only sees what they truly need for their work. This keeps exposure low across large teams.
3. A Request For PHI Gets Evaluated
When the user tries to open patient data, the platform runs a quick policy check. It reviews permissions, patient consent, and the purpose of access. If something does not match the rules, the request is blocked or flagged for review.
4. Data Moves Through Secure Connections
When access is allowed, the data travels through encrypted channels. This keeps PHI protected while it moves between systems. In addition, API gateways check each request to confirm it follows security rules.
5. The Platform Limits What Gets Shared
The system sends only the minimum data needed for the task. Sensitive fields stay hidden if the user does not require them. However, if a request asks for too much, the platform automatically restricts the response.
6. Every Action Gets Logged And Tracked
The platform records detailed logs for logins, views, edits, and downloads. These records show who did what and when. Therefore, security and compliance teams can review activity quickly when needed.
7. Monitoring Flags Unusual Activity
The system watches user behavior in real time. It looks for signs like odd login times, new locations, or large data exports. When something looks risky, alerts go to the security team for fast action.
8. Audits And Reports Stay Ready
Because activity is tracked continuously, audit reports are easy to generate. Compliance teams can pull records without heavy manual work. As a result, organizations stay prepared for reviews while daily work continues smoothly.
When these steps work together, PHI secure platforms keep patient data tightly controlled while still supporting large-scale healthcare operations.
Must-Have Features of PHI-Secure Healthcare Platforms
Enterprise PHI secure healthcare platforms need strong identity control, encrypted data handling, continuous monitoring, and governed interoperability to protect patient information at scale.
Enterprise buyers usually look past surface-level security claims. What matters more is whether the platform can protect sensitive data across large teams, connected systems, and growing digital programs. The features below show what separates true enterprise-grade PHI secure software from basic healthcare tools.
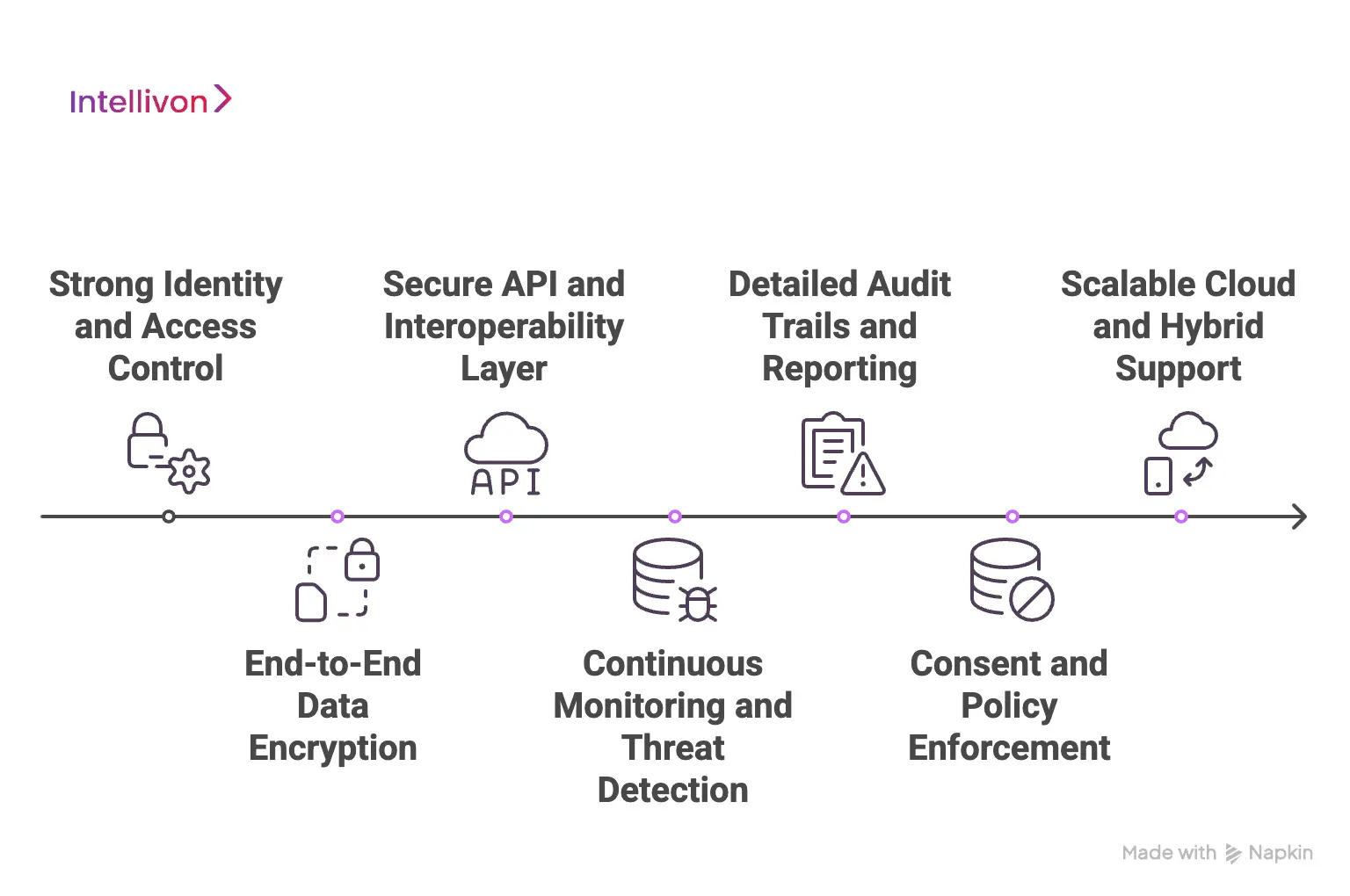
1. Strong identity and access control
At enterprise scale, access control cannot stay loose. The platform needs tight role-based access, least privilege rules, and regular access reviews. It also helps when MFA and adaptive login checks run quietly in the background. Together, these controls reduce the chance of unauthorized entry across the environment.
2. End-to-end data encryption
Patient data moves often between systems, partners, and cloud services. Because of that, encryption must protect PHI both at rest and in transit. Mature platforms also manage encryption keys carefully, which lowers exposure risk during transfers, backups, and integrations.
3. Secure API and interoperability layer
Modern healthcare runs on constant data exchange. The platform, therefore, needs governed APIs, along with FHIR and HL7 security controls. Strong partner authentication also matters here. When these pieces work together, data can move across EHRs and digital health systems without opening new gaps.
4. Continuous monitoring and threat detection
Enterprise teams need real-time visibility into what is happening inside the platform. Good systems watch user behavior, access patterns, and system activity without slowing operations. If something unusual appears, security teams get alerts early enough to act before the issue grows.
5. Detailed audit trails and reporting
When regulators or internal teams ask questions, logs must tell a clear story. The platform should keep complete and tamper-resistant records of access and activity. Just as important, reports should be easy to generate so audits do not turn into fire drills.
6. Consent and policy enforcement
Patient consent rules are getting more complex across regions and care models. Policy-driven controls help apply the right data limits automatically. This keeps data use aligned with privacy rules even as the ecosystem expands.
7. Scalable cloud and hybrid support
Large healthcare groups rarely stay in one environment for long. The platform should work smoothly across cloud, hybrid, and on-prem setups. When done right, organizations can grow their infrastructure without weakening their PHI protection posture.
Enterprise-grade PHI secure platforms bring these controls together into one coordinated layer. When the foundation is solid, healthcare organizations can scale digital services while keeping sensitive patient data properly protected.
Core Architecture Principles for PHI-Secure Platforms
PHI secure platforms use a layered design where identity, zero trust checks, data protection, secure data exchange, and monitoring work together from the start.
Enterprise healthcare platforms stay reliable when security is built in layers, and not added later. Each layer handles a different risk point in the data journey. When these layers support each other properly, patient information stays protected even as the platform expands across regions and partners. High-risk gaps appear when one of these layers is weak or loosely connected.
Below is how mature PHI secure software is typically designed.
Layer 1: Identity and Access Control Layer
This layer works as the front door of the platform. Every user, device, and connected service must prove identity before any PHI request moves forward. In large healthcare environments, weak identity controls often create the earliest exposure.
A well-designed platform keeps identity management centralized and tightly governed. It assigns access based on job role and real need, not broad default permissions.
At the same time, multi-factor authentication adds another check for sensitive actions. Admin accounts also receive closer monitoring because they carry a higher risk.
Most strong implementations include:
- Central identity directory for all workforce and partner users
- Role-based and attribute-based access rules
- Multi-factor authentication for high-risk access
- Privileged access monitoring for admin users
- Automated onboarding and offboarding of user accounts
When identity is handled carefully, many downstream risks reduce on their own.
Layer 2: Zero Trust Security Layer
Healthcare systems today run across cloud services, partner apps, and remote users. Because of this spread, the platform cannot assume that any session is fully safe after login. The zero-trust layer keeps checking activity throughout the session.
This layer evaluates device health, user behavior, and network signals in real time. Here, sessions are kept short, so stolen credentials have less value. If something looks unusual, the platform can ask for extra verification before allowing the action. This approach helps contain threats before they spread across systems.
Common capabilities in this layer include:
- Continuous session validation
- Device and location risk checks
- Short-lived access tokens
- Step up authentication for sensitive actions
- Microsegmentation between services
With zero trust in place, lateral movement inside the environment becomes much harder.
Layer 3: Data Protection Layer
This layer focuses directly on the safety of PHI itself. Even when access is approved, the platform still limits how much data becomes visible. This reduces the impact if an account is misused.
Encryption protects patient data while it is stored and while it is moving between systems. Many enterprise platforms also apply field-level masking so highly sensitive elements stay hidden unless truly needed. Key management stays tightly controlled because weak key handling can undo strong encryption.
Important controls in this layer usually include:
- Encryption of PHI at rest and in transit
- Field-level masking of sensitive data
- Minimum necessary data sharing rules
- Secure encryption key management
- Data loss prevention policies
Strong data protection means that even intercepted data is far less useful to attackers.
Layer 4: Secure Interoperability Layer
Healthcare platforms depend heavily on data exchange across EHRs, payer systems, and digital health tools. This layer governs how PHI moves between those systems. Without tight control here, exposure often happens in transit.
A mature platform secures APIs, validates partner systems, and enforces standards such as FHIR and HL7. It also applies rate limits and schema validation, so unexpected data requests do not slip through. Partner onboarding usually follows a governed process instead of open connectivity.
This layer typically includes:
- API gateway with strong authentication
- FHIR and HL7 security enforcement
- Partner and vendor access controls
- Data exchange policy checks
- Rate limiting and schema validation
When interoperability is governed well, the platform can share data safely at enterprise scale.
Layer 5: Monitoring and Audit Layer
The final layer gives the organization full visibility into what is happening across the platform. Without this view, teams often detect issues too late.
Continuous monitoring tracks user behavior, data access patterns, and system activity. When something unusual appears, alerts reach security teams quickly. At the same time, detailed logs create a clear history for investigations and regulatory reviews. Good platforms make these reports easy to generate without heavy manual effort.
Core functions in this layer include:
- Real-time activity monitoring
- Behavioral anomaly detection
- Centralized audit logging
- Compliance reporting dashboards
- Incident response support
With strong monitoring in place, organizations move from reactive firefighting to controlled oversight.
PHI secure healthcare platforms stay resilient when these architectural layers work together as one system. This layered approach helps enterprises protect patient data while still supporting large-scale digital healthcare growth.
How Intellivon Builds PHI-Secure Healthcare Platforms
Intellivon builds PHI secure healthcare platforms through a step-by-step delivery model that covers risk mapping, secure architecture, controlled build, validation, and ongoing governance.
Enterprises rarely struggle because they lack security tools. More often, the challenge is stitching those controls into a platform that still runs smoothly at scale. We approach this work as a disciplined build journey, where PHI protection stays visible from the first discovery session through long-term operations.
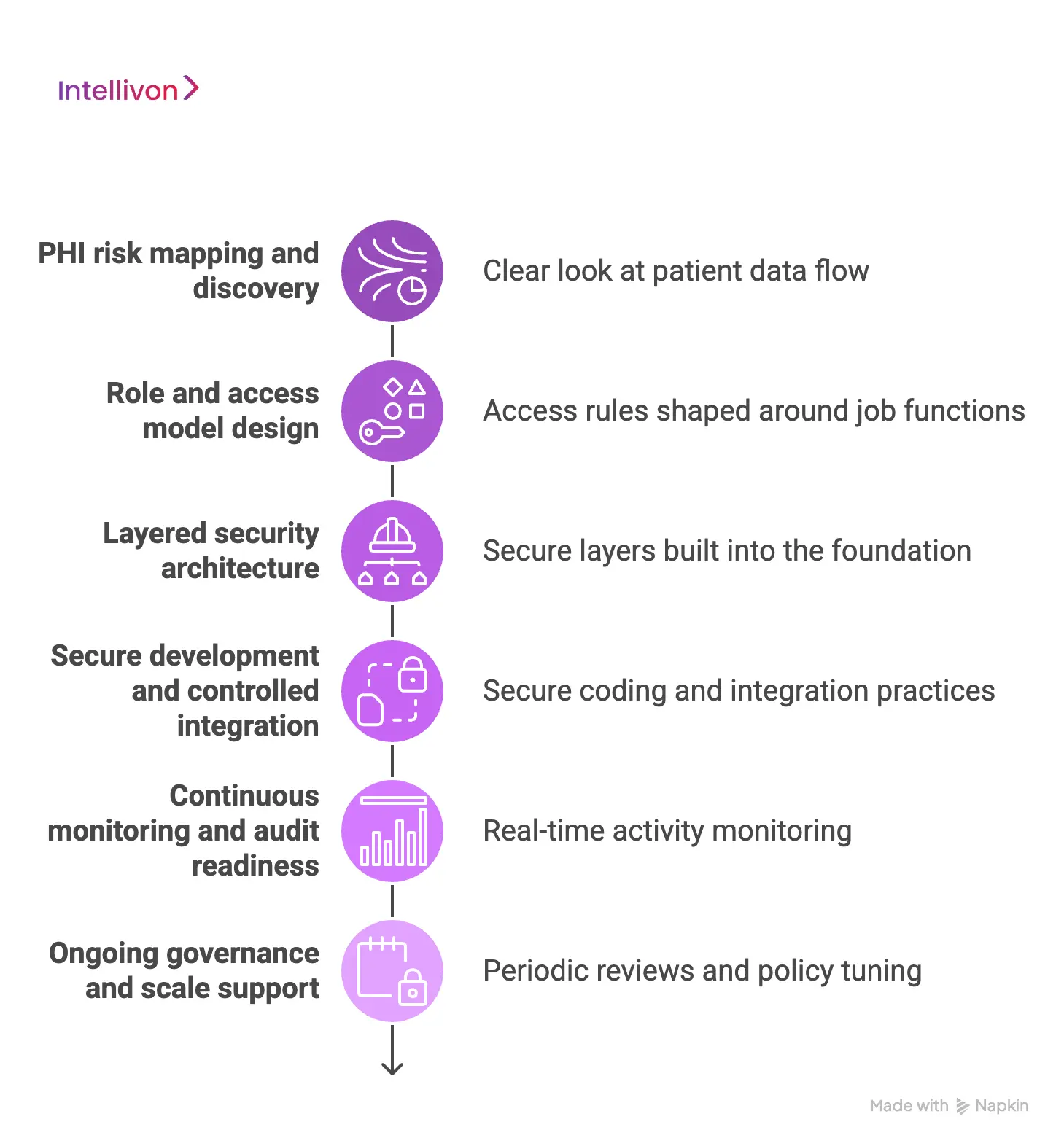
Step 1: PHI risk mapping and discovery
Every engagement starts with a clear look at how patient data moves through the environment. The team reviews EHR connections, user groups, partner touchpoints, and high-risk workflows. This step often surfaces hidden exposure areas that standard reviews miss.
What this stage delivers
- End-to-end PHI flow mapping
- Identification of high-risk access points
- A prioritized security and compliance baseline
This early clarity helps prevent expensive redesign later.
Step 2: Role and access model design
Once risks are clear, access rules are shaped around real job functions. The focus stays on least privilege without slowing clinical or operational work. Special attention goes to admin accounts and third-party access because those areas tend to carry elevated risk.
What this stage delivers
- Enterprise-ready role-based access model
- MFA and session control policies
- Access lifecycle and review framework
When access is designed carefully, many downstream security issues never appear.
Step 3: Layered security architecture
With identity rules in place, the platform architecture takes shape in secure layers. Identity controls, data protection, API governance, and monitoring are built into the foundation rather than added later. Because of this, the platform can expand without creating new blind spots.
What this stage delivers
- Layered PHI secure architecture blueprint
- Secure interoperability design for EHR and partners
- Clear data segmentation boundaries
This step sets the long-term stability of the platform.
Step 4: Secure development and controlled integration
During the build phase, engineering teams follow secure coding and integration practices. APIs, data pipelines, and external connections are tested against policy rules. In addition, automated checks run inside the CI/CD pipeline to catch drift early.
What this stage delivers
- Secure code and API validation
- Policy-aligned integration controls
- Early detection of configuration risk
This keeps security aligned with development speed.
Step 5: Continuous monitoring and audit readiness
Before and after launch, visibility becomes the focus. Monitoring tools track user behavior, data access patterns, and system activity across the environment. When something looks unusual, alerts reach security teams quickly. Audit trails also stay clean and easy to generate.
What this stage delivers
- Real-time activity monitoring
- Behavioral risk detection
- Audit-ready logging and reporting
Strong visibility reduces surprise during audits and incident reviews.
Step 6: Ongoing governance and scale support
Enterprise platforms do not stand still, and security cannot either. As new users, partners, and regions come online, controls must stay aligned. Intellivon supports teams with periodic reviews, policy tuning, and architecture guidance so PHI protection keeps pace with growth.
What this stage delivers
- Periodic access and policy reviews
- Guidance for new integrations and regions
- Long-term PHI protection maturity roadmap
Intellivon builds PHI secure healthcare platforms through a structured, architecture-first approach. The result is a system that protects sensitive patient data while still supporting large-scale digital healthcare growth.
Cost Of Building A PHI-Secure Enterprise Healthcare Platform
At Intellivon, PHI secure healthcare platforms are built as a regulated healthcare data infrastructure, not as security features added on top of existing systems. The focus stays on creating platforms that protect patient data across providers, partners, regions, and evolving privacy mandates. Every design choice accounts for governance, interoperability, and long-term risk from the beginning.
When budget pressure appears, scope can be refined with care. However, identity controls, encryption, consent enforcement, and audit visibility are never reduced. Because of this approach, enterprises avoid costly remediation after launch. Over time, predictability improves, and long-term ROI stays protected.
Estimated Phase-Wise Cost Breakdown
| Phase | Description | Estimated Cost Range (USD) |
| Discovery & Risk Alignment | PHI flow mapping, regulatory review, platform scope definition | $5,000 – $8,000 |
| Secure Architecture Design | Layered security model, identity flows, data protection blueprint | $6,000 – $10,000 |
| Identity & Access Framework | RBAC/ABAC design, MFA setup, session policy definition | $6,000 – $9,000 |
| Backend & Enterprise Integrations | EHR connections, APIs, partner systems, identity services | $10,000 – $18,000 |
| Frontend & Role-Based Interfaces | Clinical, admin, and partner dashboards with access controls | $6,000 – $10,000 |
| Data Protection & Encryption Layer | Encryption setup, key management, and data masking controls | $5,000 – $9,000 |
| Monitoring & Audit Infrastructure | Logging pipeline, anomaly detection, compliance reporting | $5,000 – $8,000 |
| Testing & Compliance Validation | Functional, security, and regulatory readiness testing | $4,000 – $7,000 |
| Deployment & Scale Readiness | Cloud or hybrid rollout, performance tuning, and monitoring setup | $4,000 – $7,000 |
Total initial investment: $50,000 – $100,000
Ongoing maintenance and optimization: 15–20% of the initial build per year
Hidden Costs Enterprises Should Plan For
Even well-planned PHI secure programs can face pressure when indirect cost drivers are missed. Planning for these early helps protect budgets, timelines, and compliance posture as the platform grows.
- Integration complexity increases as EHRs and partner systems expand
- Compliance overhead grows with audits and regulatory updates
- Governance needs ongoing policy reviews and access tuning
- Infrastructure costs rise with data volume and monitoring workloads
- Change management includes onboarding clinical and IT teams
- Continuous monitoring becomes more important as usage scales
Best Practices to Avoid Budget Overruns
Based on Intellivon’s experience delivering enterprise healthcare platforms, these practices help keep costs controlled and outcomes predictable.
- Start with clear PHI flow mapping before expanding the scope
- Build governance and auditability into the core architecture
- Use modular components that scale without redesign
- Plan interoperability early to avoid expensive rework
- Maintain strong observability across security and performance
- Design for evolving regulations, not one-time compliance
Ready to plan your PHI secure platform?
Request a tailored proposal from Intellivon’s healthcare experts to receive a delivery roadmap aligned with your budget, compliance exposure, and long-term digital health strategy.
Designing Identity and Access Controls That Actually Hold
Effective PHI secure software depends on well-designed identity and access controls that enforce least privilege, continuous verification, and real-time monitoring across users and systems.
Identity and access control often look solid on paper. However, many enterprise breaches still trace back to weak role design, stale permissions, or overly trusted sessions. Strong PHI protection depends on controls that hold up under daily operational pressure, not just during audits.
The goal is simple. The right person gets the right access at the right time, and nothing more. Below are the practices that help enterprise platforms reach that standard.
1. Start With Role Clarity
Many access problems begin with poorly defined roles. Therefore, the first step is mapping real job functions to precise access needs. Clinical staff, billing teams, partners, and admins should never share broad default permissions.
Well-designed platforms usually include:
- Role-based and attribute-based access models
- Least privilege enforcement across all user groups
- Separation between clinical, financial, and admin access
- Periodic role reviews to remove permission creep
Clear role boundaries reduce the risk of accidental overexposure.
2. Apply Strong Authentication
Not every login carries the same level of risk. Because of that, mature platforms apply step-up authentication when sensitive actions occur. This keeps workflows smooth while still protecting high-value data.
Common controls include:
- Multi-factor authentication for privileged users
- Adaptive login checks based on device and location
- Short-lived session tokens
- Re-authentication for sensitive data access
These measures make stolen credentials far less useful.
3. Watch Third-Party Access Closely
Admin accounts and external partners often have a broader reach inside the system. If left loosely governed, they can become quiet risk points. Strong platforms treat this access with extra scrutiny.
Key protections typically include:
- Privileged access monitoring and session recording
- Time-bound access for vendors and support teams
- Just-in-time access for high-risk tasks
- Automated alerts for unusual admin behavior
Tighter control here reduces high-impact exposure.
4. Keep the access lifecycle fully automated
Manual user management rarely keeps up at enterprise scale. When employees change roles or leave the organization, access must adjust quickly. Automation helps prevent stale accounts from lingering in the system.
Mature environments usually implement:
- Automated user provisioning tied to HR systems
- Immediate deprovisioning on role change or exit
- Scheduled access recertification campaigns
- Continuous policy enforcement across systems
This keeps permissions aligned with real workforce changes.
5. Maintain continuous visibility and review
Access control is not a one-time setup. Behavior and risk change over time, so monitoring must stay active. Platforms that track usage patterns can catch problems early.
Important capabilities include:
- Real-time access monitoring
- Behavioral anomaly detection
- Centralized audit logging
- Regular access reviews by security teams
With strong visibility, organizations move from reactive fixes to controlled oversight.
Identity and access controls only work when they reflect real roles, adjust to risk, and stay continuously monitored. Platforms that treat access as a living control layer are far better positioned to protect PHI at enterprise scale.
Securing Data Flow Across EHRs, APIs, and AI Systems
PHI secure software must protect patient data while it moves across EHRs, APIs, and AI systems through encryption, governed APIs, and continuous monitoring.
Most PHI exposure does not happen where data is stored. It usually happens while the data is moving between systems. As healthcare platforms connect EHRs, partner apps, and AI services, the number of data paths grows quickly. Therefore, enterprises must treat data in motion as a high-risk zone.
A strong platform controls how information is requested, transmitted, processed, and shared. Below are the areas that need the most attention.
1. Secure EHR Integration Points
EHR systems sit at the center of most healthcare ecosystems. However, every new connection to the EHR creates another path for PHI to move. Without proper controls, these links can expose sensitive records.
Enterprise platforms reduce this risk by:
- Validating every system that requests EHR data
- Applying role-based filters before data leaves the EHR
- Enforcing purpose of use checks
- Monitoring bulk data exports closely
When these checks run consistently, EHR data stays far better contained.
2. Govern APIs That Move Patient Data
APIs carry a large share of PHI traffic across modern healthcare platforms. Because of this, weak API controls often become a hidden exposure point. Good PHI secure software treats APIs as high-value assets, not simple connectors.
Mature API protection usually includes:
- Strong authentication and token validation
- Rate limiting to prevent abuse
- Schema validation to block unexpected data requests
- Central API gateway enforcement
- Detailed API activity logging
These controls help prevent unauthorized or excessive data access.
3. Set Clear Boundaries For AI
AI models and analytics tools need data to deliver value. However, they can also create new exposure paths if boundaries are unclear. Enterprises must define what data AI systems can see, store, or process.
Strong platforms usually:
- Limit PHI sent to AI pipelines
- Mask or de-identify sensitive fields when possible
- Control training data access carefully
- Monitor model output for data leakage
- Apply policy checks before AI-driven data actions
With these guardrails in place, AI can support innovation without increasing privacy risk.
4. Protect Third-Party Data Exchange
Healthcare platforms rarely operate alone. Data often flows to payers, labs, digital health vendors, and regional partners. Each external connection adds another layer of responsibility.
To stay protected, enterprises typically:
- Require strong partner authentication
- Use secure data exchange standards such as FHIR and HL7
- Apply time-bound access for vendors
- Monitor partner activity continuously
- Review partner permissions on a regular cycle
This keeps the extended ecosystem from becoming the weakest link.
5. Maintain End-to-End Visibility
Even strong controls can drift over time. Therefore, continuous visibility across data flows is essential. Security teams need to see who accessed what, when, and through which pathway.
Key monitoring practices include:
- Real-time data access tracking
- Cross-system activity correlation
- Alerts for unusual data movement
- Centralized audit logging
- Rapid investigation workflows
When visibility stays high, organizations can respond before small issues become large incidents.
PHI stays safest when enterprises control every stage of data movement across EHRs, APIs, and AI systems. Platforms that combine encryption, strong API governance, and continuous monitoring are far better prepared to protect patient data at scale.
Advanced AI Capabilities That Strengthen PHI Protection
Advanced AI in PHI secure software improves data protection through anomaly detection, behavior analytics, risk scoring, and automated policy enforcement.
Traditional security rules still matter, but they struggle to keep pace with large and fast-moving healthcare environments. As user volume grows and data paths multiply, manual reviews miss subtle risk signals. This is where AI adds real value. It watches patterns continuously and flags problems earlier than static controls can.
When used carefully, AI strengthens PHI protection without slowing clinical or operational work.
1. AI-driven Anomaly Detection
AI models can study normal access patterns across users, devices, and applications. Over time, the system learns what typical behavior looks like. Therefore, when something unusual appears, it can raise an alert quickly.
Typical capabilities include:
- Detection of unusual login times or locations
- Alerts for sudden spikes in data access
- Identification of abnormal download behavior
- Early warning for possible credential misuse
This helps security teams act before small issues grow into major incidents.
2. Behavioral Identity Analytics
Not every threat comes from outside attackers. Sometimes, valid accounts get misused or compromised. Additionally, AI-based behavior analytics looks closely at how each user normally works.
Strong platforms use AI to:
- Build behavior profiles for users and admins
- Detect insider risk patterns
- Flag session activity that breaks normal habits
- Highlight accounts that may be compromised
Because of this visibility, enterprises can respond faster to hidden access risks.
3. Intelligent Risk Scoring
Large healthcare environments generate thousands of access events every day. Security teams cannot review each one manually. AI helps by assigning risk scores to users, sessions, and data requests.
Most mature systems:
- Rank high-risk access attempts automatically
- Prioritize alerts that need human review
- Combine identity, device, and behavior signals
- Continuously update risk levels as activity changes
This allows teams to focus attention where it matters most.
4. Automated Policy Enforcement
AI can also help keep access policies aligned as environments evolve. Instead of waiting for manual reviews, the system can suggest or apply tighter controls when it detects drift.
Common uses include:
- Recommending permission reductions
- Flagging over-provisioned roles
- Suggesting step-up authentication triggers
- Detecting policy conflicts across systems
Over time, this reduces the chance of silent permission creep.
5. Privacy-Preserving AI techniques
Healthcare organizations still need analytics and insights from patient data. However, privacy must stay protected during that process. Advanced platforms use privacy-preserving methods to balance both needs.
These may include:
- Data masking before AI processing
- The identification of sensitive fields
- Secure enclaves for model training
- Controlled access to training datasets
With these safeguards, AI can support innovation without exposing raw PHI.
Advanced AI capabilities strengthen PHI protection by adding continuous intelligence on top of traditional controls. When deployed carefully, these tools help enterprises detect risk earlier, enforce policies faster, and protect patient data more consistently at scale.
Common Mistakes Enterprises Make (and How to Avoid Them)
Most PHI security failures come from broad access, weak API control, late security design, and poor visibility. Prevention requires the first discipline and continuous governance.
Even mature healthcare programs run into avoidable security gaps. The problem usually is not missing tools. Instead, controls are applied too late, permissions grow too wide, or monitoring stays limited. Over time, these small gaps increase exposure and raise audit pressure.
Below are the mistakes that appear most often and how they can be prevented.
1. Late security
Many teams still treat PHI protection as something to tighten near the end of the build. At first, the platform may look compliant. However, as integrations and users grow, hidden gaps begin to surface. Fixing them later often leads to delays, budget overruns, and workflow disruption. In addition, retrofitting security rarely closes every exposure point.
How we solve it: Security is built into the architecture from the first phase. Identity, encryption, and monitoring are designed early, so the platform grows without costly rework.
2. Broad access
Enterprises sometimes grant wide permissions to speed up onboarding and operations. Over time, these permissions remain even when roles change or teams move. As a result, users often have more access than they truly need. This increases the risk of accidental exposure and insider misuse. In large environments, this problem grows quietly.
How we solve it: Access models are mapped to real job functions with strict least privilege rules. Automated reviews and role cleanups keep permissions aligned with actual responsibilities.
3. Weak API Control
APIs move a large share of PHI across healthcare systems. However, many organizations still treat them as simple connectors. Without strict validation, rate limits, and monitoring, APIs can become quiet entry points for data leakage. This risk increases as partner integrations expand and traffic grows.
How we solve it: Governed API gateways, strong authentication, and continuous traffic monitoring are applied. This keeps data exchange controlled even as integrations scale.
4. Limited Visibility
Some platforms log activity but do not analyze it in real time. Because of this, risky behavior can continue for weeks before anyone notices. By the time alerts surface, the investigation becomes harder, and the impact grows. Limited visibility also slows audit response.
How we solve it: Continuous monitoring and behavior analytics run across the environment. Security teams receive early alerts, and audit logs stay ready when reviews begin.
5. Static Compliance Mindset
Many organizations focus only on passing the next audit. While that may work short-term, environments keep changing. New users, partners, and data flows introduce fresh risks that static controls cannot catch. Compliance should move with the platform, not lag behind it.
How we solve it: Ongoing governance reviews and policy tuning keep PHI controls aligned as the ecosystem evolves. This helps enterprises stay prepared beyond one-time certification.
Enterprises that avoid these common mistakes usually treat PHI protection as a living discipline. With the right architecture, access controls, and visibility in place, healthcare platforms stay resilient even as they scale.
Conclusion
PHI security has become a core requirement for any enterprise healthcare platform. As systems expand and data flows grow, small gaps can quickly turn into serious risks.
Therefore, organizations need platforms where protection is built into identity, data movement, and monitoring from the start. The right architecture not only reduces compliance pressure but also supports faster and safer digital growth.
Intellivon helps enterprises design and scale PHI secure software that holds up in real-world conditions. If your organization is planning the next phase of digital healthcare, now is the time to build on a stronger, security-first foundation.
Build PHI-Secure Healthcare Platforms With Intellivon
At Intellivon, PHI secure healthcare platforms are built as a regulated healthcare data infrastructure, not as security layers added onto existing systems. Every architectural and delivery decision focuses on data protection, identity control, and interoperability. This approach helps platforms run safely across providers, partners, regions, and evolving privacy requirements, not just during the initial rollout.
As enterprise healthcare environments grow, stability becomes more important. Governance, performance, and audit readiness stay consistent even as user volume, integrations, and data exchange increase. Organizations keep firm control over patient data, access permissions, and compliance posture without adding operational friction or hidden risk.
Why Partner With Intellivon?
- Enterprise-grade PHI secure architecture designed for regulated healthcare ecosystems
- Proven delivery across hospitals, health networks, and digital health platforms
- Compliance by design approach with built-in audit visibility and policy enforcement
- Secure modular infrastructure supporting cloud, hybrid, and on-prem deployments
- AI-driven monitoring, risk detection, and automation with strong governance controls
Book a strategy call to explore how Intellivon can help you build and scale PHI secure healthcare platforms with confidence, control, and long-term enterprise value.

FAQs
Q1. What is PHI secure software in healthcare?
A1. PHI secure software is designed to protect sensitive patient information across healthcare systems. It controls who can view data, encrypts information in transit and at rest, and tracks activity. This helps organizations meet privacy rules while still running digital care programs efficiently.
Q2. Why do enterprises need PHI secure healthcare platforms?
A2. Large healthcare organizations manage data across many systems and partners. Without strong protection, the risk of exposure rises quickly. PHI secure platforms help reduce breach risk, support compliance, and keep patient trust intact as digital services expand.
Q3. How long does it take to build a PHI secure platform?
A3. Timelines vary based on scope, integrations, and compliance needs. However, most enterprise builds take a few months from discovery to deployment. Early architecture planning usually speeds up delivery and reduces rework later.
Q4. What features should enterprises look for first?
A4. Start with strong identity and access control, end-to-end encryption, secure APIs, and continuous monitoring. In addition, look for detailed audit logging and policy enforcement. These features form the foundation of reliable PHI protection.
Q5. How does AI help strengthen PHI protection?
A5. AI helps by watching user behavior and data access patterns in real time. It can flag unusual activity, prioritize risks, and support faster response. When used correctly, AI adds an extra layer of intelligence on top of traditional security controls.