Authentication in EHR-integrated applications can look healthy for long stretches. Under this system, the clinicians can sign in, the single sign-on behaves as expected, and daily workflows can keep moving. Because everything continues to function, the authentication layer behind these integrations does not always get a second look. Due to this oversight, data exposure starts at the moment trust passes from the identity system into the clinical application.
As more apps, partners, and digital services connect to the EHR environment, trust between parties becomes harder to manage. Hence, small weaknesses in token handling, session checks, or multifactor enforcement can grow over time if they are not revisited. In complex healthcare ecosystems, the issue is an authentication design that was never built for the level of integration now in place.
In this blog, we break down what secure authentication should look like for EHR-integrated apps. Drawing on Intellivon’s experience across multi-system healthcare environments, we outline the design choices, common weak points, and practical safeguards that help organizations strengthen access without slowing clinical workflows.
Why Authentication Is Essential for EHR-Connected Apps Now
Authentication is now mission-critical for EHR-connected applications as healthcare breaches continue to rise. Attackers still exploit weak credentials across the expanding digital ecosystem.
Therefore, organizations are adopting multifactor authentication and biometrics to protect patient data and stay aligned with tightening HIPAA expectations, including the 2025 push toward broader MFA adoption.
The global electronic health record applications market reached approximately USD 783.22 million in 2023. Moreover, analysts expect it to expand at a CAGR of 8.87% between 2024 and 2030, reflecting steady growth in digital healthcare adoption.
The Biggest Data Breaches:
- 2024 to 2025: More than 700 U.S. healthcare breaches exposed over 275 million records, marking a 63.5% jump from 2023 and the largest spike on record. Stolen credentials remained the primary entry point, frequently linked to groups such as RansomHub and ShinyHunters.
- 2023: A total of 725 breaches compromised 133 million records. Moreover, since 2020, attackers have exposed more than 590 million healthcare records, meaning many U.S. citizens have been affected multiple times.
- Ascension (2024): A ransomware incident exposed 5.6 million records, including names, Social Security numbers, and clinical data. As a result, operations across 142 hospitals experienced weeks of disruption.
- WebTPA (2024): A credential-based intrusion affected approximately 2.43 million individuals, exposing sensitive personal and insurance information.
What Goes Wrong Without Strong Authentication
Weak authentication rarely fails in obvious ways. Instead, it creates quiet exposure points that grow over time. In EHR-integrated environments, one weak login can ripple across multiple clinical and operational systems.
As integrations expand, the blast radius of a single compromise also increases. Therefore, healthcare enterprises often discover the damage only after data access patterns or audit trails raise concerns. Below are the most common failure patterns seen in real enterprise environments.
1. Unauthorized Patient Record Access
When authentication controls are weak, attackers and unauthorized insiders can access patient charts without immediate detection. In many cases, basic SSO success is mistaken for full security coverage.
This risk becomes serious in EHR-connected apps because once a user is authenticated, downstream systems often trust the session automatically. As a result, sensitive clinical data may be viewed, exported, or misused without proper verification.
2. Privilege Creep Across Integrated Systems
Over time, users accumulate access rights that no longer match their roles. Without strong identity validation and periodic review, these excess privileges remain active.
In practice, EHR-integrated apps often inherit permissions from upstream identity systems. However, if authentication and authorization are loosely enforced, users may retain access to modules they no longer need. Consequently, the attack surface quietly expands.
3. Session Hijacking and Token Misuse
Weak session controls make it easier for attackers to reuse valid tokens or hijack active sessions. This is especially risky in environments that rely heavily on web and mobile clinical tools.
For example, long-lived tokens, poor device validation, or missing re-authentication checks allow bad actors to operate as legitimate users. Therefore, even a well-designed EHR security architecture can be undermined by poor session hygiene.
4. Compliance and Audit Gaps
Regulators increasingly expect proof of strong identity assurance. However, weak authentication creates blind spots in audit trails and access logs.
When identity events are not tightly controlled, organizations struggle to demonstrate who accessed what and when. As a result, compliance exposure grows across HIPAA, HITRUST, and global privacy frameworks. In addition, incident investigations become slower and more expensive.
Healthcare enterprises must treat authentication as a core control layer within their EHR security architecture, not as a simple login feature. Strengthening this foundation reduces breach risk, improves audit confidence, and supports a safer digital scale.
Where Authentication Sits in the EHR Integration Architecture
Authentication sits at the trust boundary between users and clinical systems. In an EHR security architecture, it verifies identity before any data exchange occurs. A centralized identity layer helps healthcare enterprises enforce consistent access controls across integrated applications.
In large healthcare environments, authentication is not just a login screen. It operates as a control layer that governs who can enter the clinical ecosystem and under what conditions. As digital health tools multiply, this layer becomes the first line of defense across the entire EHR security architecture.
To understand its importance, it helps to see where authentication lives in the typical enterprise stack.
1. The Typical Trust Boundary in Healthcare Systems
In most hospitals and health networks, access flows through several coordinated layers. Each layer has a specific responsibility.
A simplified flow typically looks like this:
- User or system initiates access from a clinical app, portal, or device.
- The access gateway or application front end captures the login request.
- Identity provider (IdP) verifies credentials and applies MFA if required.
- IAM layer evaluates roles, policies, and contextual signals.
- An EHR platform, such as Epic or Cerner, grants scoped data access.
- Downstream clinical apps trust the validated session or token.
Because these steps are tightly connected, a weakness in the early stages can affect every system that follows. Therefore, authentication must be engineered as a shared enterprise control, not as an app-level feature.
2. Key Control Points in the Authentication Flow
Within this architecture, several moments carry a higher risk and therefore require stronger controls.
A. Login initiation
The system must validate the source, device posture, and user context. Otherwise, attackers can begin the flow from untrusted environments.
B. Credential and MFA verification
This is where identity proofing happens. Strong multifactor authentication significantly reduces credential-based attacks.
C. Token issuance and validation
After a successful login, the identity provider issues tokens. These tokens must be short-lived, properly scoped, and continuously validated.
D. Context switching between apps
In EHR-integrated environments, users often move between systems using SSO. Therefore, session trust must be carefully maintained and rechecked when risk signals change.
E. Audit and monitoring layer
Every authentication event should feed centralized logging. This supports compliance reporting and rapid incident response.
Why Centralization Matters in Enterprise Environments
Many healthcare organizations still manage authentication differently across applications. However, fragmented identity controls create inconsistent security and increase operational overhead.
A centralized approach within the EHR security architecture delivers several advantages:
- Consistent enforcement of MFA and access policies
- Faster onboarding and offboarding of workforce users
- Better visibility across clinical and administrative access
- Stronger audit readiness across HIPAA and HITRUST
- Reduced risk from third-party and vendor access
In addition, centralization supports Zero Trust initiatives that many health systems are now prioritizing.
Authentication sits at the front door of every EHR-connected workflow. However, its real value appears when it operates as a unified enterprise control plane. As digital care delivery expands, this foundation becomes essential to sustaining trust across the healthcare ecosystem.
Core Authentication Standards for EHR-Integrated Apps
Modern EHR security architecture relies on standards such as SMART on FHIR, OAuth 2.0, OpenID Connect, and SAML. These protocols enable secure identity verification, token-based access, and scalable interoperability across clinical applications.
Healthcare enterprises rarely build authentication from scratch. Instead, they depend on proven identity standards that support interoperability, auditability, and secure scale. However, choosing the right mix of protocols is critical. Each standard solves a different part of the identity problem within EHR-integrated environments.
Below are the core authentication frameworks that mature health systems rely on today.
1. SMART on FHIR Authentication
SMART on FHIR has become the dominant model for modern EHR integrations. It allows external applications to access clinical data securely while maintaining enterprise control.
At its core, SMART on FHIR combines OAuth 2.0 with healthcare-specific context. Therefore, it fits naturally into evolving EHR security architecture.
Key capabilities include:
- Secure app launch from within the EHR
- Scoped, token-based data access
- Patient and user context sharing
- Standards-based interoperability
- Support for mobile and web clinical apps
In practice, SMART on FHIR works best when the identity provider, EHR, and IAM policies are tightly aligned. Otherwise, token misuse and scope creep can still occur.
2. OAuth 2.0 for Delegated Authorization
OAuth 2.0 serves as the backbone for many healthcare authentication flows. It allows applications to access resources on behalf of a user without exposing credentials.
This model is especially useful in integrated clinical environments where multiple apps need controlled access to EHR data.
Common OAuth benefits include:
- Token-based access instead of password sharing
- Granular permission scopes
- Support for third-party integrations
- Reduced credential exposure risk
- Compatibility with SMART on FHIR
However, OAuth alone does not confirm user identity. Therefore, it must be paired with strong authentication and identity validation controls.
3. OpenID Connect for Modern Identity Verification
OpenID Connect builds on OAuth 2.0 by adding an identity layer. It provides ID tokens that confirm who the user is, not just what they can access.
As healthcare moves toward cloud and mobile experiences, OpenID Connect is becoming more important inside enterprise EHR security architecture.
Organizations typically adopt it for:
- Single sign-on across clinical apps
- Identity federation across partners
- Mobile workforce access
- Patient-facing digital experiences
- Cloud-based healthcare platforms
Because it supports modern web standards, OpenID Connect helps reduce friction while maintaining strong identity assurance.
4. SAML 2.0 in Legacy Hospital Environments
Many large health systems still rely on SAML 2.0, especially in older enterprise environments. While it remains reliable, it is less flexible than newer token-based models.
SAML is most commonly used for:
- Workforce single sign-on
- Legacy enterprise applications
- Internal clinical portals
- Federation with established partners
However, SAML can introduce complexity in mobile and API-driven workflows. Therefore, many organizations now run hybrid models that combine SAML with OAuth and OpenID Connect.
5. Passwordless and FIDO2: The Emerging Direction
Healthcare identity is gradually moving toward passwordless authentication. Standards such as FIDO2 and WebAuthn reduce dependence on passwords and lower phishing risk.
Early adopters are exploring:
- Biometric login for clinicians
- Hardware security keys
- Device-bound authentication
- Phishing-resistant MFA
- Continuous identity verification
While adoption is still growing, these approaches align well with Zero Trust strategies and future-ready EHR security architecture.
Strong authentication in EHR-integrated apps depends on choosing and combining the right standards. No single protocol solves every risk.
Therefore, healthcare enterprises must design identity flows deliberately, with interoperability, clinical usability, and regulatory alignment in mind.
Authentication Architecture Patterns Used by Large Health Systems
Large health systems typically use delegated EHR authentication, enterprise IDP models, Zero Trust access, or hybrid bridges. The right pattern depends on scale, legacy constraints, and risk tolerance within the EHR security architecture.
Healthcare organizations rarely rely on a single authentication model. Instead, they evolve through stages as their digital ecosystem grows. What works for a single hospital often fails at multi network scale. Therefore, mature enterprises adopt architecture patterns that balance security, usability, and operational control.
Below are the most common patterns seen across large EHR-integrated environments.
Pattern 1: EHR Delegated Authentication
In this model, the EHR platform handles primary user authentication. External clinical apps trust the EHR session through SMART on FHIR or similar launch flows.
This approach is common in environments that want tight EHR control with minimal identity duplication.
When organizations use it
- Early-stage digital ecosystems
- EHR-centric clinical workflows
- Limited third-party app footprint
- Smaller hospital networks
Risks to watch
- Limited flexibility outside the EHR
- Harder cross-platform governance
- Potential session over trust
- Dependency on EHR capabilities
In practice, this model works well initially. However, it can become restrictive as ecosystems expand.
Pattern 2: Enterprise Identity Provider Centric Model
Here, a centralized identity provider becomes the primary trust authority. The EHR and all connected apps rely on this shared identity layer.
This pattern is widely used in large health systems that operate complex multi-application environments.
When organizations use it
- Multi-hospital networks
- Large workforce populations
- Heavy third-party integrations
- Cloud and hybrid strategies
Risks to watch
- Higher upfront design effort
- Requires strong IAM maturity
- Integration complexity with legacy systems
- Change management challenges
Despite the effort, this model forms the backbone of modern EHR security architecture in large enterprises.
Pattern 3: Zero Trust Authentication Model
Zero Trust extends beyond basic login. It continuously verifies identity, device posture, and session risk throughout the user journey.
Healthcare organizations adopt this model when they need tighter control over distributed access.
When organizations use it
- Remote clinical workforce
- High-risk data environments
- Extensive API ecosystems
- Advanced security programs
Risks to watch
- Requires mature telemetry
- Higher operational complexity
- Potential clinician friction if poorly tuned
- Requires strong endpoint visibility
When implemented carefully, Zero Trust significantly strengthens enterprise resilience.
Pattern 4: Hybrid Legacy Bridge Model
Many health systems operate in transition. They maintain legacy authentication methods while gradually introducing modern identity controls.
This hybrid approach is often unavoidable in long-established hospital environments.
When organizations use it
- Heavy legacy EHR footprint
- Older clinical applications
- Phased modernization programs
- Budget-constrained transformations
Risks to watch
- Policy inconsistencies
- Hidden trust gaps
- Increased operational overhead
- Harder audit alignment
Without careful governance, hybrid environments can accumulate identity debt quickly.
There is no universal authentication pattern for every health system. The right approach depends on scale, legacy constraints, and risk posture.
However, organizations that treat authentication as a core layer of their EHR security architecture consistently achieve stronger protection and smoother digital growth. The key is to choose deliberately and evolve the model as the ecosystem expands.
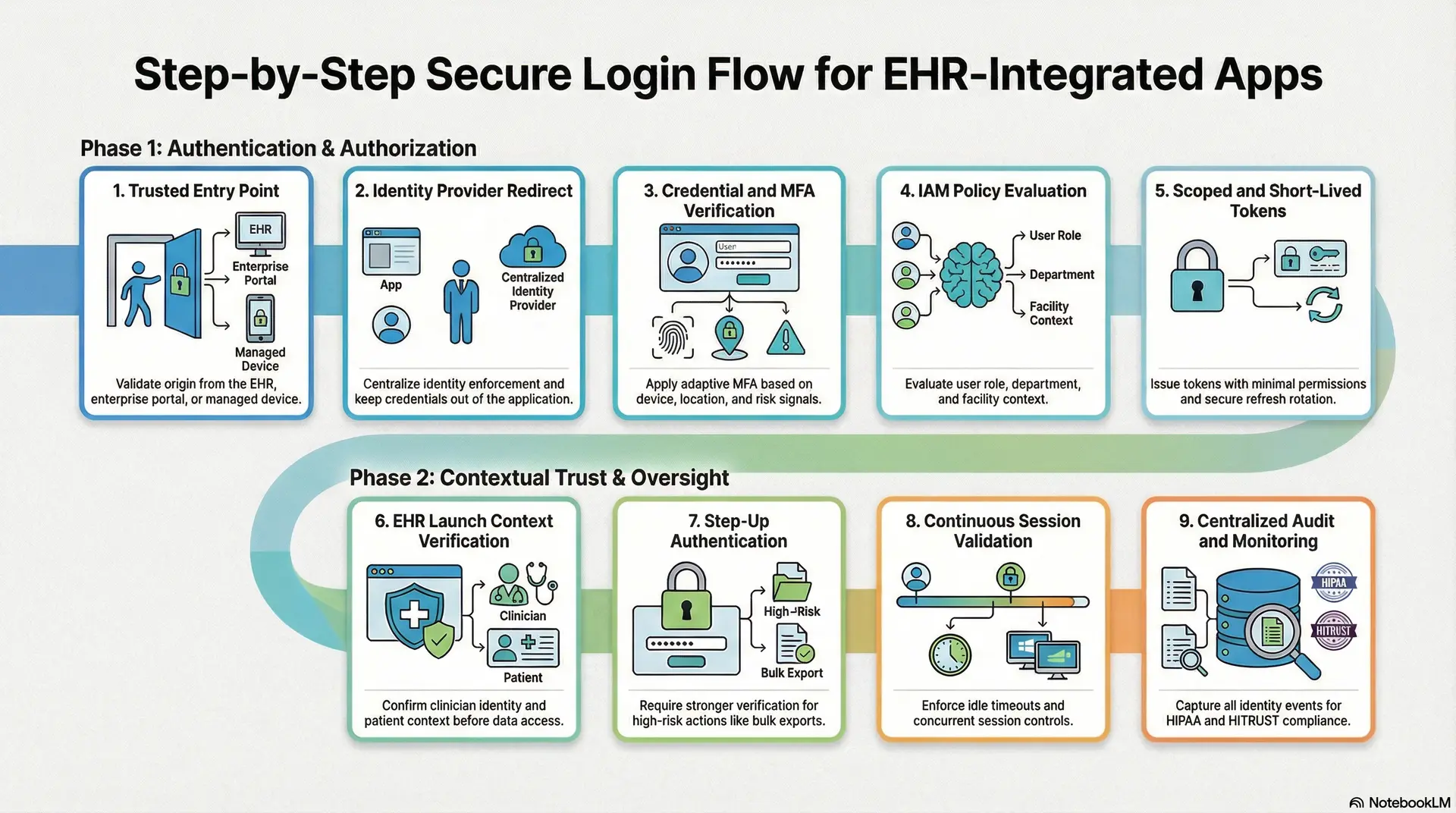
Step-by-Step Secure Login Flow for EHR-Integrated Apps
A secure login flow for EHR-integrated apps verifies identity, enforces MFA, issues scoped tokens, and continuously validates sessions. In addition, it logs every identity event for audit and incident response within the EHR security architecture.
At Intellivon, we design it as a governed identity workflow embedded directly into the EHR security architecture. As a result, access decisions stay consistent across web, mobile, and EHR-embedded experiences. Below is the step-by-step approach we implement in enterprise healthcare environments.
1. Access Starts With a Trusted Entry Point
Every secure session begins with controlled entry. Users typically start access from the EHR, an enterprise portal, or a managed device. Therefore, we validate the origin before the authentication flow proceeds. This early check helps block untrusted sources and reduces unnecessary exposure.
Common trusted entry points include:
- Launching the application from within the EHR
- Opening the app through a secure enterprise workspace
- Using a managed clinical workstation or mobile device
By enforcing entry validation, organizations reduce the risk of unauthorized session initiation.
2. The App Redirects to the Enterprise Identity Provider
In a mature EHR security architecture, the application does not authenticate users directly. Instead, it redirects the user to the approved identity provider. This separation keeps credentials out of the application layer and centralizes identity enforcement.
At this stage, the identity provider becomes responsible for:
- Credential validation
- MFA enforcement
- Conditional access policies
- Risk-based login decisions
Therefore, security teams gain a single control plane for identity governance.
3. The Identity Provider Verifies Credentials and MFA
Once redirected, the identity provider validates the user’s credentials. It then applies the appropriate multifactor authentication method based on risk signals. This step is critical because credential theft remains the leading breach vector in healthcare.
Intellivon typically enables adaptive MFA based on factors such as:
- Device management status
- User location
- Network trust level
- Access time patterns
- Sensitivity of requested data
As a result, clinicians experience minimal friction during normal workflows while high-risk access receives stronger verification.
4. IAM Policies Evaluate Role and Context
After successful authentication, the IAM layer evaluates what the user is allowed to do. This step ensures that identity verification is tightly connected to authorization controls.
In enterprise deployments, we validate:
- User role and department alignment
- Facility or care setting context
- Device posture and trust signals
- Time-based access restrictions
- Vendor or external user status
Therefore, access reflects real operational context instead of static role assignments.
5. The System Issues Scoped and Short-Lived Tokens
After policy validation, the identity system issues tokens that allow the application to access approved resources. Token hygiene is essential in EHR-integrated environments because tokens often travel across multiple services.
Intellivon enforces the following controls:
- Short token lifetimes
- Minimal permission scopes
- Audience restriction
- Secure refresh token rotation
Because of these controls, even if a token is exposed, the potential impact remains limited.
6. EHR Launch Context Is Verified Before Data Access
When apps launch from the EHR, context verification becomes essential. Many environments assume the launch is trustworthy, but this assumption can create hidden risk. Therefore, we validate the launch context before allowing any clinical data access.
This verification confirms:
- The authenticated clinician identity
- The correct patient context
- The approved workflow pathway
- The integrity of the launch request
As a result, the application does not blindly trust the upstream context.
7. Step-Up Authentication Protects High-Risk Actions
Not every action carries the same level of risk. Routine chart review should remain fast. However, sensitive actions require stronger verification. Therefore, Intellivon implements step-up authentication for high-risk events.
Typical triggers include:
- Bulk record exports
- Sensitive document downloads
- Administrative configuration changes
- Privileged clinical workflows
This approach balances usability with strong protection.
8. Sessions Remain Protected Through Continuous Validation
Authentication cannot end at login. Clinical sessions often stay active for long periods, especially on shared workstations. Therefore, continuous session protection is essential.
We typically enforce:
- Idle session timeouts
- Absolute session duration limits
- Device binding is supported
- Risk-based re-authentication
- Concurrent session controls for privileged users
These controls help prevent silent session misuse during busy clinical shifts.
9. Identity Events Feed Centralized Audit and Monitoring
Finally, every authentication event must be visible to security and compliance teams. Without strong telemetry, even well-designed controls lose effectiveness. Therefore, Intellivon centralizes identity logging across the ecosystem.
We capture and correlate:
- Identity provider events
- Token issuance and refresh activity
- EHR launch validations
- Step-up authentication triggers
- Policy denials and anomalies
In addition, we align logs to HIPAA and HITRUST audit expectations so organizations can respond quickly during investigations.
Intellivon builds authentication as a governed identity layer within the EHR security architecture. As a result, healthcare organizations reduce credential-based exposure, improve audit readiness, and scale digital care with greater confidence.
Role-Based and Attribute-Based Access in Clinical Contexts
Role-Based Access Control assigns permissions based on user roles, while Attribute-Based Access Control evaluates context such as location, device, and patient relationship. Modern EHR security architecture often combines both models to improve precision and reduce over-privileged access.
Organizations that modernize this layer strengthen both security posture and operational clarity across the EHR security architecture.
1. How Role-Based Access Control Works in Hospitals
RBAC grants permissions based on a user’s defined role. Most hospitals begin here because the model is straightforward and relatively easy to manage. For example, physicians receive broader clinical access, while billing teams see financial data.
In practice, RBAC typically supports roles such as:
- Attending physician
- Staff nurse
- Revenue cycle specialist
- Clinical administrator
- External vendor user
When implemented correctly, RBAC simplifies provisioning and supports consistent policy enforcement. It also aligns well with HR-driven onboarding workflows. However, RBAC alone often struggles in complex care environments.
Over time, many organizations experience role inflation. Users accumulate access that no longer reflects their current responsibilities. As a result, over-privileged accounts quietly expand the attack surface. In large networks, this risk compounds across integrated applications.
2. Where Attribute-Based Access Control Adds Precision
Attribute-Based Access Control, or ABAC, evaluates additional context before granting access. Instead of relying only on the job role, the system examines the conditions surrounding the request. Therefore, access decisions become more precise and adaptive.
Common attributes used in healthcare environments include:
- User location or facility
- Device trust level
- Time of access
- Patient relationship
- Network risk signals
For example, a physician may have full chart access inside the hospital but limited access when working remotely. Similarly, a traveling clinician may receive permissions only for assigned patients. These controls significantly reduce unnecessary exposure.
ABAC also supports Zero Trust initiatives because it evaluates risk continuously. However, ABAC alone can become difficult to manage at enterprise scale. Without strong governance, policy sprawl can introduce operational complexity.
3. Why Leading Health Systems Use Hybrid RBAC and ABAC
Most mature healthcare organizations now combine RBAC and ABAC. This hybrid model delivers both operational simplicity and contextual precision. RBAC provides the structural foundation, while ABAC adds real-time intelligence.
In a well-designed EHR security architecture:
- RBAC defines baseline permissions
- ABAC refines access based on context
- IAM policies enforce both layers consistently
- Identity telemetry feeds continuous risk evaluation
This approach solves several common problems. It reduces privilege creep, improves audit confidence, and supports flexible clinical workflows. In addition, it aligns well with modern interoperability and remote care models.
From an executive perspective, the hybrid model also improves governance visibility. Security teams gain clearer insight into who accessed what and under which conditions. Meanwhile, clinicians experience fewer unnecessary access barriers.
Organizations that combine RBAC and ABAC within their EHR security architecture achieve stronger protection without slowing care delivery. This balance is becoming essential as healthcare environments grow more connected and more scrutinized.
Multi-Factor Authentication Strategies That Actually Work In These Apps
Effective MFA in EHR-integrated apps balances strong identity proofing with clinical speed. Healthcare leaders prioritize adaptive MFA, phishing-resistant methods, and workflow-aware enforcement within the EHR security architecture.
Therefore, the goal is to apply the right level of assurance at the right moment. In high-performing environments, MFA protects sensitive access without slowing care delivery. Below are the strategies that consistently work in real healthcare settings.
1. Use Adaptive MFA Instead of One-Size-Fits-All Controls
Traditional MFA forces the same challenge every time. In clinical environments, this approach quickly creates frustration and workarounds. Therefore, leading organizations use adaptive MFA that adjusts based on risk signals.
The system evaluates context such as:
- Device trust status
- User location
- Network risk level
- Access time patterns
- Sensitivity of requested data
When risk is low, clinicians move quickly. However, when risk rises, the system automatically requires stronger verification. This balance improves both security and usability across the EHR security architecture.
2. Prioritize Phishing-Resistant Authentication Methods
Not all MFA methods offer the same level of protection. SMS codes and basic push approvals are easier to bypass through modern phishing attacks. Therefore, healthcare enterprises are shifting toward phishing-resistant approaches.
Stronger options include:
- Biometric verification on trusted devices
- Hardware security keys
- FIDO2-based authentication
- Certificate-based device trust
- Secure badge tap integrations
These methods significantly reduce the success rate of credential-based attacks. In addition, they align well with Zero Trust identity strategies.
3. Align MFA With Clinical Workflow Realities
Security controls must respect the pace of care delivery. If MFA interrupts critical workflows, clinicians will look for ways around it. Therefore, successful programs design MFA around how care teams actually work.
Effective implementations often include:
- Single MFA at shift start on trusted workstations
- Reduced prompts inside secure hospital networks
- Faster re-authentication for chart review
- Step-up MFA only for high-risk actions
- Support for shared workstation environments
This workflow-aware design maintains strong protection without introducing clinical friction.
4. Apply Step-Up Authentication for Sensitive Actions
Not every activity requires the same assurance level. Routine chart access should remain fast. However, high-risk actions demand stronger verification. Therefore, step-up authentication plays a critical role.
Common triggers include:
- Bulk record exports
- Sensitive patient data access
- Administrative privilege changes
- External data sharing
- Vendor remote sessions
By applying MFA selectively, organizations protect high-risk moments while preserving daily efficiency.
5. Monitor and Tune MFA Continuously
MFA is not a set-and-forget control. Threat patterns, workforce behavior, and access models continue to evolve. Therefore, mature health systems continuously monitor MFA performance and adjust policies.
Key operational practices include:
- Reviewing MFA bypass attempts
- Tracking user friction metrics
- Monitoring unusual login patterns
- Updating risk scoring models
- Aligning controls with new compliance expectations
Continuous tuning ensures the MFA program remains effective as the environment grows.
However, those that implement adaptive, phishing-resistant MFA within their EHR security architecture achieve stronger protection and smoother clinical operations. As digital care expands, this balance becomes essential for both risk management and sustainable growth.
Common Authentication Mistakes in EHR Integrations
Many EHR-integrated apps fail due to over-trusted SSO, weak session controls, and fragmented identity governance. Leading organizations fix these gaps by centralizing identity, enforcing adaptive MFA, and continuously validating access within the EHR security architecture.
Below are the mistakes we see most often and how Intellivon helps enterprises correct them.
Mistake 1: Treating SSO Success as Full Security Coverage
Many teams assume that if single sign-on works, the application is secure. However, SSO only confirms that the user authenticated once. It does not guarantee proper session validation, context checks, or ongoing risk evaluation.
This false confidence often leaves downstream apps over-trusting the session.
How Intellivon fixes it
- Add post-login policy validation at the application layer.
- Enforce token scope and audience checks on every request.
- Implement continuous session monitoring tied to risk signals.
- Align SSO flows with Zero Trust identity principles.
As a result, authentication becomes a governed process rather than a one-time event.
Mistake 2: Allowing Privilege Creep Across Clinical Systems
Over time, users often accumulate access rights they no longer need. This usually happens because role reviews are infrequent and identity lifecycle controls are weak. Consequently, many EHR-integrated environments carry significant over-privileged access.
This exposure increases both insider risk and breach impact.
How Intellivon fixes it
- Implement automated role recertification workflows.
- Align RBAC baselines with real clinical job functions.
- Add ABAC context checks for sensitive access.
- Integrate identity lifecycle events with HR systems.
Therefore, access stays tightly aligned with current responsibilities.
Mistake 3: Weak Token and Session Hygiene
Many applications still rely on long-lived tokens and loosely managed sessions. Attackers actively look for these gaps because stolen tokens often bypass login controls entirely.
In busy clinical environments, poor session controls can persist unnoticed for months.
How Intellivon fixes it
- Enforce short-lived access tokens by default.
- Enable secure refresh token rotation.
- Apply device binding where supported.
- Implement idle and absolute session timeouts.
- Monitor for abnormal token reuse patterns.
These controls significantly reduce the value of stolen credentials.
Mistake 4: Ignoring Clinical Workflow Realities in MFA Design
Some organizations deploy MFA in ways that disrupt care delivery. When prompts appear too frequently or at the wrong moments, clinicians create workarounds. Over time, this weakens the entire control model.
Security that fights workflow rarely succeeds.
How Intellivon fixes it
- Deploy adaptive MFA based on contextual risk.
- Reduce prompts on trusted clinical networks.
- Enable step-up authentication only for high-risk actions.
- Support badge tap and biometric options where appropriate.
- Continuously tune policies using real usage data.
This approach strengthens protection without slowing clinical teams.
Mistake 5: Fragmented Identity Governance Across Applications
In many health systems, each application team manages authentication slightly differently. Although each system may pass review individually, the overall identity posture becomes inconsistent.
This fragmentation creates blind spots across the EHR security architecture.
How Intellivon fixes it
- Centralize identity enforcement through the enterprise IdP.
- Standardize authentication flows across all integrated apps.
- Unify audit logging and identity telemetry.
- Align policies across cloud, on-prem, and hybrid systems.
- Establish governance guardrails for third-party integrations.
As a result, organizations gain consistent visibility and control.
Mistake 6: Limited Visibility Into Authentication Events
Many environments generate logs but fail to correlate them. Without centralized visibility, security teams struggle to detect early warning signs.
This delay increases dwell time during credential-based attacks.
How Intellivon fixes it
- Stream identity telemetry into centralized monitoring platforms.
- Correlate login, token, and EHR launch events.
- Enable real-time anomaly detection.
- Align logging with HIPAA and HITRUST audit needs.
- Build dashboards for both security and compliance teams.
Therefore, organizations can detect and respond faster.
Healthcare organizations that address these issues systematically strengthen both security posture and operational resilience. By embedding disciplined identity controls into the EHR security architecture, enterprises reduce breach risk and create a safer foundation for digital growth.
Conclusion
Secure authentication is now a strategic requirement for any organization running EHR-integrated apps. Weak identity controls no longer create isolated risk. Instead, they expose the entire clinical ecosystem.
Therefore, healthcare enterprises must treat authentication as a core layer of their EHR security architecture. When designed correctly, it protects patient data, improves audit confidence, and supports a safe digital scale.
Intellivon helps health systems modernize identity with enterprise-grade, AI-driven solutions built for real clinical environments. Partner with Intellivon to strengthen access controls, reduce breach exposure, and enable confident growth across your connected healthcare ecosystem.
Build Secure EHR-Integrated Applications With Intellivon
At Intellivon, secure EHR-integrated applications are engineered as a governed clinical identity infrastructure, not login layers added onto disconnected systems. Every architectural and delivery decision focuses on clinical workflow alignment, strong access governance, and long-term operational resilience across the EHR security architecture.
As digital health ecosystems expand across hospitals, partner networks, and patient-facing platforms, consistency becomes essential. Identity controls, session integrity, and audit visibility must remain stable even as user volumes, API traffic, and integration complexity grow. This disciplined approach helps healthcare organizations scale innovation without reopening hidden access risks or compliance exposure.
Why Partner With Intellivon?
- Enterprise-grade identity architecture purpose-built for EHR-integrated healthcare environments
- Proven delivery across multi-hospital, multi-EHR, and high-scale clinical ecosystems
- Compliance-by-design framework with embedded audit readiness and policy enforcement
- Secure, modular platform supporting cloud, hybrid, and on-prem deployments
- AI-ready identity foundation enabling adaptive authentication and risk-aware access controls
Book a strategy call to explore how Intellivon can help you design and scale secure EHR-integrated applications with confidence, control, and long-term enterprise value.
FAQs
Q1. What is secure authentication in EHR-integrated applications?
A1. Secure authentication in EHR-integrated applications verifies user identity before granting access to clinical data. It typically combines single sign-on, multifactor authentication, and token-based controls. When implemented correctly within the EHR security architecture, it reduces unauthorized access and strengthens audit readiness across connected healthcare systems.
Q2. Why is MFA critical for EHR-connected healthcare apps?
A2. MFA is critical because stolen credentials remain a leading cause of healthcare breaches. A second verification factor significantly reduces unauthorized access risk. In addition, modern healthcare environments use adaptive MFA to protect sensitive workflows without slowing clinicians during routine patient care activities.
Q3. How does SMART on FHIR improve authentication security?
A3. SMART on FHIR improves security by using OAuth 2.0 and OpenID Connect to control how apps access EHR data. It issues scoped, time-limited tokens instead of exposing user credentials. Therefore, organizations gain better control over third-party app access within the EHR security architecture.
Q4. What is the difference between RBAC and ABAC in healthcare systems?
A4. RBAC grants access based on predefined user roles such as physician or nurse. ABAC goes further by evaluating context like location, device trust, and patient relationship. Most large health systems combine both models to improve precision while maintaining manageable identity governance.
Q5. When should healthcare organizations modernize their authentication architecture?
A5. Organizations should modernize when they expand digital health tools, enable remote access, integrate third-party apps, or face rising audit pressure. These changes increase identity risk. Therefore, strengthening authentication early helps reduce breach exposure and supports secure enterprise growth.