Identity is the backbone of every enterprise, and yet in most organizations, it is also the weakest link. Centralized identity leads to single points of failure, wherein one outage can paralyze operations, and one breach can result in a systemic crisis. The 2023 Okta incident proved this when attackers gained access to sensitive support user data across virtually all of Okta’s customers, leaving enterprises exposed to phishing, impersonation, and operational disruption. This is the flaw of centralized identity, where risk and trust are concentrated in one fragile hub. The sustainable alternative is decentralized identity management systems, where credentials are issued as verifiable proofs, held securely in digital wallets by employees, customers, and partners, and anchored on blockchain for tamper-proof verification.
We have delivered measurable results through our customized decentralized identity management systems by streamlining onboarding processes, reducing compliance costs, and enabling organizations to improve trust and efficiency across their ecosystems. In this blog, we will explore how we build these enterprise-grade platforms from the ground up to be secure, compliant, and future-ready.
What is a Decentralized Identity (DID) Management System?
A decentralized identity management system is a way of handling digital identities without relying on a single central authority. Instead of storing all employee, customer, or partner credentials in one database, which can be hacked or taken offline, identities are distributed and cryptographically verifiable.
In this model, three roles define the flow of trust:
- Issuer: The entity that creates and signs an identity credential. For enterprises, this could be HR issuing an employee badge, a regulator issuing a compliance certificate, or a bank providing KYC verification.
- Holder: The individual or system that stores the credential in a secure wallet. This wallet can live on a mobile device, desktop, or enterprise agent.
- Verifier: The application, partner, or service that checks the credential when access or proof is needed. For example, a supplier portal verifies that a user is an authorized buyer.
What makes this different from today’s identity systems is how trust is anchored. With decentralized identity, the credential itself is verifiable through blockchain-backed signatures, which means a verifier doesn’t need to “call home” to the issuer every time. This design reduces dependency, increases privacy, and makes verification faster and more reliable.
The enterprise no longer carries the burden of storing and protecting every piece of personal data. Instead, it verifies only what it needs, when it needs it.
Market Insights on Decentralized Identity (DID) in Enterprises
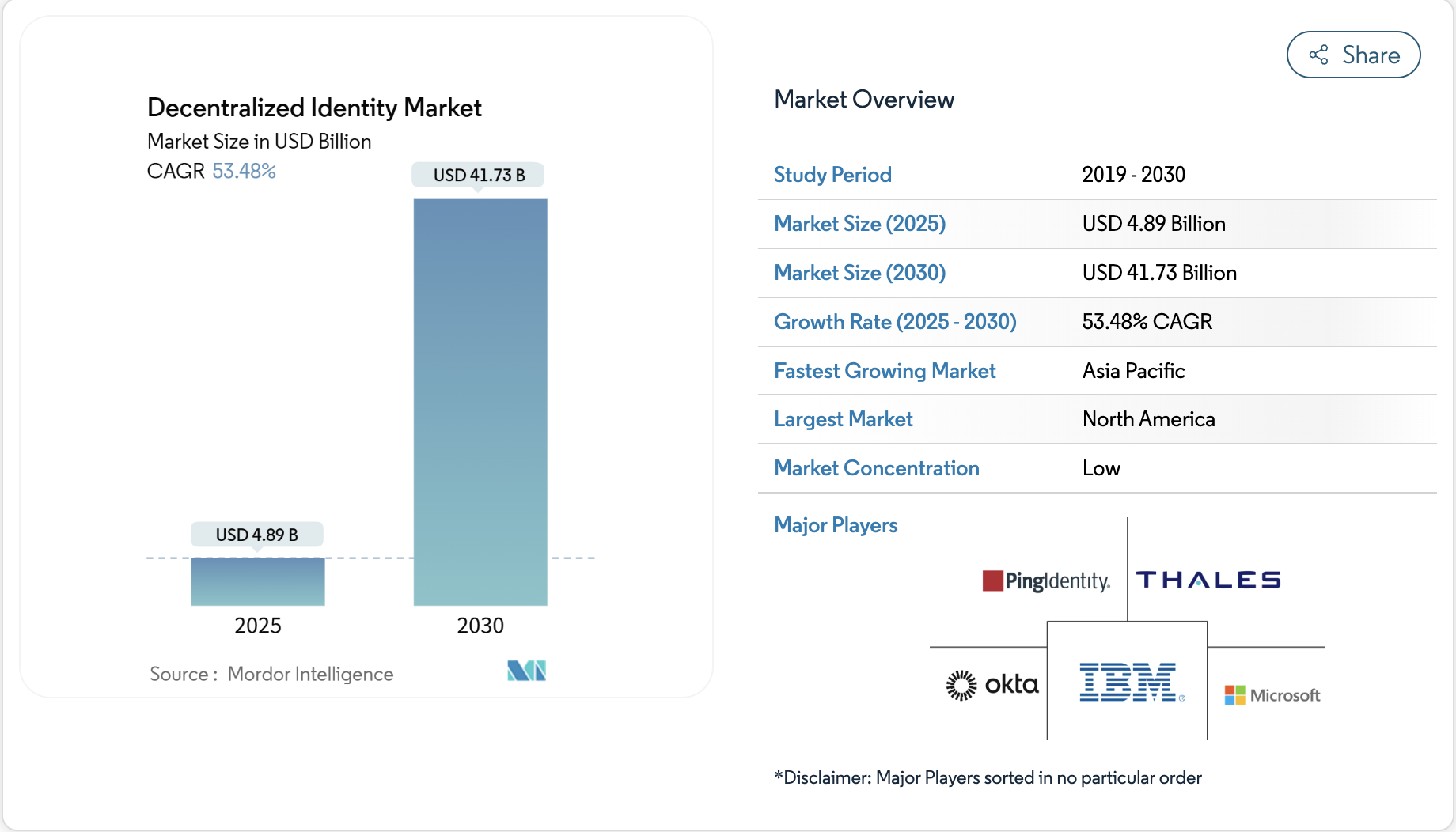
The decentralized identity market is experiencing rapid growth as enterprises demand stronger security, greater privacy, and user-controlled digital identity solutions. The decentralized identity market size reached USD 4.89 billion in 2025 and is projected to advance to USD 41.73 billion by 2030, translating into a robust 53.48% CAGR over the forecast horizon. This trajectory underscores decentralized identity as one of the fastest-growing areas in enterprise technology.
Key Growth Drivers:
- Regulatory mandates such as eIDAS 2.0 in Europe, NIST standards in the U.S., and HIPAA are driving the adoption of verifiable enterprise identities.
- Expansion of digital ecosystems is demanding seamless, cross-border identity verification.
- Enterprise adoption of blockchain and cryptographic technologies enabling self-sovereign identity (SSI) and decentralized identifiers (DIDs).
- New use cases in IoT device identity, AI autonomous agents, remote work, and privacy-first access control.
- Enterprises focus on reducing risk from identity fraud, cyberattacks, and data breaches.
Market Segmentation Highlights:
- Large enterprises dominate with a 60% share, led by financial services, healthcare, telecom, government, and e-commerce.
- SMBs are adopting rapidly with higher growth rates thanks to agility and customer-focused identity strategies.
- Non-biometric solutions are gaining traction, enabling flexible authentication without storing sensitive biometrics.
- North America leads adoption, followed by Europe, with Asia-Pacific showing accelerating momentum.
With regulatory support, expanding use cases, and maturing technology, enterprise adoption of DID will continue to accelerate, offering a scalable, interoperable, and privacy-preserving framework for digital identity.
Why Enterprises Need Decentralized Identity Management Systems
When identity systems break down, business continuity is disrupted, compliance obligations are jeopardized, and operational efficiency suffers. This is why enterprises are turning to decentralized identity management, not for novelty, but to solve pressing challenges across governance, security, and scale.
1. Security for Core Operations
Enterprises can’t afford downtime or widespread compromise when a single provider fails. These systems anchor trust in verifiable credentials, ensuring continuity even if one system is breached or offline. This reduces systemic exposure and strengthens enterprise-wide resilience.
2. Compliance Alignment with Mandates
With GDPR, HIPAA, SOX, and eIDAS 2.0, compliance failures now translate into heavy fines and reputational loss. DID enables enterprises to issue and verify credentials with audit-ready proofs and selective disclosure, embedding compliance directly into identity workflows.
3. Cost Reduction in Identity
Password resets, repetitive KYC, and redundant access checks are hidden cost drains. The system eliminates these inefficiencies, lowering IT support costs, reducing onboarding overhead, and freeing resources for higher-value projects.
4. Scalable Trust
Global enterprises depend on thousands of suppliers, partners, and regulators. DID creates a secure trust fabric where verifiable credentials can be exchanged across organizational boundaries, accelerating collaboration and reducing manual verification delays.
5. Governance and Risk Control
Enterprise leaders need confidence that identity policies are enforceable and auditable. A decentralized identity management system provides a framework where issuance, revocation, and verification are governed by cryptographic proofs and registries, reducing the risk of insider abuse or policy drift.
Centralized identity has reached its limits in today’s compliance-heavy, security-first, globally connected enterprise environment. Decentralized identity offers a new operating model that is resilient, compliant, cost-efficient, and scalable.
How Decentralized Identity Management Systems Work
For most enterprises, identity and access management (IAM) is already in place. Employees authenticate through Active Directory, partners use federated logins, and customers rely on centralized providers. But these systems carry a high risk, because one breach or outage cascades across the enterprise. Decentralized identity management doesn’t replace IAM, but it enhances it by adding a new layer of verifiable, distributed trust that integrates with existing workflows.
1. Issuers Within Enterprise
In decentralized identity, trusted authorities issue credentials. For enterprises, this could be HR generating employee IDs, compliance teams certifying access privileges, or regulators confirming licenses. Each credential is cryptographically signed, creating a proof that can be trusted without checking a central database.
2. Holders Across Workforce
Credentials don’t sit in a central repository, but they are stored by holders in secure wallets. These holders can be employees, contractors, suppliers, or even enterprise systems and IoT devices. The wallet ensures that credentials are under the control of the rightful owner while remaining instantly verifiable.
3. Verifiers at Access Points
When access is requested, the verifier, which can be a business application, a supplier portal, or a regulator, checks the credential against blockchain-anchored trust records. No sensitive data is stored or transmitted unnecessarily, and verification happens in seconds. This reduces dependency on a single IAM provider while strengthening access assurance.
4. Blockchain as Trust Anchor
Blockchain is not used to store personal data, but to anchor decentralized identifiers (DIDs), public keys, and revocation registries. This provides a tamper-proof trust fabric that allows credentials to be validated consistently across enterprise systems and global networks.
5. Integration with IAM Systems
Enterprises don’t abandon their IAM investments. DID feeds into IAM policies, mapping verifiable credentials to existing role-based (RBAC) or attribute-based (ABAC) access controls. This hybrid approach ensures business continuity while extending IAM with resilience, compliance, and scalability.
Decentralized identity systems succeed in the enterprise because they don’t reinvent access control, but more so because they strengthen it. By combining issuers, holders, and verifiers with blockchain as the trust anchor, enterprises gain a scalable identity model that is secure, compliant, and ecosystem-ready.

Key Standards for Integrating DIDs with Enterprise IAM
For decentralized identity to work in real enterprise environments, it can’t exist in a silo. It must integrate with the systems organizations already use for authentication, access control, and compliance reporting. This is where global standards and protocols act as the “translation layer,” ensuring decentralized identity works seamlessly alongside IAM, cloud platforms, and partner networks.
1. W3C Decentralized Identifiers (DIDs)
The World Wide Web Consortium (W3C) defines the structure of decentralized identifiers. A DID is a globally unique identifier that links to public keys and metadata on a blockchain. It allows enterprises to recognize and verify identities without relying on a central directory.
2. Verifiable Credentials (VCs)
Also standardized by W3C, Verifiable Credentials are digital equivalents of trusted documents, such as employee badges, compliance certificates, or supplier attestations. They are signed by issuers, held by users, and presented to verifiers with cryptographic assurance that they haven’t been tampered with.
3. OpenID (OIDC4VCI & OIDC4VP)
Most enterprises already use OpenID Connect for logins. These new extensions bridge decentralized identity with existing SSO flows. They allow verifiable credentials to be issued (VCI) and presented (VP) through the same login protocols enterprises know, reducing friction for IT teams.
4. DIDComm
DIDComm provides a protocol for secure, private communication between enterprise systems. It enables credentials and proofs to be exchanged between agents, partners, or applications without exposing data to intermediaries.
5. Trust Registries
Standards alone aren’t enough, because enterprises also need governance. Trust registries define which issuers are recognized and under what rules. For example, a financial consortium may create a registry of trusted KYC issuers. This prevents fraudulent credentials and ensures interoperability across industries.
At Intellivon, our engineers have built production systems using OpenID4VC flows, mapped verifiable credentials to IAM policies, and designed trust registries aligned with EU eIDAS 2.0 and U.S. NIST frameworks. This ensures that when enterprises deploy decentralized identity, it is both standards-compliant and regulator-ready.
Leading Use Cases for Decentralized Identity Management Systems
Enterprises across industries are already deploying decentralized identity management systems to solve pressing problems in security, compliance, and ecosystem trust. Below are leading sectors where DID is transforming operations, with practical use cases and enterprise examples that highlight its impact.

1. Financial Services
Financial institutions face growing pressure to reduce fraud, streamline onboarding, and stay ahead of evolving KYC and AML regulations. Decentralized identity offers a faster, safer way to establish trust across global financial ecosystems.
A. Customer KYC Onboarding
Banks can issue reusable, verifiable KYC credentials once, allowing customers to use them across services without repeating document checks. This reduces onboarding time from weeks to days.
B. Fraud Prevention
With DID, credentials are cryptographically signed and instantly verifiable. This eliminates reliance on easily forged documents and reduces exposure to phishing and account takeover attacks.
C. Cross-Border Compliance
Global transactions often stall on regulatory checks. Decentralized identity enables cross-jurisdictional verification of credentials, helping banks meet local compliance standards without duplicating checks.
Enterprise Example: BBVA
Spanish banking giant BBVA has experimented with decentralized identity models to streamline customer onboarding and enable cross-border KYC verification, showing how major financial institutions are preparing for scalable DID adoption.
2. Healthcare
Healthcare enterprises struggle with securing patient records, proving compliance, and reducing administrative overhead in a heavily regulated environment. DID brings trust and portability to identity management in healthcare ecosystems.
A. Patient Record Access
Hospitals can issue verifiable credentials that prove patient identity, allowing secure access to health records across multiple systems without redundant registrations.
B. Insurance Verification
Insurance providers can verify patient eligibility instantly using decentralized credentials, eliminating manual claim checks and accelerating approvals.
C. Workforce Credentialing
Doctors, nurses, and staff often work across facilities. DID enables portable credentials for licenses, certifications, and role-based access, reducing delays and compliance gaps.
Enterprise Example: Mayo Clinic
Mayo Clinic has participated in pilots exploring blockchain-based decentralized identity to improve interoperability between hospitals and insurers, reflecting how healthcare leaders are preparing for verifiable patient and workforce credentials.
3. Supply Chain and Manufacturing
Supply chains rely on trust between multiple stakeholders, from manufacturers and distributors to logistics providers and auditors. DID enhances traceability and authenticity across global networks.
A. Supplier Certification
Suppliers can present verifiable credentials proving compliance with ESG, ISO, or safety standards. Manufacturers instantly validate authenticity without manual document exchanges.
B. Product Provenance
DID credentials tied to goods can prove authenticity across the supply chain, reducing counterfeiting and improving transparency for regulators and customers.
C. Logistics and Customs Clearance
Logistics providers can use verifiable identity credentials to speed up border checks and customs clearance, reducing delays and fraud.
Enterprise Example: IBM Food Trust
IBM’s Food Trust platform has used blockchain and verifiable credentials to track and validate food supply chains, giving manufacturers and retailers end-to-end visibility and trust.
4. Government and Public Sector
Governments face pressure to deliver secure, privacy-first identity systems that citizens can use across services. DID enables interoperability and trust at scale.
A. Digital Citizen IDs
Governments can issue verifiable digital IDs that citizens use across tax, healthcare, and education services while retaining control of personal data.
B. Cross-Border Recognition
With DID, credentials can be verified internationally, enabling seamless travel, work permits, or education validation.
C. Public Workforce Access
Government employees and contractors can use DID credentials for secure role-based access, ensuring compliance across agencies.
Enterprise Example: European Union eIDAS 2.0 Wallets
The EU is rolling out eIDAS 2.0 digital identity wallets, which will allow citizens and enterprises to share verifiable credentials across all member states, which is a major milestone in global DID adoption.
From faster KYC and safer patient records to trusted supplier verification and interoperable citizen services, DID solves real-world problems that centralized identity cannot. At Intellivon, we translate these use cases into enterprise-ready deployments, helping organizations move from pilot to production with measurable results.

Must-Have Features of a Decentralized Identity Management System
For enterprises, decentralized identity is an operational framework that has to integrate with legacy systems, withstand regulatory scrutiny, and deliver measurable ROI. Through Intellivon’s deployments across industries, several non-negotiable features emerge as critical for success.
1. Interoperability with Existing IAM
A DID system must complement, not replace, current IAM investments. That means seamless mapping of verifiable credentials into Active Directory, Okta, or Azure AD policies. Without this bridge, enterprises face costly rip-and-replace scenarios that stall adoption.
2. Fine-Grained Access Control
It’s not enough to verify who someone is, but enterprises need to manage what they can access. DID platforms must translate credential attributes into granular access rights (RBAC/ABAC), ensuring employees, contractors, and partners receive appropriate privileges without overexposure.
3. Selective Disclosure
Executives know regulators won’t tolerate overexposure of personal data. DID must support selective disclosure, where only the minimum proof required is shared, for e.g., proving a supplier is certified without revealing every document. This reduces compliance risk and audit burdens.
4. Lifecycle Management
A credential without lifecycle controls is a liability. Enterprises must be able to issue, suspend, and revoke credentials dynamically. For example, an offboarded employee’s wallet should instantly lose access rights while leaving other credentials intact.
5. Trust Registries and Governance
DID systems fail without governance. This is why trust registries are essential for defining which issuers are recognized in a given ecosystem, and whether by regulators, industry consortia, or internal compliance teams. This prevents fraudulent credentials and ensures interoperability across industries.
6. High-Availability Architecture
Enterprise-grade DID platforms need fault-tolerant, multi-region architectures that ensure credential verification continues even during provider downtime. Blockchain anchors help, but the surrounding systems must be equally resilient.
7. Integration with Regulatory Frameworks
Regulated industries demand more than cryptographic proofs and need systems that align with GDPR, HIPAA, SOX, and eIDAS 2.0. DID must embed compliance into workflows, with audit-ready logs and policy mapping that regulators can verify.
8. Enterprise-Grade Wallet Management
Wallets are enterprise assets, and DID systems must support both custodial and non-custodial wallet models. These wallets should feature enterprise recovery policies, key management, and multi-device access for workforce and ecosystem users.
9. Analytics and Monitoring Dashboards
Identity is also a governance issue. DID platforms should provide dashboards that track credential usage, revocation events, and anomalies. Enterprises need visibility to detect abuse, prepare audits, and prove compliance at board and regulator levels.
Intellivon’s Feature-First Approach
Our systems at Intellivon are hardened architectures that integrate with IAM, enforce compliance, and scale across global partner ecosystems. This is why clients in finance, healthcare, and supply chains trust us to deploy DID systems that deliver measurable, regulator-ready results.
How We Develop an Enterprise Decentralized Identity Management System
Building a decentralized identity management system inside an enterprise to align compliance, security, and operational workflows with a new model of trust. Based on Intellivon’s experience across industries, here is a phased approach that helps enterprises deploy DID systems without disrupting business continuity.

1. Defining Use Cases
Every project begins with enterprise priorities. We identify high-impact use cases, such as workforce access, supplier certification, and customer onboarding, and map them directly to measurable outcomes.
Faster onboarding, reduced audit costs, and fraud prevention aren’t abstract benefits; they become the ROI anchors that secure executive buy-in.
2. Selecting DID Methods
No two enterprises need the same DID model. We evaluate whether public, consortium, or permissioned blockchains best suit the client’s compliance and industry environment.
For instance, financial services clients often require permissioned networks for strict regulatory control, while manufacturers benefit from consortium-led frameworks that support cross-border supply chains.
3. Designing Wallet Infrastructure
Wallets are the backbone of decentralized identity adoption. We architect custodial models for regulated industries (managed by the enterprise for employees or contractors) and hybrid or non-custodial options where user control is critical.
Recovery policies, device support, and compliance requirements are built into wallet design from day one.
4. Integrating with IAM
DID doesn’t replace IAM, but it makes it stronger. Our architectures map verifiable credentials into IAM policies (RBAC/ABAC), so access rights are enforced at a granular level.
Employees, partners, and contractors get the access they need, while enterprises maintain continuity with Active Directory, Okta, or Azure AD.
5. Embedding Governance
A DID platform without governance becomes unmanageable. We implement trust registries, credential lifecycle policies, and revocation frameworks aligned with regulators.
This ensures credentials are auditable, revocable, and compliant in real time, and don’t just exist.
6. Piloting in Controlled Environments
We roll out pilots in contained domains, such as a business unit, a supplier ecosystem, or a compliance-driven workflow.
These pilots validate usability, revocation speed, and IAM integration while surfacing cultural and operational blockers before wider rollout.
7. Scaling Across Ecosystems
Once proven, we expand DID platforms to external stakeholders, such as partners, regulators, and global suppliers. This stage is where decentralized identity evolves from an internal system to a trust fabric that spans across borders and industries.
Decentralized identity is an enterprise transformation. At Intellivon, we build these systems as part of your strategic fabric, aligning technology with compliance, governance, and business goals. With our phased approach, identity moves from a point of vulnerability to a scalable advantage that drives resilience, trust, and long-term growth.
Overcoming Challenges To Deploy a Decentralized Identity Management System
Deploying decentralized identity inside a large enterprise isn’t about installing a wallet and flipping a switch. The real obstacles appear in governance, integration, and adoption at scale, which are areas that most blogs skip over, but which determine whether a project succeeds or stalls.
1. Wallets That Don’t Fit Enterprise Reality
Most SSI wallets on the market are designed for consumers, not enterprises. They lack recovery models, shared device access, or the ability to enforce enterprise key custody policies. For regulated industries, this makes them unusable.
Intellivon Insight: We’ve built hybrid wallet infrastructures where employees use enterprise-issued custodial wallets with automated recovery tied to HR offboarding workflows, while contractors or partners can use non-custodial wallets under defined trust registries. This balance ensures adoption without sacrificing compliance or usability.
2. IAM Integration Without Disruption
Enterprises can’t afford to “rip and replace” IAM systems. But mapping DID credentials into IAM isn’t trivial. You need to translate verifiable credentials into RBAC/ABAC policies that legacy IAM understands.
Intellivon Insight: In our deployments, we built middleware agents that interpret DID claims and feed them into Active Directory group memberships dynamically. For example, a supplier credential marked as “ISO-certified” auto-maps into an access role for procurement portals. This turns credentials into live IAM attributes, not static proofs.
3. Regulatory Uncertainty and Audit Readiness
Most pilots fail because they underestimate regulatory audit complexity. It’s not enough to show cryptographic proofs, but auditors want lineage, revocation history, and contextual policies.
Intellivon Insight: We design DID platforms with dual audit trails: one cryptographic (on-chain proofs) and one human-readable (enterprise audit dashboards). This gives regulators what they need in the language they understand, without exposing sensitive data. In one healthcare client, this reduced audit prep time by 30% because auditors could validate proofs without combing through raw blockchain logs.
4. Cultural Resistance in IAM
IAM admins see DID as “extra complexity,” while compliance officers fear regulatory gaps. Resistance is less about the tech and more about trust in the governance model.
Intellivon Insight: We’ve overcome this by embedding DID into existing IAM workflows invisibly. For example, employees still “log in” as usual, but behind the scenes, DID credentials are being verified. Admin dashboards look familiar but include DID credential events. This approach reduces resistance by keeping the surface experience unchanged while strengthening the back-end.
5. Governance at Ecosystem Scale
Issuing credentials is easy; ensuring they’re recognized across industries is not. Without trust registries and governance rules, credentials risk becoming siloed.
Intellivon Insight: Intellivon works with consortia and regulators to build layered trust registries, which are internal enterprise registries for workforce credentials, industry registries for supplier certifications, and consortium registries for cross-border recognition. This layered model ensures enterprises don’t end up in “pilot islands” where credentials only work within one company.
Intellivon ensures DID systems scale in practice across industries, regulators, and ecosystems by overcoming these challenges
Conclusion
Centralized identity has become an enterprise liability because one outage or breach can trigger systemic disruption and regulatory exposure. In a world of expanding ecosystems and tightening compliance, this fragility is no longer sustainable.
Decentralized identity management systems offer a stronger alternative, where verifiable credentials are anchored on blockchain, governed by layered trust frameworks, and integrated with existing IAM. The result is a system designed for resilience, compliance, and scale.
Build Your Enterprise Decentralized Identity Platform with Intellivon
At Intellivon, we design decentralized identity systems that go beyond compliance and create enterprise-wide trust fabrics. Our platforms are secure, regulator-ready, and engineered to integrate with the systems you already run. With 11+ years of enterprise expertise and 500+ successful deployments, we know how to take decentralized identity from concept to scalable reality.
Why Partner with Intellivon?
- Seamless Integration: Extend existing IAM investments with verifiable credentials and governance-ready architectures.
- Compliance-First Design: Align with GDPR, HIPAA, SOX, and eIDAS 2.0 from day one.
- Enterprise-Grade Governance: Trust registries, lifecycle rules, and audit frameworks built into the core.
- Scalable Architecture: Proven models that evolve with your business and global ecosystem needs.
Book a discovery call to see how Intellivon can help you transform identity from a vulnerability into a competitive advantage.

FAQs
Q1. How is decentralized identity different from SSO or federated identity?
A1. Decentralized identity doesn’t rely on a central provider. Unlike SSO or federated logins, credentials are verified on the blockchain, making them portable and tamper-proof.
Q2. Will decentralized identity replace Active Directory or IAM?
A2. No. DID extends IAM systems like Active Directory by adding verifiable credentials. It strengthens, not replaces, existing identity governance.
Q3. Is blockchain secure for storing identity data?
A3. Yes. Sensitive data is never stored on-chain. Only identifiers and proofs are anchored on blockchain, keeping credentials private and regulator-compliant.
Q4. How do enterprises revoke or recover decentralized credentials?
A4. Enterprises use revocation registries and lifecycle policies to disable credentials. Recovery depends on wallet design, often supported by custodial or hybrid models.
Q5. Which industries use decentralized identity the most?
A5. Financial services, healthcare, supply chain, and government lead adoption, using DID for KYC, patient access, supplier verification, and digital citizen IDs.