Healthcare delivery is facing pressure to grow without increasing operational burden. Telehealth platforms work well during trials, but they start to struggle when integrated into regulated workflows, enterprise systems, and long-term care. As they scale, the gaps become clear. It gets harder to manage data access, clinical accountability fades, and compliance teams end up with platforms that were not built to handle audits, AI-driven workflows, or deep EHR integration.
That’s why platforms like Collette attract the attention of healthcare leaders. HIPAA-secure telehealth serves as an operating layer that controls how patient data flows, how access is managed, and how responsibility is upheld during virtual interactions. This approach is deliberate and designed into the platform from the start.
At Intellivon, we create HIPAA-secure telehealth platforms within healthcare environments that already have EHRs, identity systems, clinical workflows, and regulatory oversight. We view telehealth as an extension of clinical responsibility and trust, not as a separate path. Based on this experience, we will discuss how to build a HIPAA-secure telehealth app from the ground up in this blog.
Key Takeaways of the HIPAA-Compliant Apps Market
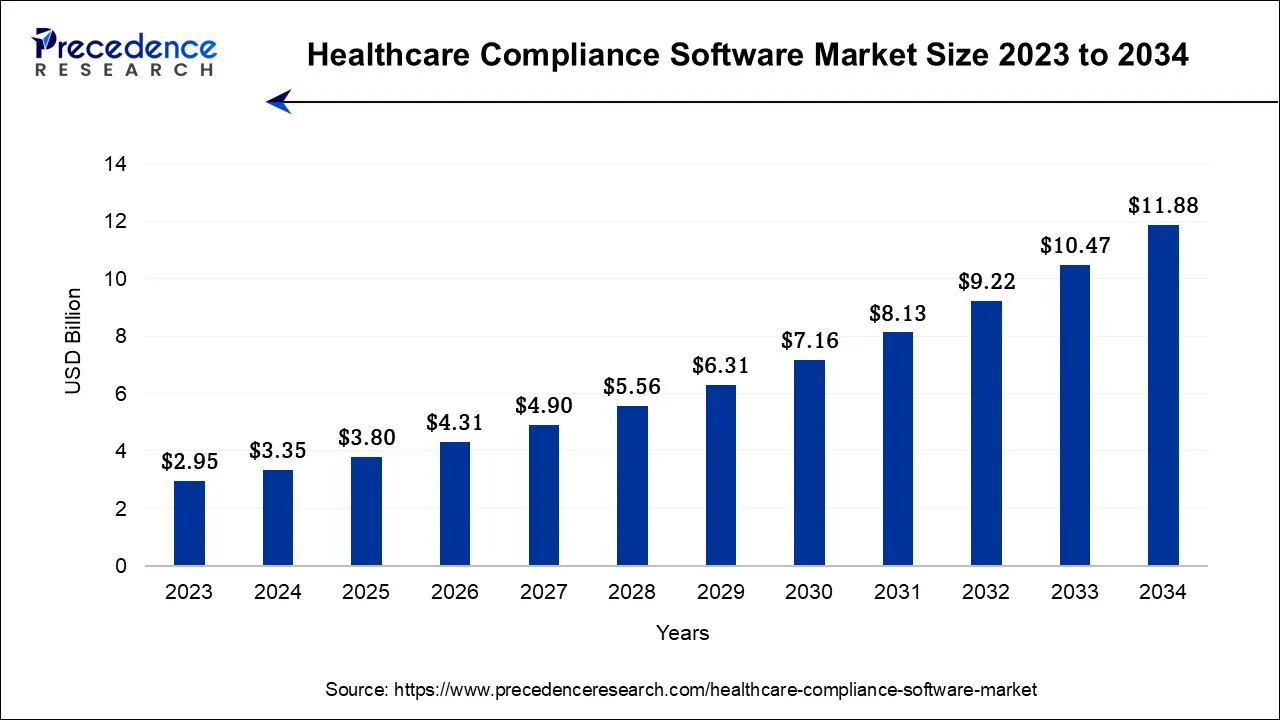
The healthcare compliance software market is entering a period of structural change. Regulatory oversight is tightening, and AI is becoming embedded in how governance is enforced across healthcare systems. In 2024, the market reached USD 3.35 billion and is expected to expand to USD 11.88 billion by 2034, growing at a sustained 13.5 percent CAGR.
This growth signals a shift in enterprise priorities. Healthcare organizations are moving toward platforms that embed privacy controls, automate compliance workflows, and stay aligned with evolving regulatory mandates, including the 2025 updates to the HIPAA Security Rule.
As digital health environments become more interconnected, compliance-first AI platforms are increasingly viewed as a way to reduce regulatory risk, operational strain, and long-term reputational exposure.
Market Drivers:
- Regional Outlook: North America accounted for 52% of total revenue in 2023, supported by well-established regulatory frameworks and compliance maturity.
- By Product Type: Cloud-based compliance solutions held a 56.3% share in 2023, reinforcing the shift toward scalable, SaaS-driven governance platforms. Meanwhile, on-premises deployments are expanding at a 15.8% CAGR as enterprises prioritize greater control over physical data environments.
- By Category: Policy and procedure management platforms represented the largest segment at 25.4% market share. At the same time, medical billing and coding compliance solutions are growing most rapidly, supported by automation requirements and stricter claims accuracy regulations.
- By End-Use: Hospitals led adoption with a 59% share in 2023. However, specialty clinics are showing the highest growth rates as they digitize clinical operations and implement cloud-native compliance systems.
Key Market Drivers
- Increasing enforcement of global healthcare data privacy regulations is raising financial risk for non-compliant organizations.
- Escalating cyber threats and high-profile data breaches continue to fuel sustained investment in compliance infrastructure.
- Rapid growth in EHR and telemedicine adoption is expanding the number of ePHI exposure points across healthcare ecosystems.
- Advancements in AI and machine learning are enabling real-time compliance monitoring and proactive risk detection.
Growth Opportunities
- Broader adoption of cloud-based and AI-enabled compliance platforms is reducing reliance on manual audits and governance processes.
- Rising demand for specialty-focused compliance solutions is driving better alignment with specific clinical and operational workflows.
- Expansion in emerging markets is accelerating as healthcare digitization and regulatory modernization efforts progress.
As regulatory scrutiny continues to intensify, healthcare organizations can no longer manage compliance as a standalone IT function. Over the next decade, enterprises that embed HIPAA compliance directly into AI apps and digital infrastructure will be better positioned to support innovation while preserving trust, security, and operational resilience.
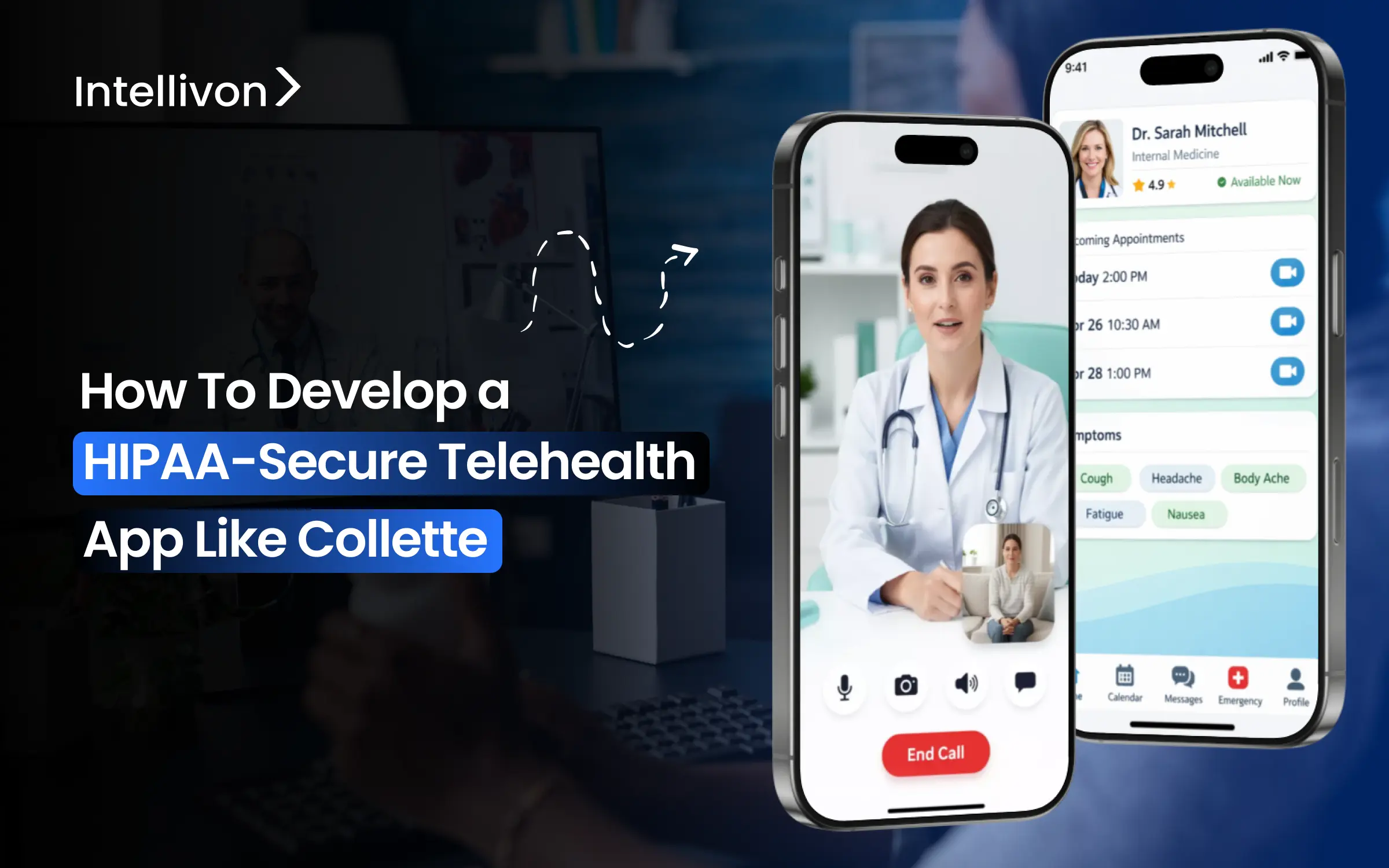
What Is the HIPAA-Secure Telehealth App Collette?
Collette is a HIPAA-secure telehealth platform designed for regulated healthcare delivery, not consumer-first experimentation. Its structure reflects the reality that virtual care must operate under the same governance standards as in-person services.
At its foundation, Collette treats telehealth as an operating layer. Patient data flows are controlled. Access is role-based and auditable. Clinical interactions are captured in ways that support compliance and continuity. As a result, virtual care integrates into enterprise workflows instead of existing in isolation.
Security is embedded by design. Communication, data storage, and system access are governed from the start. Therefore, the platform relies less on compensating controls added after launch.
For enterprises, Collette represents a disciplined model. Usability and compliance are not traded against each other. Instead, the platform shows how telehealth can scale responsibly while maintaining trust, regulatory alignment, and operational control.
Why Collette’s Model Works in Regulated Healthcare Environments
Collette works in regulated healthcare because it treats telehealth as a governed operating layer. Security, access control, auditability, and workflow accountability are embedded into the platform design from day one.
1. Compliance Is Embedded, Not Retrofitted
Collette is designed with HIPAA constraints built into the platform architecture. Data access rules, audit logs, and consent controls are part of everyday system behavior. As a result, compliance does not depend on manual checks or downstream fixes. It becomes repeatable and defensible at scale.
2. Clinical Accountability Remains Intact
Virtual care often fails when responsibility becomes unclear. Collette maintains clear ownership across clinical interactions. Documentation, access, and handoffs remain traceable. Therefore, virtual visits align with the same accountability standards as in-person care.
3. Integration Treated as First Requirement
Regulated environments rely on EHRs, identity systems, and operational tooling already in place. Collette is structured to integrate into these systems without bypassing governance layers. This reduces fragmentation and prevents shadow workflows from emerging.
4. Platform Scales Without Risk
As usage grows, risk usually grows with it. Collette limits this by enforcing role-based access, controlled data flows, and consistent policy enforcement. As a result, scale does not weaken security or compliance posture.
Collette works in regulated healthcare because it prioritizes discipline over speed. Its model shows that telehealth platforms can scale, integrate, and innovate without eroding trust. For enterprises, this approach turns regulatory complexity into a design constraint rather than an operational burden.
How the Collette App Generates Revenue?
In regulated healthcare, a telehealth platform’s business model shapes far more than revenue. It influences compliance behavior, clinical incentives, and long-term platform viability. Collette’s model reflects this reality and is structured to support sustainable care delivery rather than short-term growth tactics.
1. Aligned With Regulated Healthcare Economics
Collette’s business model ties value creation to legitimate care delivery. Revenue is generated through clinical services and operational enablement, not engagement manipulation. As a result, financial incentives reinforce quality, accountability, and compliance.
This alignment reduces pressure to cut corners. Therefore, regulatory discipline remains intact as the platform scales.
2. Built for Enterprise and Provider Adoption
Collette prioritizes enterprise and provider relationships over consumer-scale monetization. Revenue is typically linked to organizational access, licensed usage, or structured care programs. This approach fits existing procurement, budgeting, and governance models.
As a result, adoption integrates cleanly into regulated healthcare operations.
3. Designed for Long-Term Sustainability
Regulated platforms require continuous investment in security, audits, and regulatory updates. Collette’s model supports predictable revenue streams that fund these obligations. Therefore, compliance and platform evolution remain financially viable over time.
Stability becomes a core feature, not a limitation.
4. Avoids Data-Driven Monetization Risk
Collette does not rely on secondary patient data use to drive revenue growth. This reduces regulatory exposure and protects patient trust. For enterprises, this lowers legal, ethical, and reputational risk across the platform lifecycle.
Collette’s business model works because it respects healthcare realities. Revenue, compliance, and clinical integrity remain aligned rather than competing. For enterprises evaluating HIPAA-secure telehealth platforms, this model shows how financial sustainability can coexist with long-term regulatory confidence.
What Is HIPAA Compliance And Why Should You Care?
Healthcare data now travels across systems at a pace that regulations were never originally designed to handle. Cloud infrastructure, AI models, remote monitoring tools, digital access layers, and third-party services interact with patient information at hundreds of touchpoints throughout an enterprise. In this environment, compliance can no longer be treated as a legal step added after a system goes live.
Instead, compliance has become an engineering responsibility. It must influence how platforms are architected, implemented, and governed from the very beginning.
In the United States, HIPAA continues to serve as the primary regulatory framework for healthcare data protection. However, its interpretation and enforcement have evolved to reflect the realities of modern, digitally connected healthcare systems.
The 4 Core Components of HIPAA
HIPAA is not a single regulation. It is a collection of interconnected rules that together define how healthcare data must be protected at scale. Each component has direct implications for how modern data platforms are designed and operated.
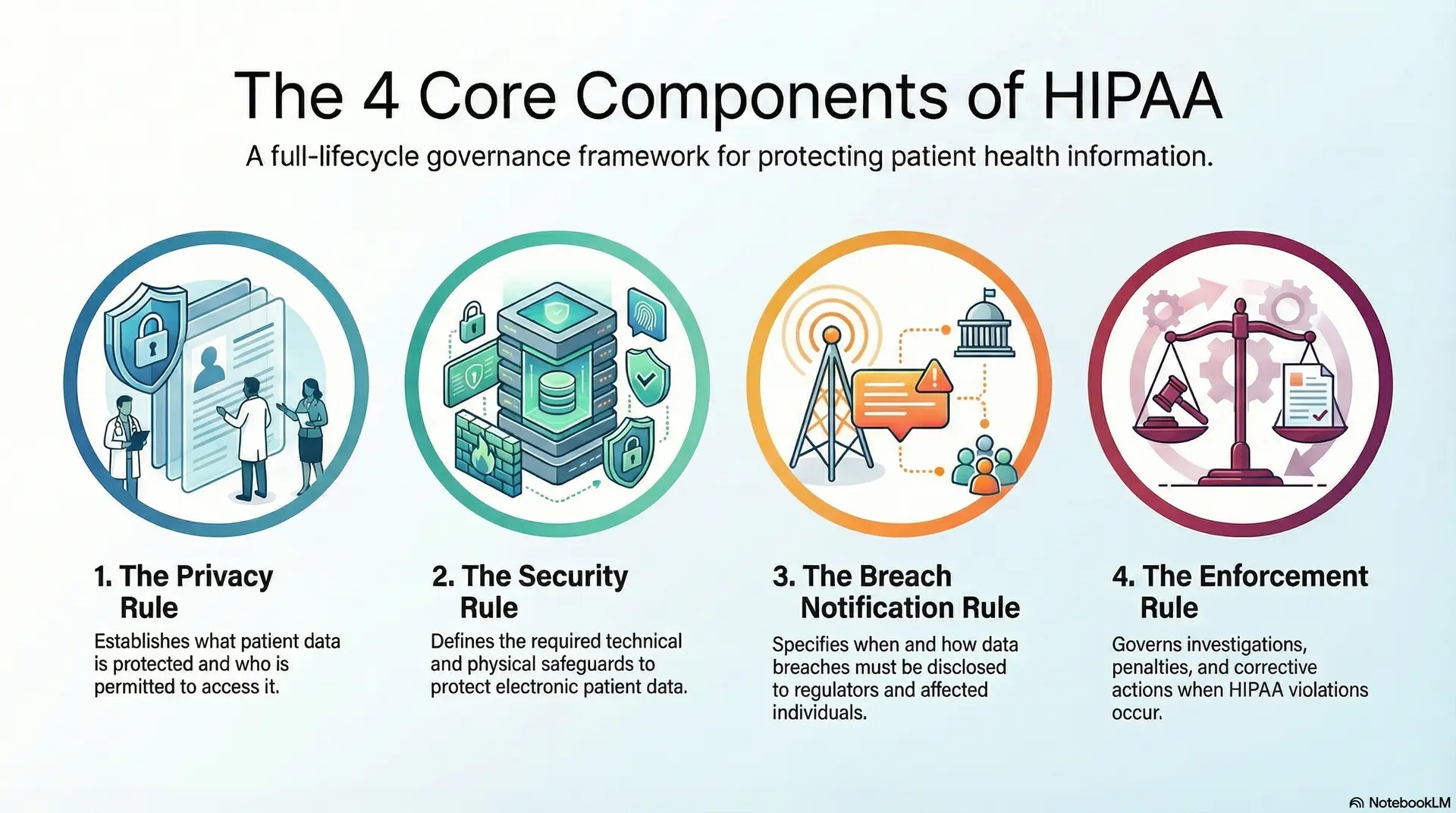
1. Privacy Rule
The Privacy Rule establishes what constitutes protected health information (PHI) and determines who is permitted to access it. It governs how patient data may be used and disclosed across clinical care, billing, research, and administrative functions.
For data platforms, this rule drives data segmentation, consent enforcement, and minimum-necessary access policies. As a result, platforms must manage not only where data is stored, but how it moves between users, services, and systems.
2. Security Rule
The Security Rule addresses how electronic PHI must be protected. It defines requirements across technical, administrative, and physical safeguards.
At the platform level, this rule influences encryption practices, identity and access controls, logging mechanisms, network security, and disaster recovery planning. Security, therefore, becomes embedded into daily system operations rather than treated as a periodic compliance review.
3. Breach Notification Rule
This rule specifies when breaches must be disclosed and how notifications must be delivered to regulators, affected individuals, and, in certain cases, the public.
For modern platforms, this necessitates real-time breach detection, detailed forensic logging, automated notification workflows, and defensible incident timelines. Without these capabilities, meeting regulatory response windows becomes difficult.
4. Enforcement Rule
The Enforcement Rule governs investigations, penalties, and corrective actions when violations occur.
From a platform perspective, this rule reinforces the need for demonstrable compliance through immutable audit trails, documented controls, and continuous oversight. Platforms must be built to withstand examination, not simply to function efficiently. Together, these four components position HIPAA as a full-lifecycle governance framework rather than a checklist.
Types of Safeguards Every Data Platform Should Have
HIPAA defines three safeguard categories that every healthcare data platform must operationalize. These safeguards protect patient data across people, processes, and technology. Their effectiveness depends on being applied collectively.
1. Administrative Safeguards
Administrative safeguards encompass the policies, procedures, and governance structures that determine how data is managed. These include workforce access policies, security training, vendor oversight, and incident response planning.
Within data platforms, these safeguards translate into approval workflows, role governance models, security playbooks, and automated compliance reporting. As a result, regulatory adherence becomes embedded into operations rather than handled manually.
2. Physical Safeguards
Physical safeguards protect the environments in which systems operate. This includes secure facilities, controlled access to infrastructure, and device protection measures.
Even in cloud-based deployments, physical safeguards remain essential through certified hosting environments, geographic controls, and regulated infrastructure providers. Compliance, therefore, extends beyond software into the underlying infrastructure layer.
3. Technical Safeguards
Technical safeguards include the controls most commonly associated with cybersecurity, such as encryption, authentication, access logging, session management, and intrusion detection.
In modern healthcare data platforms, these controls are built into identity services, API gateways, data repositories, analytics layers, and AI pipelines. When implemented in isolation, risk increases. When coordinated as a system, compliance is strengthened.
Safeguards are effective only when they remain tightly integrated. As administrative, physical, and technical controls drift apart, compliance weakens, and exposure grows.
HIPAA Updates and Changes in 2025
Healthcare regulation continues to evolve alongside digital transformation. The 2025 HIPAA updates reflect how cyber threats, AI adoption, and patient expectations have reshaped healthcare data governance.
1. Stronger Cybersecurity Expectations
The updated requirements place greater emphasis on proactive risk management rather than reactive breach reporting. Organizations are now expected to demonstrate continuous security monitoring and resilience planning.
For platforms, this elevates the importance of real-time threat detection, automated response mechanisms, and ongoing vulnerability management.
2. Expanded Patient Data Access Rights
Patients now have enhanced rights to access and transfer their health information in usable electronic formats.
This has direct implications for platform design. Data platforms must support secure patient access layers, controlled data exports, and consent-driven sharing models without introducing new security risks.
3. Tighter Third-Party Accountability
Business associates and vendors are subject to increased scrutiny under expanded enforcement expectations. Liability now extends more clearly across shared platforms and interconnected ecosystems.
As a result, modern healthcare data platforms require built-in vendor governance, contract-aware access controls, and continuous third-party monitoring.
What the 2025 Updates Mean for App Design
The 2025 updates reposition HIPAA from a static compliance requirement to a digital trust framework. Platforms developed before these changes often require substantial architectural modifications to remain defensible.
Organizations that adapt early reduce regulatory exposure while strengthening trust with patients, partners, and regulators alike.
Where HIPAA Risk Actually Lives in Telehealth Platforms
HIPAA risk in telehealth rarely comes from obvious security failures. It emerges through everyday platform decisions that seem harmless at launch but compound over time. Once telehealth systems scale, integrate with enterprise infrastructure, or support AI workflows, these risks become visible under audit and operational stress.
Understanding where HIPAA risk actually lives is critical. It allows organizations to address exposure at the architectural level rather than reacting after incidents occur.
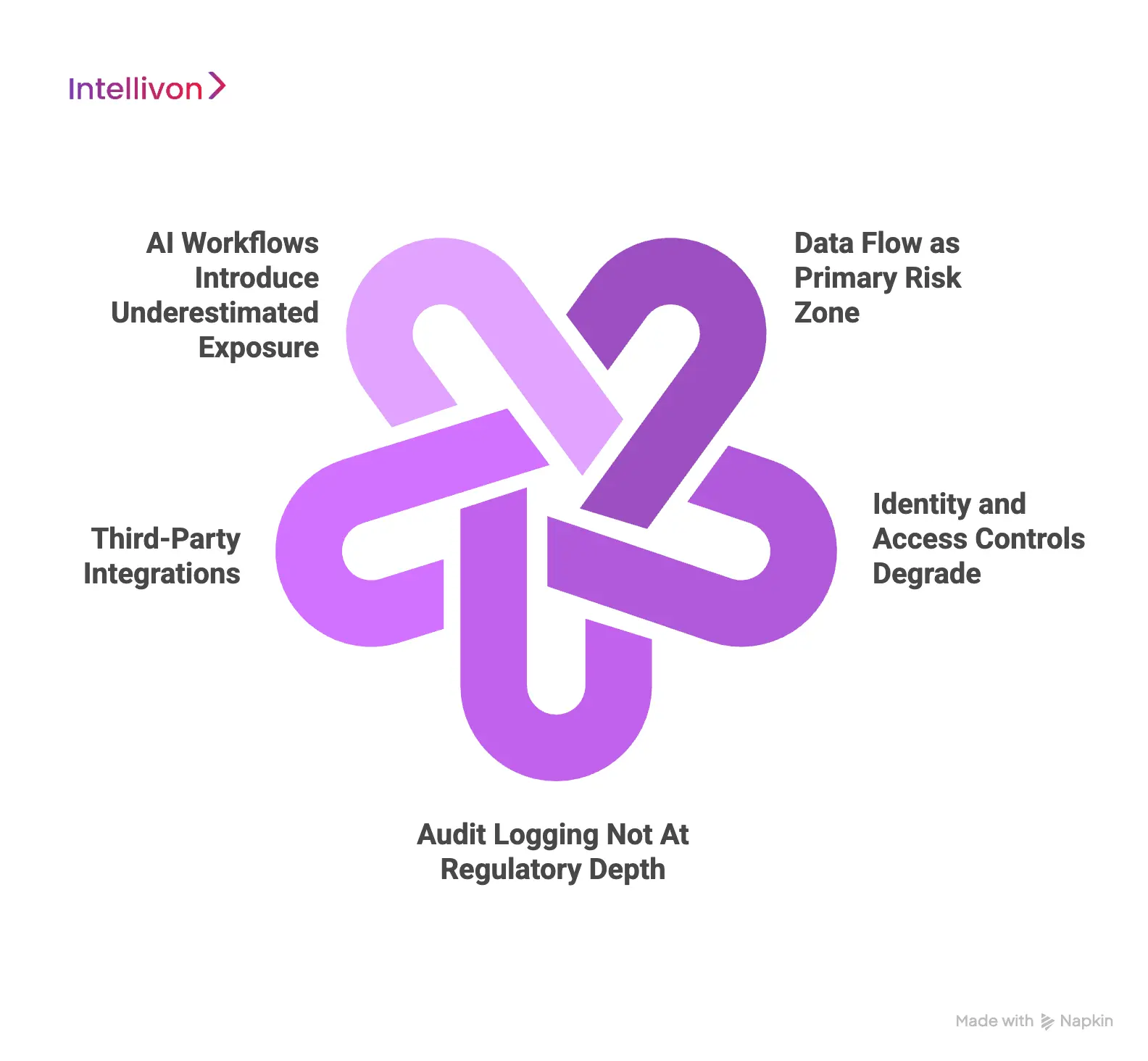
1. Data Flow as Primary Risk Zone
Most telehealth platforms encrypt data at rest. That is expected and insufficient on its own. The greater risk lies in how data moves between services, users, and systems.
Session metadata, clinical notes, chat transcripts, and AI outputs often pass through multiple layers. Without enforced flow controls, PHI spreads beyond its intended scope. As a result, access becomes difficult to trace and defend.
2. Identity and Access Controls Degrade
Early-stage telehealth platforms often rely on broad role definitions. Over time, access expands across clinicians, coordinators, administrators, vendors, and support teams.
Without granular, role-aware controls, permissions drift. Users accumulate access that exceeds the minimum necessity. This pattern frequently appears during HIPAA investigations and internal audits.
3. Audit Logging Not At Regulatory Depth
Many platforms log activity, but logging alone is not enough. Logs often lack immutability, contextual detail, or consistent retention policies.
When incidents occur, teams struggle to reconstruct events with confidence. Therefore, compliance becomes explanatory rather than provable. Regulators expect evidence that can withstand scrutiny.
4. Third-Party Integrations
Telehealth platforms rarely operate alone. EHRs, billing systems, analytics tools, and communication services all interact with PHI.
Each integration extends the compliance boundary. If third-party access is not governed continuously, liability expands across the ecosystem. As a result, risk grows even when the core platform appears secure.
5. AI Workflows Introduce Underestimated Exposure
AI-assisted documentation, triage, and summarization now process sensitive clinical data in real time. These workflows frequently bypass traditional access and logging controls.
Without clear PHI boundaries, human oversight, and inference traceability, AI becomes a silent compliance risk. This area is drawing increasing regulatory attention.
HIPAA risk in telehealth does not live in a single feature or system. It accumulates across data movement, access governance, integrations, and automation layers. Platforms that address these risks by design remain defensible over time.
Regulatory Reality Shaping HIPAA-Secure Telehealth Platforms
Enforcement data confirms that HIPAA scrutiny is continuous, not episodic. Since the HIPAA Privacy Rule compliance date in April 2003, OCR has recorded 366,377 HIPAA complaints, conducted 1,191 compliance reviews, and resolved approximately 99% of cases as of July 31, 2024.
For enterprise leaders, this confirms that HIPAA-secure telehealth platforms must be built with the assumption of audits, investigations, and corrective action plans across their lifecycle.
Evidence Gaps Behind “HIPAA-Secure Telehealth” Claims
Despite widespread claims of HIPAA compliance, real-world evidence on telehealth security practices is limited. A large U.S. systematic review screened 25,404 academic papers published between 2003 and 2016. Only 21 studies met the inclusion criteria for evaluating actual telehealth privacy and security implementation.
Within that same review, 67% of the included studies were policy-focused, while only 14% relied on surveys or interviews with telehealth practitioners. Notably, no randomized controlled trials were identified that evaluated the effectiveness of telehealth security controls.
The reviewers reported 99.04% agreement, with Cohen’s kappa = 0.7331, indicating strong methodological consistency. The gap, therefore, is not analytical rigor, but the absence of implementation-level evidence. For enterprises, this means most “HIPAA-secure” claims in the market are based on interpretation rather than validated operational models.
Platform Transparency Gaps in Telehealth Tools
A peer-reviewed assessment of telemedicine videoconferencing tools highlights a deeper transparency issue. Among 26 telemedicine platforms evaluated, only 13 (50%) were designed specifically for healthcare use.
Only 6 of the 26 platforms (23%) were described as compliant with both U.S. and European regulatory standards. Complete technical and security documentation was publicly accessible for just five platforms (19.2%).
Even basic procurement information was inconsistently available. Pricing details were disclosed by 42% of platforms, while security documentation was available for 43%. For enterprise buyers, low transparency often correlates with downstream compliance, integration, and liability risk.
What HIPAA-Secure Telehealth Controls Look Like in Practice
Operational compliance requires far more than policy statements. A validated telehealth privacy and security self-assessment framework initially included 84 control statements, reviewed by five telehealth providers, and refined into a 49-control operational instrument.
The validation study included 31 telehealth providers, with the framework demonstrating strong internal consistency (Cronbach’s alpha = 0.906). This indicates that HIPAA compliance in telehealth requires dozens of concurrent controls operating together across workflows, infrastructure, and user behavior.
The study also identified physical safeguards as a recurring weakness. In referenced prior reviews, only eight studies addressed secure server location, backup strategies, or controlled hosting environments. This underscores why cloud hosting alone does not satisfy HIPAA requirements without explicit physical safeguard accountability.
Why This Matters When Building a Platform Like Collette
These findings explain why platforms like Collette are used as enterprise reference models. Their differentiation lies in architectural discipline, audit readiness, and transparency aligned with post-discretion HIPAA enforcement. For organizations developing HIPAA-secure telehealth platforms today, the implication is clear: compliance must be engineered into the platform from inception, not retrofitted after scale.
Core Features of a HIPAA-Secure Telehealth App Like Collette
In regulated healthcare, features exist to enforce discipline. They are not optional enhancements or interface upgrades. Each core feature in a HIPAA-secure telehealth platform must control risk, preserve accountability, and support enterprise operations under audit pressure. Platforms like Collette reflect this reality in how their capabilities are structured and deployed.
1. Audit-Ready Virtual Consultations
Virtual visits are encrypted end-to-end. However, security does not stop at transmission. Each session is bound to authenticated users, defined roles, and controlled access windows.
Every interaction is logged with clinical and operational context. As a result, organizations can demonstrate who accessed data, when it happened, and why it was permitted. This makes virtual care defensible during audits.
2. Identity and Access Management
HIPAA-secure telehealth platforms cannot rely on static roles. Access must adapt to clinical responsibility, organizational hierarchy, and care context.
Collette-style platforms enforce least-privilege access across clinicians, care teams, administrators, and vendors. Permissions are reviewed and adjusted continuously. Therefore, access does not expand silently as teams, partners, or services scale.
3. End-to-End PHI Data Lifecycle Governance
PHI risk increases over time, not at creation. Data must be governed across intake, storage, sharing, and deletion.
Enterprise platforms control how data flows between systems, not just where it resides. Policies determine retention, segmentation, and access boundaries. As a result, historical data does not become a long-term liability.
4. Strong Audit Logging
Basic logs are insufficient in regulated environments. Audit trails must be complete, immutable, and context-rich.
Every access event, workflow action, and system interaction is captured with timestamps and user attribution. When incidents occur, teams can reconstruct timelines with confidence. This shifts compliance from reactive defense to provable governance.
5. Deep EHR System Integration
Telehealth cannot operate as a parallel system. It must integrate into existing EHRs, identity providers, scheduling systems, and operational platforms.
Collette-style platforms respect enterprise governance layers during integration. Data flows remain controlled, and workflows remain consistent. Therefore, telehealth extends care delivery instead of fragmenting it.
6. Programmatic Consent
Consent is not a document. It is an active control layer. HIPAA-secure platforms enforce consent rules across access, sharing, and downstream use. Policies adapt based on jurisdiction, care type, and patient preferences.
This removes manual enforcement and reduces human error.
7. AI-Ready Workflows With HIPAA Guardrails
AI now supports documentation, triage, and patient engagement. However, unmanaged AI creates a silent compliance risk.
Enterprise platforms restrict how AI interacts with PHI. Human oversight, inference logging, and access boundaries are enforced by design. Therefore, innovation remains controlled and auditable.
8. Continuous Security and Compliance Monitoring
HIPAA-secure telehealth systems monitor access patterns, policy violations, and system behavior in real time. Alerts surface issues early. As a result, teams address risk before it escalates into incidents or enforcement actions.
A HIPAA-secure telehealth app like Collette succeeds because its features enforce governance, not convenience. Each capability supports compliance, accountability, and operational scale.
Advanced AI-Powered Features Of A HIPAA Telehealth App
AI can materially improve telehealth performance when applied with restraint. It reduces administrative burden, improves care coordination, and supports clinicians under load. However, AI also introduces new compliance and accountability risks. In HIPAA-secure telehealth platforms, advanced AI features must operate as governed systems, not autonomous agents.
The following capabilities represent how AI should be deployed in enterprise telehealth environments.
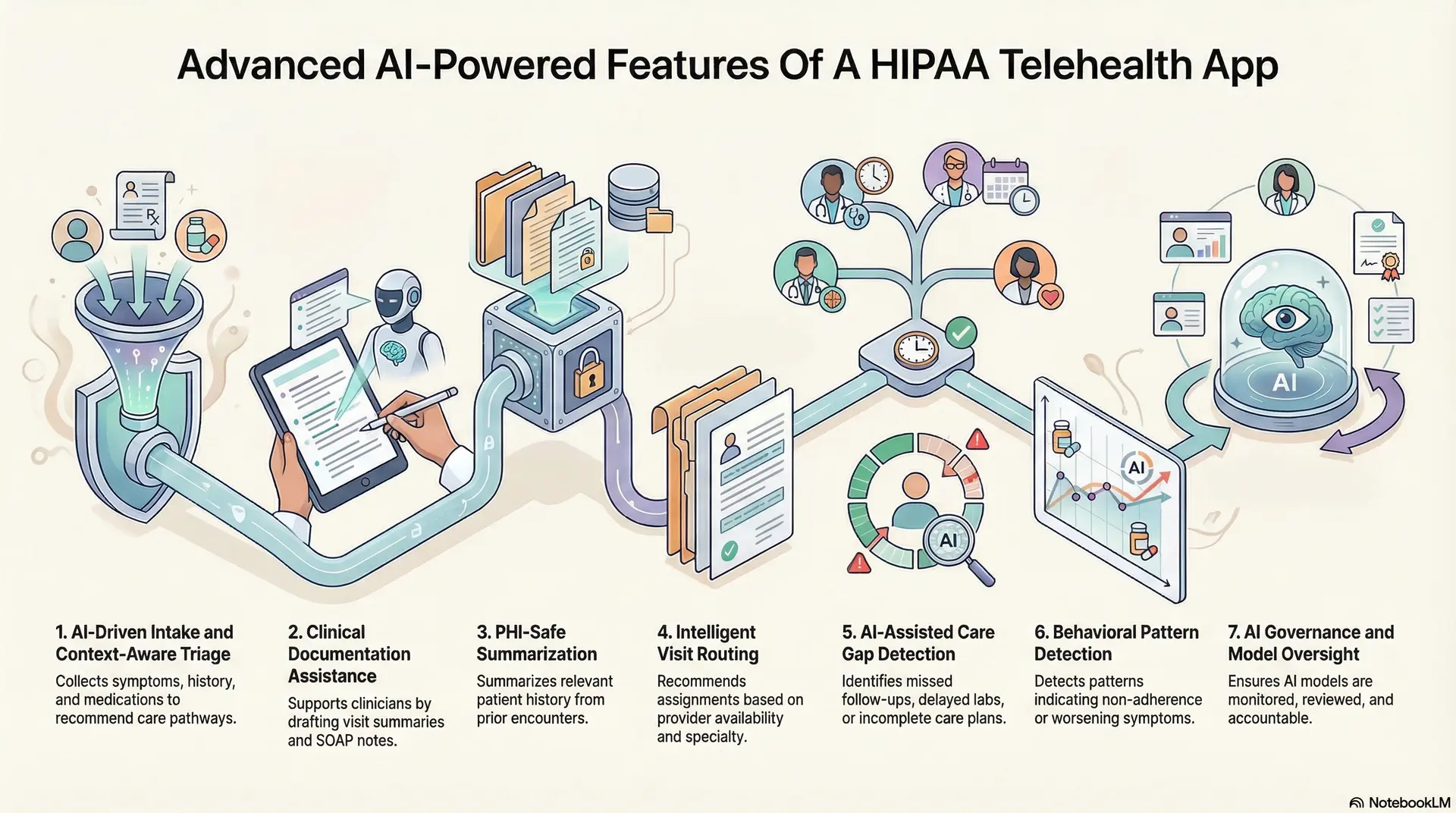
1. AI-Driven Intake and Context-Aware Triage
AI can structure patient intake before a visit begins. It collects symptoms, history, medications, and risk indicators through guided workflows. This reduces variability and improves data quality at the first point of contact.
Triage models then analyze this information to recommend urgency, care pathways, or escalation needs. However, these recommendations remain advisory. Clinical judgment always determines final routing. This preserves accountability while improving speed and consistency.
2. Clinical Documentation Assistance
AI can support clinicians by drafting visit summaries, SOAP notes, and follow-up instructions. It can also pre-populate structured fields inside the clinical record. This reduces documentation time without replacing the clinician’s responsibility.
Every generated output must remain traceable. Inputs, prompts, edits, and final approvals are logged. Therefore, documentation remains auditable and defensible during compliance reviews.
3. PHI-Safe Summarization
Before a visit, AI can summarize relevant patient history across prior encounters. It highlights recent diagnoses, medications, labs, and unresolved issues. This allows clinicians to focus on care instead of navigation.
These summaries operate within strict PHI boundaries. Only authorized data is processed. Outputs are session-scoped and logged. As a result, efficiency improves without expanding exposure.
4. Intelligent Visit Routing
AI can analyze provider availability, specialty alignment, and workload in real time. It recommends visit assignments that balance care quality and operational efficiency.
Routing logic respects licensure, scope of practice, and organizational rules. Therefore, optimization never overrides regulatory or clinical constraints. This helps enterprises scale access without creating staffing risk.
5. AI-Assisted Care Gap Detection
AI can identify missed follow-ups, delayed labs, or incomplete care plans. It flags gaps across populations and individual patients.
These insights support proactive outreach and continuity of care. However, actions remain clinician-directed. AI highlights risk. Humans decide intervention.
6. Behavioral Pattern Detection
AI can detect patterns that indicate non-adherence, worsening symptoms, or disengagement. It analyzes interaction frequency, message sentiment, and care progression.
These signals help teams intervene earlier. Governance ensures outputs are explainable and reviewed. Therefore, AI augments awareness without acting autonomously.
7. AI Governance and Model Oversight
Advanced platforms include AI governance layers by design. Models are versioned, monitored, and reviewed. Drift detection, performance tracking, and access controls remain active throughout deployment.
Human-in-the-loop workflows ensure oversight. As a result, AI remains accountable to enterprise policy, not just technical performance.
Advanced AI features strengthen telehealth platforms when they operate within clear boundaries. They improve efficiency, reduce friction, and support clinicians under pressure.
How HIPAA-Secure Telehealth Fits Into Enterprise Healthcare Systems
Telehealth only delivers value when it fits cleanly into existing healthcare systems. In enterprise environments, poor interoperability creates risk, not efficiency. HIPAA-secure telehealth platforms must integrate into clinical, operational, and governance layers without fragmenting control.
Interoperability is therefore a compliance requirement. It determines whether virtual care strengthens the system or weakens it.
1. Preserves Clinical Continuity
Enterprise healthcare workflows live inside the EHR. Telehealth platforms must integrate without creating duplicate records or manual reconciliation.
Appointments, notes, orders, and outcomes should sync automatically. As a result, clinicians maintain continuity, and data remains audit-ready across care settings.
2. Federated Identity and Access Governance
Most enterprises already manage identity through centralized IAM systems. Telehealth platforms must align with these controls instead of introducing separate access logic.
Federated identity ensures consistent permissions across systems. Therefore, access remains traceable, role-based, and compliant with HIPAA minimum-necessary requirements.
3. Secure Data Exchange Across Connected Systems
Telehealth platforms exchange data with labs, imaging, billing, and analytics tools. Each connection expands the compliance surface.
Enterprise-grade interoperability enforces encryption, consent, and access rules at every exchange point. As a result, data moves securely without uncontrolled exposure.
4. Revenue and Coding System Alignment
Virtual care affects billing workflows immediately. Misalignment leads to claim delays and compliance gaps.
HIPAA-secure platforms integrate visit data directly into billing and coding systems. Therefore, revenue integrity improves without compromising regulatory discipline.
5. Integration With Compliance Infrastructure
Compliance extends beyond clinical systems. It includes monitoring, reporting, and audit tooling.
Telehealth platforms must feed activity data into enterprise logging and compliance systems. This enables continuous oversight instead of reactive investigation.
Scaling Telehealth Without Fragmentation
As telehealth expands, inconsistent integrations introduce operational risk. Each new connection must follow the same governance model.
Standardized interoperability frameworks prevent fragmentation. As a result, platforms scale predictably while maintaining control.
HIPAA-secure telehealth fits into enterprise healthcare systems only when interoperability is intentional. Clean integration preserves workflows, enforces access control, and supports audit readiness.
How We Develop A HIPAA-Secure Telehealth App Like Collette
Building a HIPAA-secure telehealth platform is not a linear software project. It is a governance-led system built to hold up under audit, scale, and organizational change. At Intellivon, telehealth is treated as a regulated operating layer that sits inside enterprise healthcare infrastructure.
The steps below reflect how durable, compliant platforms are built in real healthcare environments.
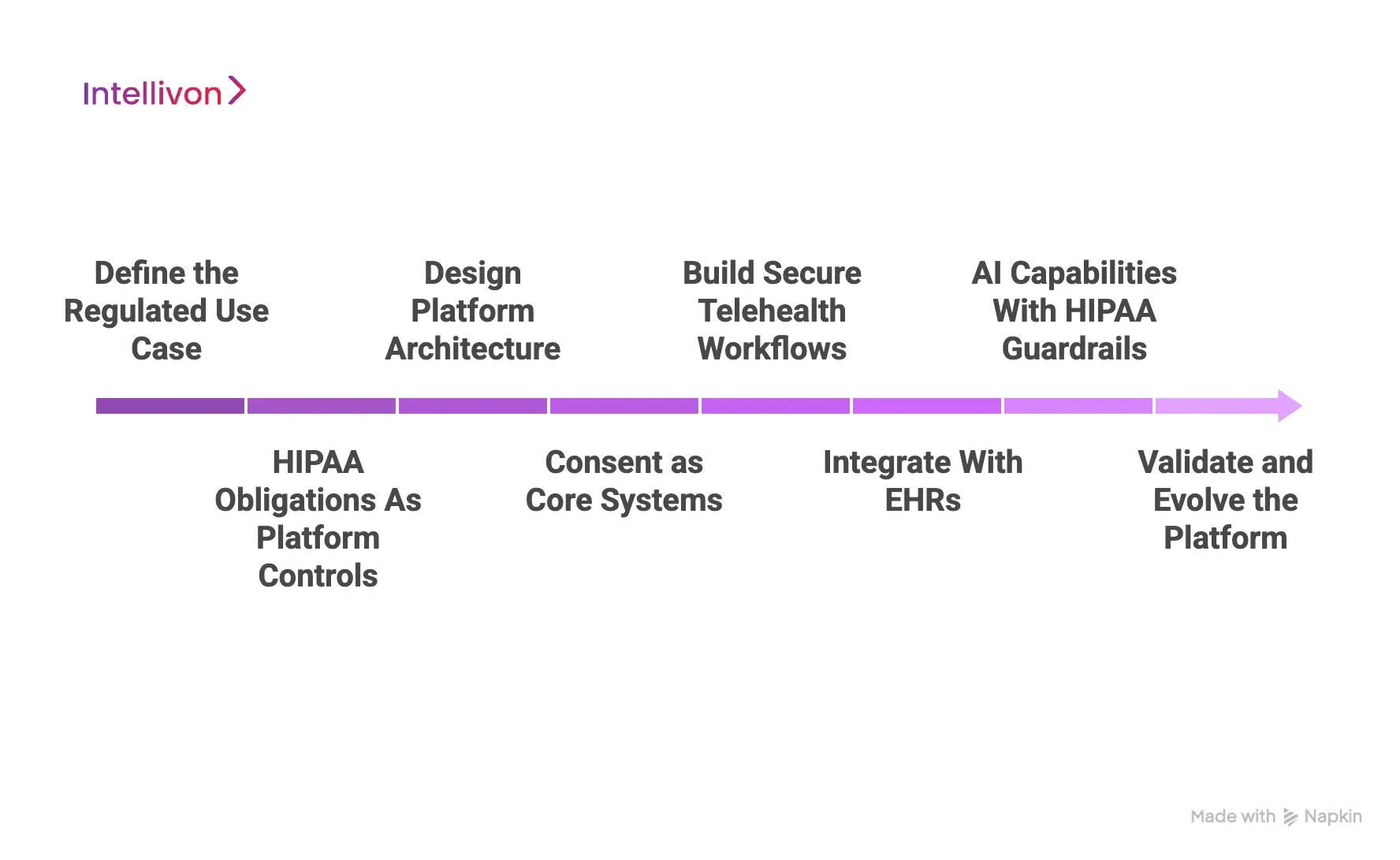
Step 1: Define the Regulated Use Case
Every project begins by clearly defining the clinical use case. This includes care type, patient population, delivery model, and jurisdictional scope. Without this clarity, compliance decisions become generic and fragile.
Once the use case is defined, PHI entry points, access paths, and data exits are mapped. This establishes a formal risk boundary. As a result, teams know exactly where HIPAA controls must apply and where exposure is unacceptable.
Step 2: HIPAA Obligations As Platform Controls
HIPAA requirements are not treated as documentation tasks. They are translated into enforceable system behaviors that shape how the platform operates every day.
Administrative, physical, and technical safeguards are mapped directly to workflows, infrastructure, and access logic. Each safeguard is tied to a measurable control. Therefore, compliance can be validated continuously instead of reviewed once at launch.
Step 3: Design Platform Architecture
Architecture decisions determine long-term compliance outcomes. The platform is structured to separate identity, data storage, workflows, and integrations into clearly governed layers.
Trust zones define how PHI is accessed and processed across services. This separation limits blast radius when systems change or scale. It also prevents compliance erosion as new features are introduced.
Step 4: Consent as Core Systems
Access control is designed around clinical responsibility, not convenience. Enterprise identity systems are integrated to enforce role-based and least-privilege access across all users.
Consent is implemented as a dynamic policy engine. It governs who can access data, when access is allowed, and for what purpose. Therefore, compliance decisions remain consistent across workflows and time.
Step 5: Build Secure Telehealth Workflows
Virtual consultations are implemented with encrypted communication, session isolation, and controlled access windows. Security applies before, during, and after the visit.
Every interaction generates audit-grade logs with context. Logs capture who accessed data, what actions were taken, and why access was permitted. As a result, platforms can withstand regulatory scrutiny without reconstruction guesswork.
Step 6: Integrate With EHRs
Telehealth platforms must integrate into existing enterprise systems rather than operate alongside them. This includes EHRs, scheduling, billing, care coordination, and analytics platforms.
Data flows bi-directionally under consistent security and governance rules. This prevents duplicate records and shadow processes. It also preserves continuity across virtual and in-person care delivery.
Step 7: AI Capabilities With HIPAA Guardrails
AI features are introduced only after governance foundations are in place. Models operate within defined PHI boundaries and approved use cases.
Inputs, outputs, and human approvals are logged. AI supports clinicians, but never replaces accountability. Therefore, innovation scales without creating hidden compliance risk.
Step 8: Validate and Evolve the Platform
Before launch, controls are tested against real workflows and edge cases. After deployment, continuous monitoring tracks access patterns, policy drift, and system behavior.
This ensures compliance does not degrade as usage grows. Platforms evolve deliberately while remaining defensible under audit.
HIPAA-secure telehealth platforms succeed when governance drives execution. Each step reinforces compliance, accountability, and enterprise fit. This approach allows organizations to scale virtual care with confidence rather than accumulate risk over time.
Cost to Build a HIPAA-Secure Telehealth App
Building a HIPAA-secure telehealth platform does not require a large, upfront enterprise rollout. Most healthcare organizations begin with a focused foundation that supports secure virtual care delivery, EHR integration, and regulatory controls. The platform then expands as care volumes, service lines, and compliance needs grow.
At Intellivon, costs are structured around platform maturity, not feature accumulation. This approach helps enterprises launch faster, validate outcomes early, and scale without carrying avoidable financial or operational risk.
Estimated Cost Breakdown (USD 55,000–150,000)
| Cost Component | What It Covers | Estimated Range |
| Discovery & Compliance Scoping | Care use cases, HIPAA risk mapping, and architecture planning | $7,000 – $14,000 |
| Secure Telehealth Delivery Layer | Video visits, async consults, clinician workspace | $12,000 – $24,000 |
| Identity & Access Management | RBAC, IAM integration, and least-privilege controls | $8,000 – $15,000 |
| EHR & Clinical Data Integration | FHIR/HL7 integration, safe write-back, validation | $12,000 – $25,000 |
| Consent & Data Governance | Consent models, data segmentation, retention rules | $6,000 – $12,000 |
| Compliance & Security Controls | HIPAA safeguards, audit trails, and logging | $6,000 – $12,000 |
| Reporting & Audit Visibility | Access logs, compliance dashboards, oversight views | $4,000 – $8,000 |
| Testing, Pilot & Stabilization | QA, controlled rollout, post-launch tuning | $4,000 – $8,000 |
Typical MVP Range: $55,000 – $90,000
Enterprise-Ready Phase 1 Platform: $105,000 – $150,000
The final cost depends on how much governance, integration depth, and audit readiness are required at launch. A phased approach allows enterprises to prove value quickly while keeping capital exposure measured.
Factors Affecting the Cost of HIPAA-Secure Telehealth Platforms
Cost is not driven by screens alone. It is shaped by compliance depth, integration complexity, and long-term governance needs. Understanding these drivers early prevents budget surprises later.
1. Scope of Virtual Care Workflows
Platforms limited to basic video visits cost less than those supporting async care, documentation, and follow-up. Each added workflow increases testing and compliance validation effort.
2. Depth of EHR and Data Integration
Light integrations differ from bidirectional clinical workflows. Safe write-back, real-time updates, and longitudinal record integrity raise cost but protect trust and continuity.
3. Compliance and Audit Requirements
Baseline HIPAA controls are standard. Costs increase when platforms require advanced consent logic, detailed auditability, and multi-role access governance.
4. Identity, Access, and Vendor Exposure
Single-role systems cost less than platforms supporting clinicians, staff, and third parties. Each additional role expands access logic and monitoring requirements.
5. Reporting and Oversight Expectations
Basic logs are simpler than audit-ready reporting. Executive visibility into access, risk, and compliance requires stronger data pipelines.
How to Stay Within Budget Without Compromising Control
Enterprises control costs by phasing delivery deliberately. Start with secure virtual care, identity controls, EHR integration, and core HIPAA safeguards. Expand analytics, automation, and advanced workflows once outcomes are validated.
Clear KPIs, disciplined change control, and early architectural decisions prevent scope creep. The goal is not to build everything at once, but to establish a defensible foundation and scale with confidence.
Overcoming Challenges While Building Secure Telehealth Apps
Building a secure telehealth platform is rarely blocked by technology alone. Most challenges emerge at the intersection of compliance, scale, and enterprise operating reality. As platforms move from pilots into core care delivery, gaps in governance, integration, and control become visible.
Addressing these challenges early determines whether telehealth becomes a durable enterprise asset or a growing regulatory liability.
1. Compliance Drift as Platforms Scale
Many telehealth platforms begin with strong compliance intent. However, as new workflows, user roles, and integrations are added, controls weaken quietly over time. Policies may remain documented, but enforcement becomes inconsistent across systems and teams.
Intellivon mitigates this risk by embedding compliance directly into platform behavior. Controls are enforced programmatically across identity, data access, and workflow layers. As platforms scale, governance scales with them, rather than relying on manual oversight or post-hoc audits.
2. Fragmented Integration With Enterprise Systems
Telehealth platforms often operate alongside EHRs, billing systems, and analytics tools instead of integrating cleanly. This creates duplicate records, manual reconciliation, and audit blind spots that weaken both compliance and clinical continuity.
Intellivon treats interoperability as a core architectural requirement, not an add-on. Telehealth workflows integrate directly into existing enterprise systems under consistent security and data governance rules. This preserves longitudinal patient records while reducing operational complexity and compliance risk.
3. Access Control Complexity Across Roles and Vendors
As telehealth expands, access is granted to clinicians, care coordinators, administrators, and third-party partners. Without disciplined identity governance, permissions drift beyond minimum necessary access, often without visibility.
Intellivon implements fine-grained, role-aware access models aligned with enterprise IAM systems. Permissions remain traceable, reviewable, and context-driven. This prevents silent access expansion and supports audit defensibility across internal teams and external vendors.
4. AI-Led Hidden Compliance Risk
AI capabilities are increasingly introduced to improve efficiency in documentation, triage, and patient engagement. However, ungoverned AI workflows can bypass traditional controls, expanding PHI exposure without clear accountability.
Intellivon introduces AI only within defined HIPAA guardrails. Inputs, outputs, and approvals are logged, and human oversight remains mandatory. This allows enterprises to innovate responsibly while maintaining trust, transparency, and regulatory alignment.
5. Proving Compliance During Audits and Incidents
Many platforms appear compliant until evidence is requested. At that point, incomplete logs, inconsistent records, and missing context undermine regulatory response and increase exposure.
Intellivon builds audit readiness into daily platform operations. Systems generate immutable logs, defensible timelines, and real-time compliance visibility. When scrutiny arrives, organizations respond with evidence rather than reconstruction, reducing disruption and risk.
Secure telehealth platforms fail when challenges are addressed reactively. They succeed when risks are anticipated and engineered out early. By treating compliance, integration, access governance, and AI oversight as design constraints, enterprises build telehealth platforms that scale with confidence instead of accumulating risk over time.
Conclusion
HIPAA-secure telehealth is no longer a differentiator. It is the minimum requirement for operating virtual care at enterprise scale. What separates durable platforms from short-lived tools is how deeply compliance, governance, and interoperability are engineered into the foundation.
Platforms like Collette demonstrate that secure telehealth works when it is treated as an operating layer, not a feature set. Data control, audit readiness, AI governance, and enterprise integration must function together. When any one of these is treated as an afterthought, risk accumulates quietly and surfaces later under scale or scrutiny.
At Intellivon, telehealth platforms are built with this reality in mind. The focus stays on long-term defensibility, measurable outcomes, and controlled growth. The goal is not to launch quickly, but to scale responsibly.
Build a HIPAA-Secure Telehealth Platform That Scales With Trust
At Intellivon, we build HIPAA-secure telehealth platforms as enterprise operating layers, not virtual visit tools layered onto legacy systems. Our platforms are designed to govern how care is accessed, how patient data moves, and how accountability is enforced across virtual interactions, clinical teams, and enterprise infrastructure.
Each solution is engineered for healthcare organizations operating under regulatory scrutiny and scale pressure. Platforms are compliance-led, infrastructure-first, and built to support secure virtual care delivery, enterprise integration, and AI-enabled workflows while preserving audit readiness, clinical oversight, and predictable operating economics as adoption expands across service lines and regions.
Why Partner With Intellivon?
- Governance-first telehealth architecture aligned with HIPAA requirements, audit expectations, and enterprise risk controls
- Deep interoperability expertise across EHRs, identity platforms, scheduling systems, billing workflows, and clinical data ecosystems
- Compliance-by-design platforms supporting role-based access, consent enforcement, immutable audit trails, and regulatory reporting
- AI-enabled workflows with guardrails that improve efficiency while maintaining human oversight and PHI boundaries
- Enterprise delivery model with phased rollout, KPI-led validation, and long-term scalability built into the foundation
Talk to Intellivon’s healthcare platform architects to explore how a HIPAA-secure telehealth platform like Collette can be designed to integrate into your existing systems, protect patient trust, and scale responsibly without adding compliance or operational risk.
FAQs
Q1. What makes a telehealth platform HIPAA-secure at the enterprise level?
A1. A telehealth platform becomes HIPAA-secure when compliance is enforced through system design, not policy documents. This includes role-based access control, encrypted data flows, audit-grade logging, consent enforcement, and secure integrations with EHRs and enterprise systems.
At the enterprise level, security must hold under scale, audits, and multi-system workflows. Platforms like Collette demonstrate this by embedding governance into daily operations rather than adding controls after launch.
Q2. How long does it take to build a HIPAA-secure telehealth platform?
A2. Timelines depend on platform scope and integration depth. A focused MVP that supports secure virtual visits, EHR integration, and core HIPAA controls typically takes 3–4 months.
Enterprise-ready Phase 1 platforms, including advanced governance, audit visibility, and AI guardrails, usually take 5–7 months. Phased delivery reduces risk while allowing early validation.
Q3. Can AI be used safely in HIPAA-secure telehealth platforms?
A3. Yes, but only with strict guardrails. AI must operate within defined PHI boundaries, include human-in-the-loop oversight, and generate traceable outputs.
HIPAA-secure platforms log AI inputs, outputs, and approvals. This ensures AI supports clinicians without creating unmanaged compliance exposure or accountability gaps.
Q4. What are the biggest compliance risks in telehealth platforms?
A4. The highest risks come from data flow, access drift, and integrations. PHI often spreads across systems through APIs, vendors, and automation workflows.
Without enforced access controls, audit-ready logs, and governed integrations, platforms accumulate silent risk. These issues typically surface during audits or security incidents, not at launch.
Q5. Should enterprises build or buy a HIPAA-secure telehealth platform?
A5. Off-the-shelf tools work for limited use cases. However, enterprises often outgrow them due to integration, governance, and customization limits.
Building or partnering to develop a platform offers greater control over compliance, workflows, and long-term scalability. The right choice depends on risk tolerance, growth plans, and regulatory exposure.