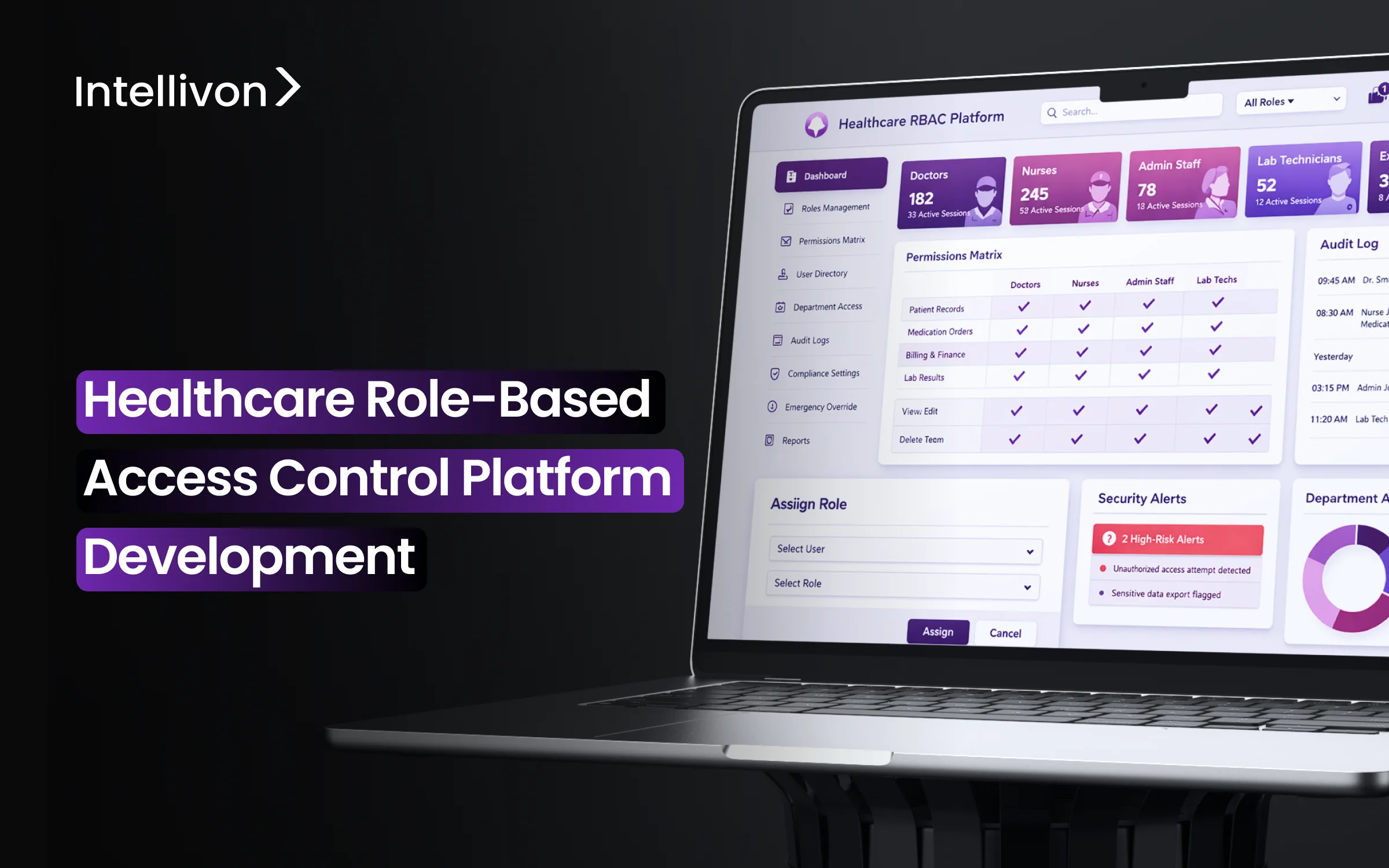
Role-based access control (RBAC) typically starts with a straightforward model and a clear purpose. However, over time, circumstances change when eams expand, roles overlap, and what once seemed organized begins to stray from how work actually gets done within the organization. The cost of an RBAC drift, when role definitions become misaligned with real job responsibilities, appears faster than many teams anticipate. As more apps connect to the environment, those small gaps tend to widen across systems, workflows, and partner interactions.
A specially designed RBAC platform alters this trend by consolidating role logic, identity signals, and application permissions into one controlled area, so access remains consistent as users join, move, and leave.
At Intellivon, we understand how complex healthcare environments operate, with multiple systems, strict regulations, and constant pressure to scale, and develop RBAC platforms keeping this in mind. In this blog, we will explain how we build an enterprise RBAC platform foundation that scales with the growth in your healthcare ecosystem.
Key Takeaways Of The RBAC Platform Market
The Role-Based Access Control (RBAC) market is growing fast as organizations face stronger cybersecurity pressure and stricter compliance requirements, especially in healthcare and finance. The global role-based access control market was valued at $8.3 billion in 2022 and is expected to reach $24.3 billion by 2032, growing at a CAGR of 11.8 percent between 2023 and 2032.
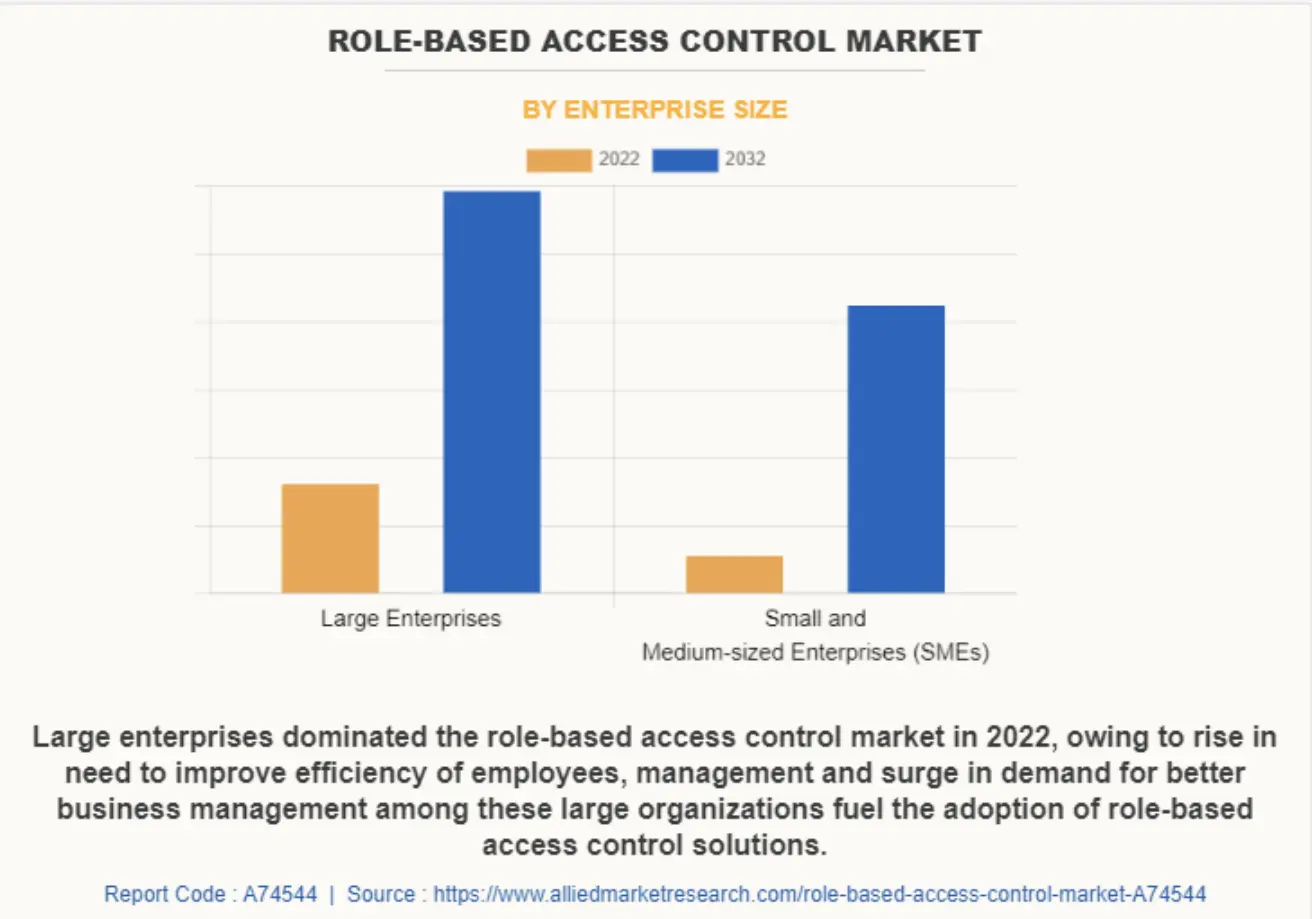
Market Insights:
- Rising cyber threats and regulations such as HIPAA are pushing organizations to use RBAC to restrict access based on user roles.
- Cloud-based RBAC solutions are leading adoption, while SMEs are choosing simpler, easier-to-manage versions.
- AI is strengthening RBAC by enabling more adaptive and context-aware access controls.
- Growing investments in AI, ML, and IoT are speeding up market expansion.
- Demand has increased further after COVID, as enterprises needed secure remote access at scale.
ROI Metrics of Role-Based Access Control (RBAC)
RBAC delivers clear operational and financial gains for enterprises. It can reduce manual user provisioning effort by up to 70% and cut help desk tickets by 25–40%, which frees valuable IT capacity.
Organizations also report much faster onboarding, often shrinking timelines from days to hours. In addition, stronger access discipline lowers breach exposure, with insider incidents averaging $15.4M annually.
Audit preparation becomes simpler and more predictable. NIST analysis shows benefit-to-cost ratios reaching up to 158:1. Over time, teams usually recover their initial investment through avoided fines, fewer access errors, and measurable productivity gains.
Why Traditional Access Models Don’t Work in Modern Healthcare
Traditional access control once felt enough for most healthcare organizations. A user received a role, permissions followed, and systems stayed manageable. However, healthcare delivery has changed faster than many access strategies. Teams now work across departments, digital tools keep multiplying, and oversight expectations continue to rise.
Because of this shift, many organizations are seeing their older access models stretch beyond their limits. What used to be manageable with directory roles and manual approvals now creates delays, blind spots, and growing operational stress. Therefore, leaders who once trusted their access framework are starting to question whether it still supports the scale and speed their environment demands.
1. Workforce Movement Breaks Static Role Models
Healthcare work rarely stays fixed. Staff rotate, float between units, and take on temporary responsibilities. Vendors and partners also need time-bound entry. Static roles were designed for stable job definitions, not for this level of daily movement.
As a result, identity teams often create quick permission fixes to keep care delivery smooth. Over time, these workarounds pile up and make the access model harder to govern. What looked clean on paper slowly turns into a patchwork that nobody fully trusts.
2. Multi-System Environments Create Permission Sprawl
Modern healthcare enterprises run on many connected systems. EHR platforms, analytics tools, revenue systems, and cloud applications all require user permissions. When each system manages access in its own way, consistency begins to slip.
In addition, manual synchronization between systems rarely keeps pace with real workforce changes. A role updated in one place may remain outdated elsewhere. This gap increases operational risk and forces teams into constant clean-up cycles.
3. Manual Provisioning Slows the Business
Speed matters more than ever in large healthcare environments. New hires must start quickly. Role changes must reflect immediately. Partner access must be tightly controlled but not delayed.
However, traditional access models depend heavily on manual provisioning steps. Therefore, identity teams often become bottlenecks instead of enablers. Requests queue up, approvals stretch out, and business units feel the drag even when security teams are working hard behind the scenes.
4. Compliance Expectations Keep Rising
Healthcare organizations face strict regulatory oversight. Audit teams expect clear proof showing who had access, why they had it, and when it changed. Older access models were not designed with this level of audit visibility in mind.
Because of that, preparing for audits becomes a reactive exercise. Teams pull reports from multiple systems, reconcile role definitions, and investigate exceptions under time pressure. The more complex the environment becomes, the harder it gets to present a clean, defensible access story.
By moving toward a modern healthcare RBAC foundation, they reduce operational drag, improve governance clarity, and support the pace at which today’s healthcare enterprises are expected to run.
What Is An RBAC (Role-Based Access) Platform?
An RBAC platform assigns system permissions based on job roles, helping healthcare organizations control who can view, use, or change sensitive information.
An RBAC platform is a system that manages user permissions by linking access rights to defined job roles. Instead of giving access one user at a time, the platform assigns permissions based on what a person’s role requires.
In healthcare environments, this means a nurse, physician, or billing specialist receives the access needed to perform daily tasks, no more and no less. When someone changes teams or leaves the organization, the platform updates or removes permissions automatically.
As a result, healthcare RBAC helps large organizations maintain consistent control, reduce manual work, and support audit readiness across many connected systems.
How The Platform Works
A healthcare RBAC platform works by defining roles, mapping permissions, connecting identity data, and then applying access automatically as people join, change jobs, or leave.
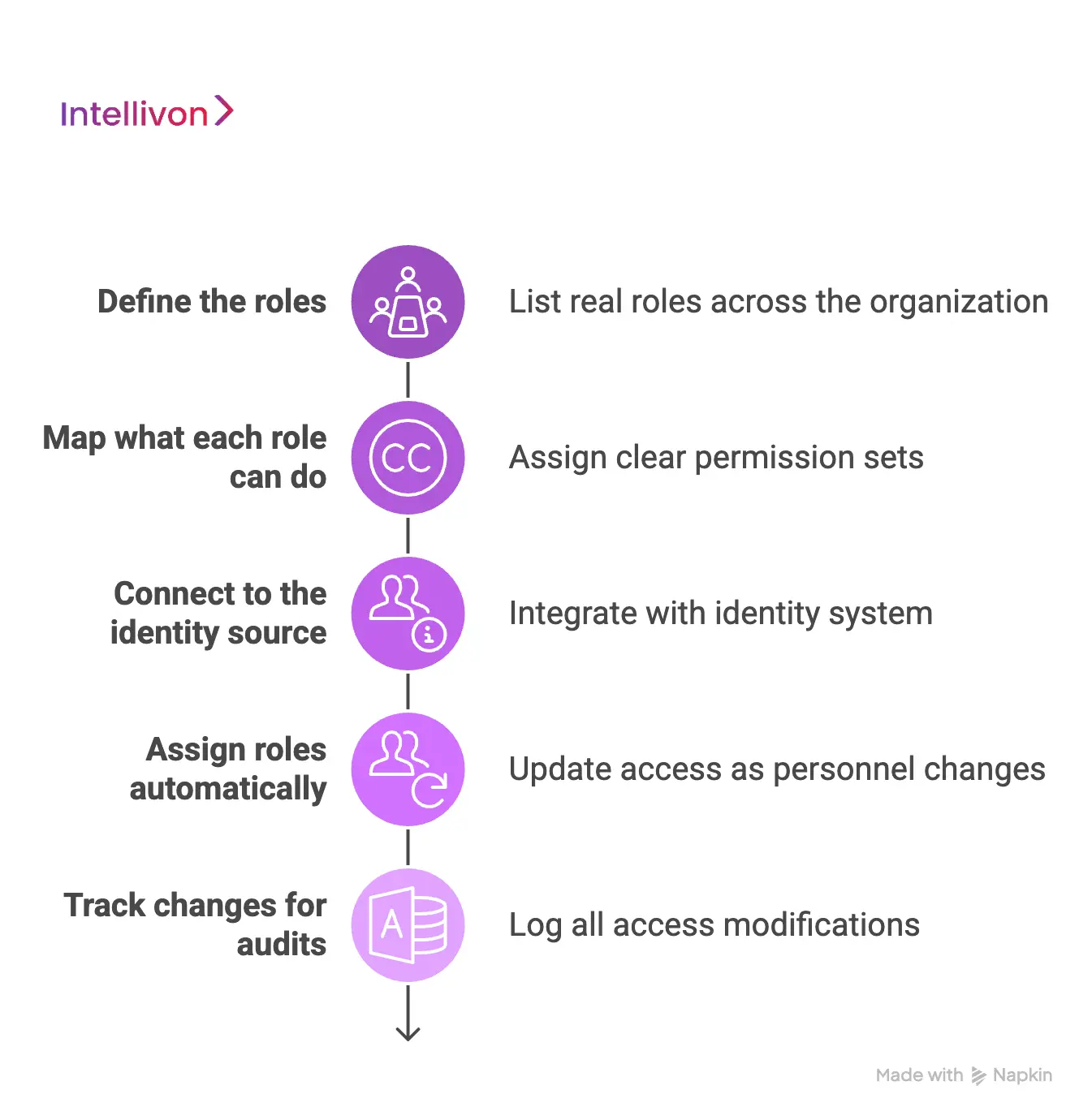
Step 1: Define the roles
First, the team lists the real roles used across the organization. These roles match job duties, not just job titles. Therefore, the role set stays practical and easier to manage.
Step 2: Map what each role can do
Next, each role gets a clear permission set. This includes what data a role can view, what actions it can take, and which systems it can use. In addition, teams document limits, so nobody guesses later.
Step 3: Connect to the identity source
Then the platform connects to your identity system, like a directory or IAM tool. It pulls user details such as department, location, and employment type. However, the platform only uses the fields that matter for access decisions.
Step 4: Assign roles automatically
After that, the platform assigns the right role when a person joins. When someone changes teams, it updates the role. When someone leaves, it removes access. Therefore, access stays aligned without constant manual tickets.
Step 5: Track changes for audits
Finally, the platform logs role assignments, permission changes, and exceptions. This creates a clear record of who had access, why, and when it changed. As a result, audit work becomes faster and less stressful.
Modern healthcare environments move too fast for manual, role-by-role access control. A well-designed healthcare RBAC platform keeps permissions aligned, audit-ready, and easy to manage at scale.
RBAC Platform vs IAM Platform: What Healthcare Enterprises Need to Know
Many healthcare organizations already run an IAM system and assume it fully covers role-based control. In practice, the two serve related but different purposes. IAM focuses on who the user is and how they sign in. An RBAC platform focuses on what the user is allowed to do once inside the environment.
As healthcare ecosystems grow more complex, this difference starts to matter. Identity alone does not keep permissions aligned across dozens of applications, rotating staff, and strict audit expectations. Therefore, understanding where IAM stops and where healthcare RBAC begins helps teams plan their access strategy with far more clarity.
RBAC Platform vs IAM Platform: Side-by-Side Comparison
| Area | IAM Platform | Healthcare RBAC Platform |
| Primary focus | Identity authentication and user lifecycle | Role-based permission governance |
| Core question answered | Who is the user? | What should this user be allowed to do? |
| Typical functions | Login control, MFA, user provisioning | Role design, permission mapping, access alignment |
| Scope in healthcare | Directory and sign-in management | Cross-application permission consistency |
| Handling workforce movement | Limited role depth | Built for role changes and rotations |
| Audit visibility | Identity events | Role and permission traceability |
| Enterprise scale fit | Foundational layer | Governance platform for complex environments |
IAM remains essential for managing identities and securing sign-in flows. However, as healthcare environments expand, identity control alone does not keep permissions clean, consistent, or audit-ready.
A dedicated healthcare RBAC platform fills that gap by aligning roles, permissions, and real workforce behavior. When both work together under the right architecture, organizations gain stronger governance, faster operations, and a far clearer path to enterprise-scale access control.
Key Capabilities of an Enterprise Healthcare RBAC Platform
An enterprise healthcare RBAC platform must support role lifecycle control, cross-system permission management, automated provisioning, and clear audit visibility to scale safely.
A basic role setup is not enough for large healthcare environments. Enterprise teams need a healthcare RBAC platform that keeps access consistent across many systems while still staying easy to govern. The right capabilities reduce manual work, improve visibility, and support compliance without slowing operations.
Below are the capabilities that matter most.
1. Role Engineering and Lifecycle Management
Strong platforms help teams design roles that match real job duties. They also track how roles change over time. Therefore, access stays aligned even as departments grow or responsibilities shift.
In addition, lifecycle controls help retire unused roles and prevent role sprawl. This keeps the role model clean and easier to audit.
2. Identity Source Integration
An enterprise RBAC platform must connect cleanly with the organization’s identity system. This usually includes directories and IAM tools that store user attributes.
Because of this connection, the platform can read trusted user data and apply roles automatically. Teams no longer depend on manual updates to keep permissions accurate.
3. Multi-Application Permission Orchestration
Healthcare enterprises run many connected applications. The RBAC platform should push role-based permissions across EHRs, revenue tools, analytics platforms, and cloud apps from one place.
As a result, organizations maintain consistent access rules instead of managing each system separately. This reduces errors and improves control.
4. Policy-Driven Provisioning and Deprovisioning
Automation is a core requirement at enterprise scale. The platform should grant access when a user joins and remove it when the user leaves or changes roles.
Therefore, joiner, mover, and leaver events happen with less manual effort. This also lowers the risk of outdated permissions staying active longer than they should.
5. Audit Visibility and Compliance Controls
The RBAC platform must record who received access, why it was granted, and when it changed.
With this visibility, audit preparation becomes faster and less disruptive. Teams can show clear proof instead of pulling reports from multiple systems.
6. Exception and Emergency Access Handling
Even well-designed roles cannot cover every situation. Sometimes teams need short-term elevated access for urgent care or system support.
A strong platform supports controlled exception workflows. It grants temporary permissions, tracks usage, and removes access automatically after the approved window.
7. Scalability Across Multi-Hospital Environments
Large health systems continue to expand through new facilities, partnerships, and digital programs. The RBAC platform must handle this growth without constant redesign.
When scalability is built in, organizations can onboard new applications, departments, and users without losing governance clarity. This keeps the access model stable as the enterprise evolves.
When these capabilities come together, healthcare RBAC becomes a reliable control layer that supports both security and operational speed.
Architecture Of An RBAC Platform Development
Healthcare RBAC platform architecture connects identity data, role logic, and application permissions through a centralized control model built for scale and audit clarity.
Building a healthcare RBAC platform is not just about defining roles. The architecture must support real-time workforce changes, many connected systems, and strict audit needs.
When the design is layered properly, teams gain visibility and control without slowing operations. Below is how strong enterprise platforms are typically designed.
1. Central Role Management Core
This is the brain of the RBAC platform. It stores role definitions and keeps role logic consistent across the enterprise. Without this core, roles start to drift between systems.
Key responsibilities include:
- Maintain the master role catalog
- Track role lifecycle and ownership
- Prevent duplicate or unused roles
- Support version control for role changes
Because this core stays centralized, governance teams can manage access policy from one trusted place. It also reduces confusion when roles evolve over time.
2. Identity Data Ingestion Layer
The platform must continuously pull trusted user data from identity sources. This includes directories, HR systems, and IAM tools. However, only the right attributes should drive access decisions.
This layer typically handles:
- User profile synchronization
- Department and job mapping
- Employment status updates
- Location and unit alignment
When identity data flows cleanly, role assignment becomes more reliable. As a result, manual corrections drop, and onboarding moves faster.
3. Role-to-Permission Mapping Engine
Once roles are defined, the platform must translate them into actual system permissions. This mapping engine connects business roles with technical access rights across applications.
It usually performs the following tasks:
- Map roles to application entitlements
- Maintain permission catalogs
- Resolve conflicts between systems
- Support fine-grained access rules
Because of this engine, organizations avoid managing permissions one system at a time. The platform keeps access logic consistent across the environment.
4. Provisioning and Deprovisioning Automation
This layer executes the access changes in real time. When users join, move, or leave, the platform updates permissions automatically. Therefore, identity teams do not rely on manual tickets.
Strong automation includes:
- Joiner, mover, leaver workflows
- Time-bound access controls
- Scheduled access reviews
- Exception handling workflows
With automation in place, access stays aligned with workforce changes. This also reduces the risk of lingering permissions.
5. Audit and Compliance Visibility Layer
Healthcare organizations must show clear proof of access decisions. This layer captures every role assignment, permission change, and exception event. Without it, audit preparation becomes painful.
Key capabilities include:
- Access change logging
- Role assignment history
- Exception tracking
- Compliance reporting views
Because everything is recorded in one place, audit teams can quickly validate who had access and why. This lowers both risk and preparation time.
6. Integration and API Framework
Enterprise RBAC platforms must connect smoothly with many internal and external systems. An API (automated request between applications) framework allows the platform to exchange data in real time.
This framework supports:
- Application onboarding workflows
- Real-time permission updates
- Secure partner connections
- Scalable system expansion
When integrations are designed well, the platform grows with the enterprise instead of becoming a bottleneck. It also allows new digital initiatives to plug in without major redesign.
When these layers work together inside a unified healthcare RBAC platform, organizations gain predictable access control, cleaner governance, and the flexibility to scale without constant rework.
Advanced AI Features of an RBAC Platform
As healthcare systems grow, manual role management starts to fall behind. Identity teams spend too much time reviewing access, fixing role gaps, and chasing audit questions. This is where AI begins to add real value.
In a modern healthcare RBAC platform, AI does not replace governance. Instead, it supports teams by spotting patterns, highlighting risks, and recommending cleaner role designs. When used correctly, it reduces noise and helps teams act faster with more confidence.
1. Role Mining and Smart Role Suggestions
AI reviews real user behavior across systems and suggests role groupings that better reflect daily work. This helps teams design roles based on evidence, not guesswork.
Over time, the platform highlights unused permissions and role overlaps. As a result, the role model stays lean and easier to govern.
2. Access Risk Detection
AI continuously scans permission patterns to find unusual or risky access combinations. For example, it can flag when a user receives permissions that do not match their normal job pattern.
Because of this early signal, security teams can review issues before they grow into audit problems.
3. Anomaly Monitoring for Workforce Changes
Healthcare workforces change frequently. AI watches for sudden shifts in access behavior after role changes, transfers, or temporary assignments.
If something looks off, the platform alerts the team for review. Therefore, organizations catch misalignment faster without adding manual checks.
4. Intelligent Access Review Support
Access reviews often take time and pull teams away from higher-value work. AI helps by prioritizing high-risk permissions and highlighting low-risk ones.
This allows reviewers to focus their attention where it matters most. In addition, review cycles become faster and more consistent.
5. Predictive Provisioning Insights
AI studies past joiner, mover, and leaver patterns to anticipate access needs. When a similar user profile appears, the platform can recommend the most likely role set.
This does not replace approval workflows. However, it helps teams move faster while still maintaining control.
AI is not a shortcut for governance, and it should not be treated as one. Its real value inside a healthcare RBAC platform comes from reducing manual noise, improving role accuracy, and helping teams spot risk earlier.
When implemented carefully, AI-supported RBAC gives healthcare enterprises a smarter way to manage access while keeping human oversight firmly in place.
How We Build Enterprise-Grade Healthcare RBAC Platforms
Intellivon builds healthcare RBAC platforms by mapping real job duties to roles, connecting identity sources, standardizing permissions across apps, and adding audit-ready governance.
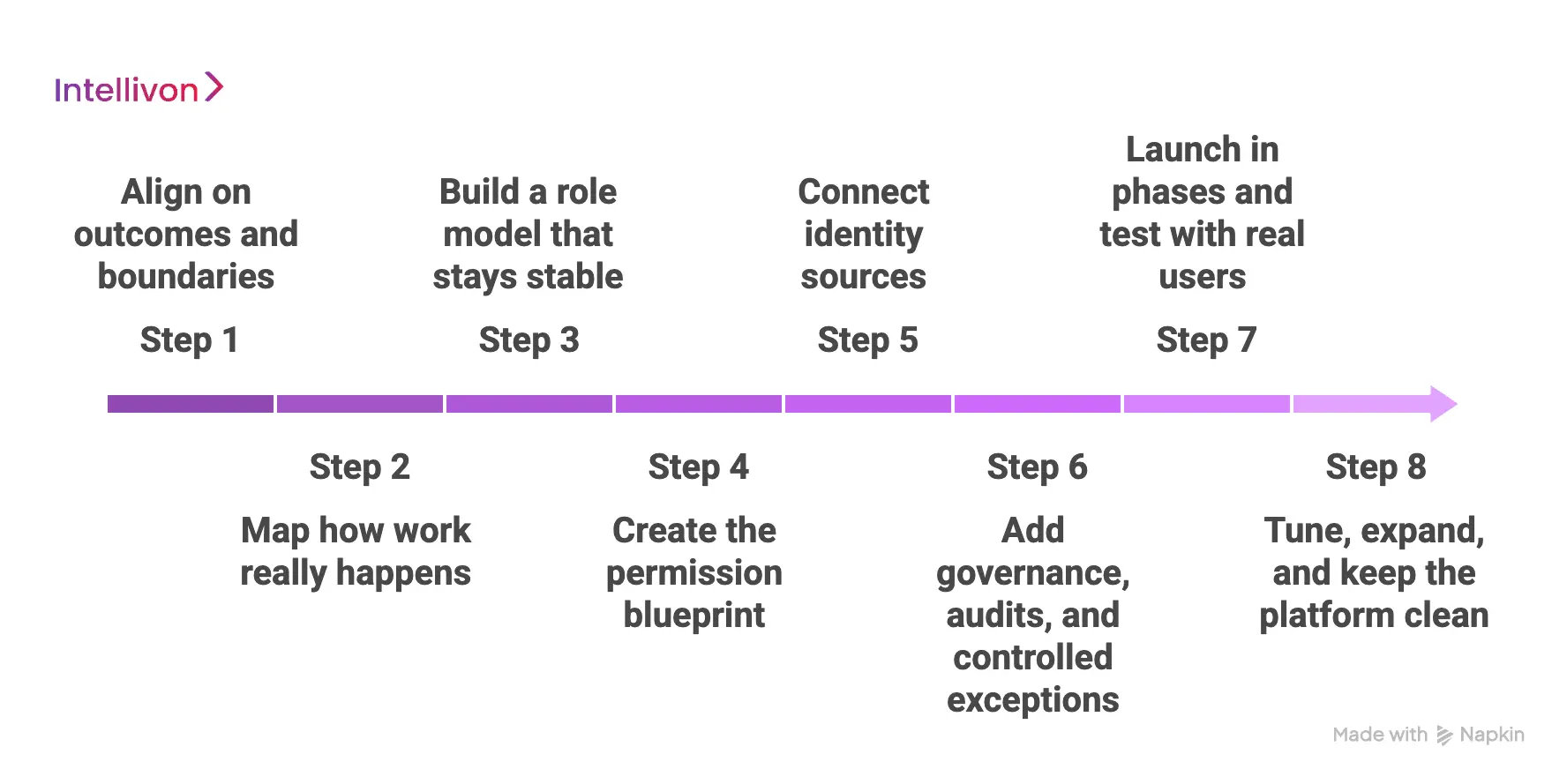
Step 1: Align on outcomes and boundaries
We start with the business goal, not with a role list. Teams tell us what must improve first, like onboarding speed, audit readiness, or partner entry control. However, we also define what is out of scope, so the platform does not turn into a catch-all project.
Then we agree on the systems, user groups, and locations included in phase one. This keeps the work clean and measurable.
Step 2: Map how work really happens
Next, we map the workflows that drive access requests. We look at how staff move across units, how shifts work, and how temporary responsibilities get assigned.
In addition, we identify where manual approvals slow operations. This step matters because roles should match real duties, not old org charts. Therefore, the platform starts from reality, not assumptions.
Step 3: Build a role model that stays stable
Then we design roles with clear ownership and simple rules. We group roles by function and scope, so teams can manage them without constant rework.
However, we also plan for exceptions, because healthcare work has edge cases. We keep the role set tight to avoid role sprawl. As a result, the model stays usable and auditable.
Step 4: Create the permission blueprint
After the role model is ready, we map roles to permissions in each connected system. We build a permission catalog, so every entitlement has a name, a purpose, and a clear owner.
In addition, we handle overlaps between systems, so users do not get duplicate or conflicting rights. This step is where many projects get messy. Therefore, we keep it documented and easy to review.
Step 5: Connect identity sources
Next, we connect the platform to the identity sources, like the directory and HR system. We pick the few user attributes that matter, like department, location, and employment type.
Then the platform assigns roles based on these signals, with approvals where needed. In addition, we set up joiner, mover, and leaver flows so access updates do not depend on tickets. This is where speed and control start showing up together.
Step 6: Add governance, audits, and controlled exceptions
Now we build the guardrails that enterprise teams need. The platform logs role changes, permission updates, and approvals in a clean trail. We also add exception workflows for short-term access, with time limits and tracking.
However, we keep emergency paths controlled, not casual. Therefore, audits become easier, and exceptions stop turning into permanent access.
Step 7: Launch in phases and test with real users
We do not roll out everywhere at once. Instead, we start with a focused group, like one region, one service line, or a set of high-impact apps. We test role accuracy, provisioning timing, and audit logs with real workflows.
In addition, we watch for friction points and then fix them quickly. This phased launch reduces disruption and builds confidence.
Step 8: Tune, expand, and keep the platform clean
After launch, we review what is working and what is drifting. We remove unused permissions, tighten roles that grew too wide, and update mappings when apps change.
In addition, we set a steady review cadence so the model stays healthy over time. This is where long-term value shows up. Therefore, the platform stays stable even as the enterprise grows.
This is how Intellivon builds healthcare RBAC platforms that hold up under real scale. The process stays practical, governed, and built to last, so access control supports growth instead of slowing it down.
When Healthcare Enterprises Should Modernize RBAC
Many healthcare organizations keep their access model in place for years because it still looks fine on the surface. Users can log in, permissions exist, and daily work continues. However, the real pressure usually builds quietly in the background, where manual fixes grow, onboarding slows, and audit prep starts taking more time than it should.
Modernization becomes necessary when the access model begins to slow the business instead of supporting it. The signs below tend to appear early, and teams that notice them quickly usually avoid bigger clean-up work later.
1. Provisioning Requests Keep Piling Up
When identity teams spend most of their day handling access tickets, the model is already under strain. New hires wait longer to start, and role changes move through too many approval steps.
If request queues keep growing month after month, the current setup is no longer keeping pace with the business, and the pressure will keep building.
2. Role Sprawl Is Getting Hard to Manage
Over time, many organizations collect hundreds of overlapping roles, some rarely used, others created as quick fixes for past gaps.
When teams cannot clearly explain what each role allows, governance becomes messy. This usually means the healthcare RBAC model needs cleanup and a more disciplined design.
3. Application Ecosystem Is Expanding Quickly
Healthcare environments rarely stay still. New EHR modules, analytics tools, cloud apps, and partner platforms keep getting added.
If every new system brings fresh access to work and more manual mapping, the environment is becoming harder to control, and the risk of permission gaps starts rising.
4. Audit Preparation Feels Heavy
Audit readiness should feel routine and predictable. However, many teams still pull reports from multiple systems and manually reconcile permissions under time pressure.
When audits begin to feel heavy each cycle, it often signals that the current access model no longer provides the visibility large enterprises need.
5. Workforce Movement Has Increased
Healthcare staffing models have become more fluid over time. Staff rotate across units, take temporary duties, and move between departments more often than before.
If role updates cannot keep up with this movement, access misalignment grows quietly. A modern healthcare RBAC platform is designed to handle this level of change with far less manual effort.
6. Cloud and Digital Programs Are Accelerating
Many healthcare enterprises are expanding digital services and moving more workloads to the cloud. This growth increases the number of users, systems, and access paths that must stay aligned.
When identity teams support this expansion without stronger automation, the pressure compounds. Modernizing RBAC at this stage helps restore control before the environment becomes too complex.
RBAC modernization rarely begins with one big failure. It usually becomes clear when manual work rises, visibility drops, and the environment starts feeling harder to manage than it should.
Organizations that act early stay ahead of the curve. A modern healthcare RBAC platform brings back clarity, reduces operational drag, and supports the pace at which today’s healthcare enterprises need to grow.
Conclusion
Healthcare organizations have outgrown basic access models. As systems expand and teams move faster, permissions must stay accurate without adding more manual work. A well-built healthcare RBAC platform brings that balance. It keeps access aligned, improves audit confidence, and supports daily operations without friction.
However, the real value appears when RBAC is designed with enterprise scale in mind. That is where experience matters. Intellivon helps healthcare enterprises build RBAC platforms that stay governed, flexible, and ready for growth. If your access model is starting to strain, now is the right time to rethink the foundation and move forward with clarity.
Build a Healthcare RBAC Platform With Intellivon
At Intellivon, healthcare RBAC platforms are built as governed enterprise access infrastructure, not as role features loosely added onto identity systems. Every architectural and delivery decision focuses on access accuracy, audit visibility, and cross-system consistency. This allows RBAC programs to operate reliably across hospitals, clinics, digital applications, and partner environments, not just during early rollout.
As healthcare ecosystems grow, access complexity rises with them. Workforce movement increases, application footprints expand, and compliance expectations continue to tighten. Therefore, governance, performance, and traceability must remain steady even as user volume and system connections scale. Organizations keep firm control over who gets access, why it was granted, and how it changes over time, without introducing operational friction or risk exposure.
Why Partner With Intellivon?
- Enterprise-grade healthcare RBAC architecture designed for regulated environments
- Proven delivery across multi-hospital systems and complex care networks
- Compliance-by-design approach with strong audit visibility and policy control
- Secure, modular platform supporting cloud, hybrid, and on-prem deployments
- AI-enabled intelligence for role insights, risk detection, and access optimization
Book a strategy call to explore how Intellivon can help you design and scale a healthcare RBAC platform with confidence, control, and long-term enterprise value.
FAQs
Q1. What is healthcare RBAC, and why is it important?
A1. Healthcare RBAC is a method that gives system permissions based on job roles. It helps hospitals control who can view or change sensitive data. When done right, it reduces manual work and improves audit readiness. It also keeps access aligned as staff join, move, or leave.
Q2. How is healthcare RBAC different from standard RBAC?
A2. Healthcare RBAC must handle rotating staff, multi-hospital environments, and strict compliance rules. Standard RBAC models are often too simple for this level of movement. Therefore, healthcare platforms need stronger automation, clearer audit trails, and tighter role governance.
Q3. When should a healthcare organization upgrade its RBAC platform?
A3. Organizations should consider an upgrade when access tickets keep rising, roles become hard to manage, or audits take too much effort. In addition, rapid cloud growth and new digital programs often expose gaps in older access models.
Q4. What systems should connect to a healthcare RBAC platform?
A4. A strong platform typically connects with identity directories, HR systems, EHR platforms, revenue cycle tools, and major clinical or analytics applications. This connection helps keep permissions consistent across the enterprise.
Q5. How long does it take to implement a healthcare RBAC platform?
A5. Timelines vary based on system complexity, role cleanup needs, and integration scope. Many enterprises begin seeing structured improvements within the first few months. However, full enterprise maturity usually comes through phased rollout and steady governance.