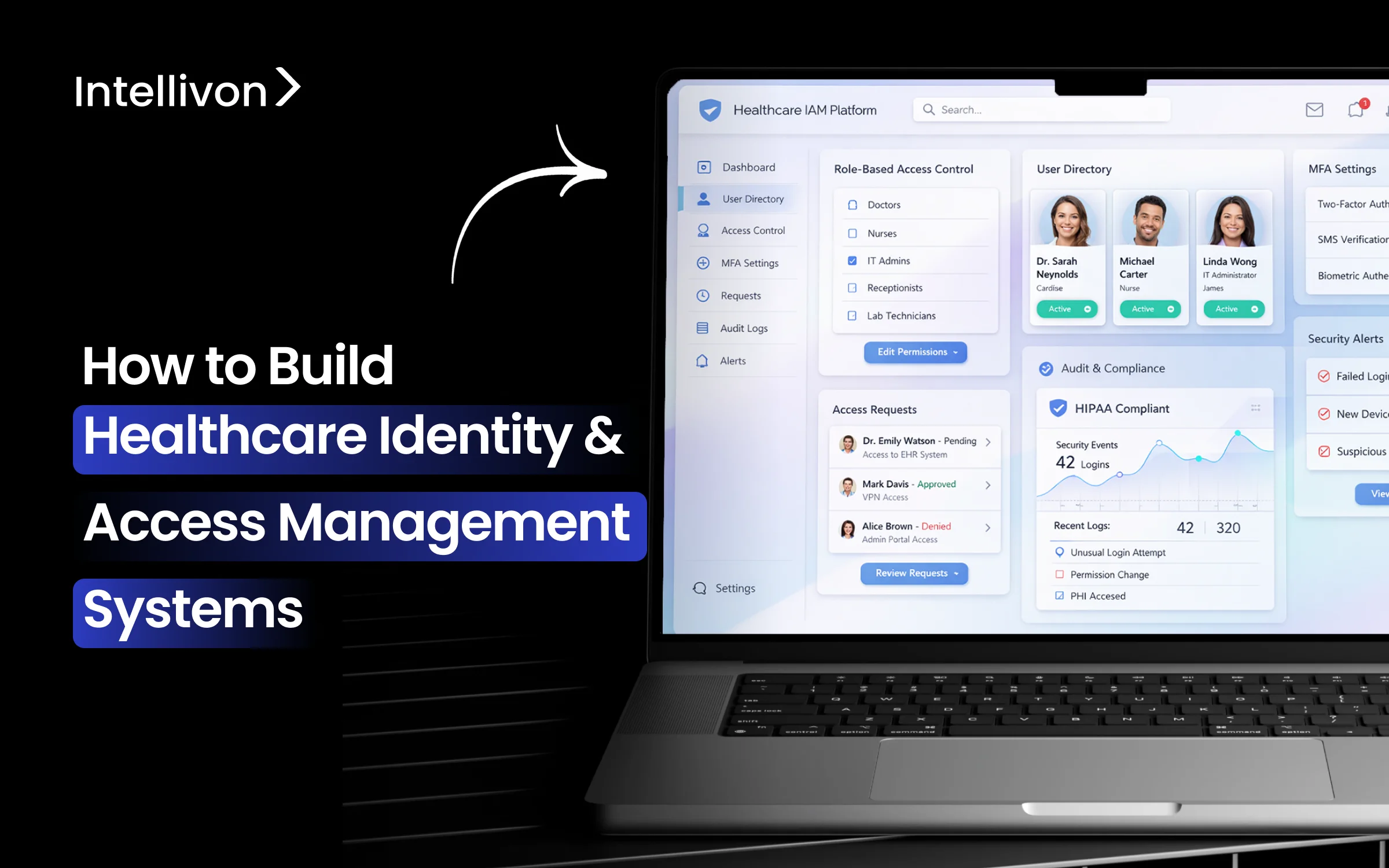
Controlling who can access clinical and operational systems remains one of the hardest problems in modern healthcare enterprises. Here, clinicians, staff, patients, and external partners all require different levels of access, often across multiple apps and under the same time pressure. In many organizations, these access rules have evolved over years of system growth, which makes them difficult to manage consistently.
As healthcare ecosystems become more connected, identity management cannot rely on basic login controls alone. This is where a well-designed healthcare Identity and Access Management (IAM) platform becomes essential. A strong IAM foundation helps organizations verify users properly, apply the right access at the right time, and maintain clear audit visibility without disrupting clinical workflows. In our work at Intellivon, we often see that the challenge is not a lack of security tools, but it is the absence of a unified IAM system across the environment.
In this blog, we will discuss how we build healthcare IAM systems by breaking down the core components, architectural decisions, and practical steps required to deliver secure, compliant, and scalable access control across the entire healthcare enterprise environment.
Why Healthcare Organizations Need Modern IAM Systems Now
Modern IAM systems have become essential for providers that need to stay ahead of rising cyber threats, meet strict regulatory demands, and support enterprise-scale digital transformation. According to Next Move Strategy Consulting, the global healthcare identity and access management market was valued at USD 3.94 billion in 2023 and is projected to reach USD 7.51 billion by 2030, growing at a CAGR of 9.65% between 2024 and 2030.
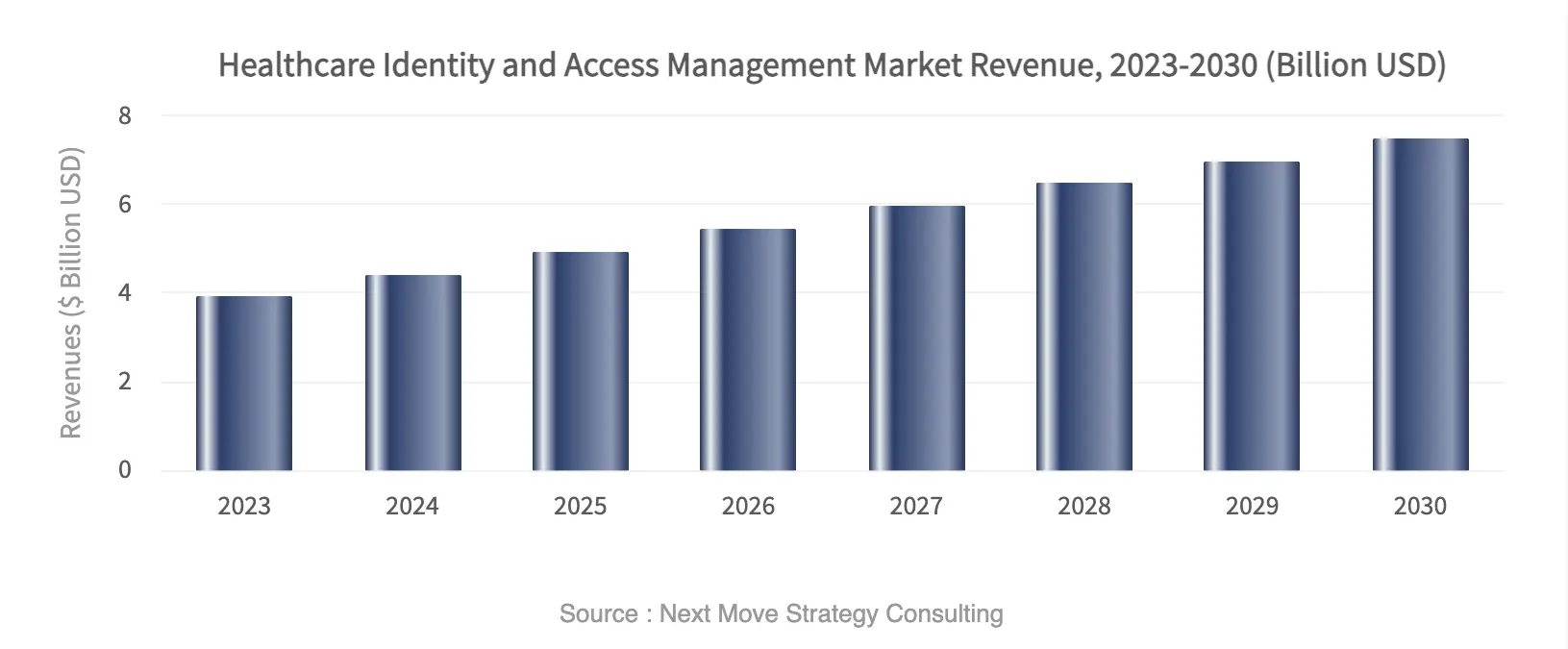
Market Insights:
- Rising cyber threats: Credential misuse and over-permissioning drive many healthcare breaches, especially after telehealth expansion. Modern IAM with Zero Trust, RBAC, and PAM enables real-time monitoring and reduces incidents across large networks.
- Regulatory pressure is increasing: HIPAA, HITECH, and GDPR require granular PHI controls, consent tracking, and audit trails. Many providers now target 99.9% logging coverage. A centralized IAM system simplifies compliance and supports FHIR interoperability.
- Digital transformation is expanding identity complexity: EHR integrations, telemedicine, and hybrid work demand unified identities. Modern platforms deliver SSO and MFA, with organizations reporting up to 70% reductions in clinician administrative effort.
- Clear ROI and competitive advantage: Enterprises often achieve 65–85% fewer helpdesk calls and about 50% risk reduction. With breaches costing millions and the market growing near 13% annually, IAM investments deliver fast returns.
Healthcare providers need modern IAM systems to reduce credential risk, meet strict compliance requirements, manage complex workforces, and deliver secure digital patient access at scale.
1. Escalating Cybersecurity Threats
Identity has become the primary attack surface in healthcare. Threat actors now focus on stolen credentials, privilege abuse, and ransomware entry points. As telehealth and remote access expand, the attack surface grows even faster.
Legacy access controls cannot keep up with this pace. Therefore, many organizations struggle with orphaned accounts, excessive permissions, and slow incident detection.
Modern IAM systems address this gap by enforcing least-privilege access, continuous monitoring, and stronger authentication controls. As a result, security teams gain better visibility and faster response.
2. Regulatory and Compliance Pressure
Healthcare operates under constant regulatory scrutiny. Frameworks such as HIPAA, HITRUST, SOC 2, and regional privacy laws require strict control over who can access protected health information.
However, manual access reviews and fragmented identity stores create audit risk. In addition, regulators increasingly expect real-time visibility into access decisions.
A centralized IAM system simplifies compliance by automating provisioning, enforcing policy controls, and maintaining audit-ready logs. Consequently, organizations reduce both audit fatigue and compliance exposure.
3. Workforce and Ecosystem Complexity
Care delivery is no longer confined to a single hospital. Large health systems now span multiple facilities, partner networks, remote clinicians, and third-party vendors. Each new connection increases identity complexity.
Without a unified approach, access management quickly becomes inconsistent and error-prone. Modern IAM platforms create a single control layer across the ecosystem.
This helps organizations manage workforce access, support telehealth growth, and onboard partners securely without slowing operations.
4. Patient Experience Expectations
Patients now expect the same digital convenience they see in other industries. They want secure portals, fast login, and seamless movement across digital touchpoints.
If access is slow or confusing, satisfaction drops quickly. Modern IAM supports frictionless experiences through SSO, adaptive authentication, and secure self-service.
At the same time, it protects sensitive data behind the scenes. Therefore, providers can improve both security posture and digital engagement together.
Modern IAM has become a core healthcare infrastructure that supports secure access, regulatory confidence, and scalable digital growth across complex care ecosystems.
What Is Healthcare Identity & Access Management (IAM)?
Healthcare identity and access management (IAM) is a centralized security framework that manages user identities and controls access to clinical, financial, and patient systems across healthcare environments.
It is the system that verifies who users are and controls what they can access inside a healthcare environment. Additionally, it manages identities for clinicians, staff, patients, and partners across EHRs, portals, and connected applications. A modern IAM system automates provisioning, enforces least-privilege access, and monitors activity in real time.
As a result, organizations reduce credential risk, improve compliance, and simplify secure access across complex hospital ecosystems.
Why Healthcare IAM Is Different From Enterprise IAM
Healthcare identity environments operate under very different pressures than typical corporate systems. Access decisions in hospitals directly affect patient care, clinician productivity, and regulatory exposure. Therefore, identity controls must balance security with speed and clinical workflow sensitivity.
In addition, healthcare ecosystems are more fragmented. Multiple EHRs, partner systems, medical devices, and patient portals all depend on accurate identity orchestration. As a result, an IAM system that works well in a standard enterprise often struggles in a clinical setting.
Healthcare IAM vs Enterprise IAM
| Area | Healthcare IAM | Traditional Enterprise IAM |
| Primary focus | Patient safety and secure clinical access | Employee productivity and IT security |
| User types | Clinicians, patients, vendors, devices | Mostly employees and contractors |
| Workflow sensitivity | Very high, impacts care delivery | Moderate, mainly business operations |
| Compliance pressure | HIPAA, HITRUST, and regional health laws | SOC 2, ISO, and general data protection |
| Access urgency | Requires emergency and break-glass access | Rarely needs emergency overrides |
| System complexity | Multi-EHR and clinical integrations | Standard business applications |
| Risk impact | Direct patient and regulatory risk | Primarily business and data risk |
In short, healthcare IAM demands deeper clinical awareness, tighter governance, and greater architectural flexibility. Organizations that recognize this early are far more likely to build identity programs that scale safely across complex care environments.
Key Stakeholders in Healthcare IAM
A healthcare IAM program affects far more than the IT team. Access decisions touch clinical care, operations, compliance, and patient experience. Therefore, successful implementations consider the needs of every identity group in the ecosystem.
Below are the primary stakeholders modern IAM systems must support.
1. Clinicians and Care Teams
Doctors, nurses, and allied health staff depend on fast and reliable access. Even small login delays can disrupt care workflows.
IAM must support quick authentication, role-based access, and emergency access when needed. At the same time, it must enforce least-privilege controls in the background.
2. Administrative and Operations Staff
Billing teams, schedulers, and support staff require access to financial and operational systems. Their access often changes as roles shift.
Therefore, automated provisioning and timely deprovisioning are critical to reduce errors and audit risk.
3. Patients and Caregivers
Patients increasingly use portals, mobile apps, and digital front doors. They expect secure but simple access.
IAM must support identity verification, consent management, and self-service features. When done well, it improves both security and patient satisfaction.
4. Third-Party Vendors and Partners
Health systems rely heavily on external vendors, contractors, and partner organizations. However, third-party access is a common source of risk.
Modern IAM platforms provide time-bound access, strong authentication, and continuous monitoring to control this exposure.
5. Medical Devices and Connected Systems
Clinical devices and IoMT endpoints are growing rapidly. Many now connect directly to hospital networks and applications. IAM must extend beyond human users to manage device identities, enforce trust, and support Zero Trust architectures.
In summary, healthcare IAM succeeds only when it addresses the full identity landscape. Organizations that design for all stakeholders early build stronger security, smoother workflows, and more resilient digital operations.
Where IAM Systems Sit in Large Hospital Architectures
In large hospitals, the IAM system operates as a centralized identity control layer that brokers authentication, enforces access policies, and feeds security monitoring across clinical and business systems.
In modern health systems, the IAM system does not sit at the edge. It operates at the center of the digital environment. Every login, token exchange, and access decision flows through this identity control plane.
This placement is intentional. Hospitals run hundreds of connected applications, multiple EHR environments, and growing API traffic. Without a centralized identity broker, access quickly becomes fragmented and difficult to govern. Therefore, leading organizations treat IAM as core infrastructure rather than a standalone security tool.
1. Front-End Access Layer
This is where human users interact with the identity platform. It typically includes:
- Single Sign-On portals
- Multi-factor authentication
- Clinician fast-access workflows
- Patient and caregiver login flows
The objective is to provide fast, low-friction entry into approved systems while maintaining strong authentication controls.
2. Core Identity Control Layer
This layer acts as the decision engine of the IAM system. It manages identities, roles, and policy enforcement across the enterprise. Key capabilities include:
- Unified identity directory
- Role and attribute-based access controls
- Identity federation and brokering
- Policy decision and enforcement services
- Integration with EHRs, Active Directory, and enterprise apps
Because this layer connects the entire ecosystem, accuracy and scalability are critical. Design weaknesses here often create long-term security and operational risk.
3. Back-End Security and Monitoring Layer
Behind the scenes, IAM continuously feeds security and compliance platforms. This layer supports:
- SIEM and SOC telemetry
- Immutable audit logging
- User and entity behavior analytics
- Compliance and access reporting
As a result, security teams gain real-time visibility into access activity across the environment. This visibility is essential for Zero Trust enforcement, breach response, and regulatory audits.
In large hospital environments, IAM delivers the most value when positioned as a centralized identity control plane. Organizations that architect it this way gain stronger governance, cleaner access flows, and a foundation that scales with future digital and AI initiatives.
Core Components of a Healthcare IAM Architecture
A healthcare IAM architecture includes identity lifecycle management, strong authentication, access control, privileged access management, single sign-on, and identity governance working together as a unified control layer.
Building a healthcare IAM system requires more than adding login controls. It involves several tightly connected components that manage identities from onboarding to continuous monitoring. When these pieces work together, organizations gain secure access, better compliance, and smoother clinical workflows.
Below are the core components every enterprise healthcare IAM architecture should include:
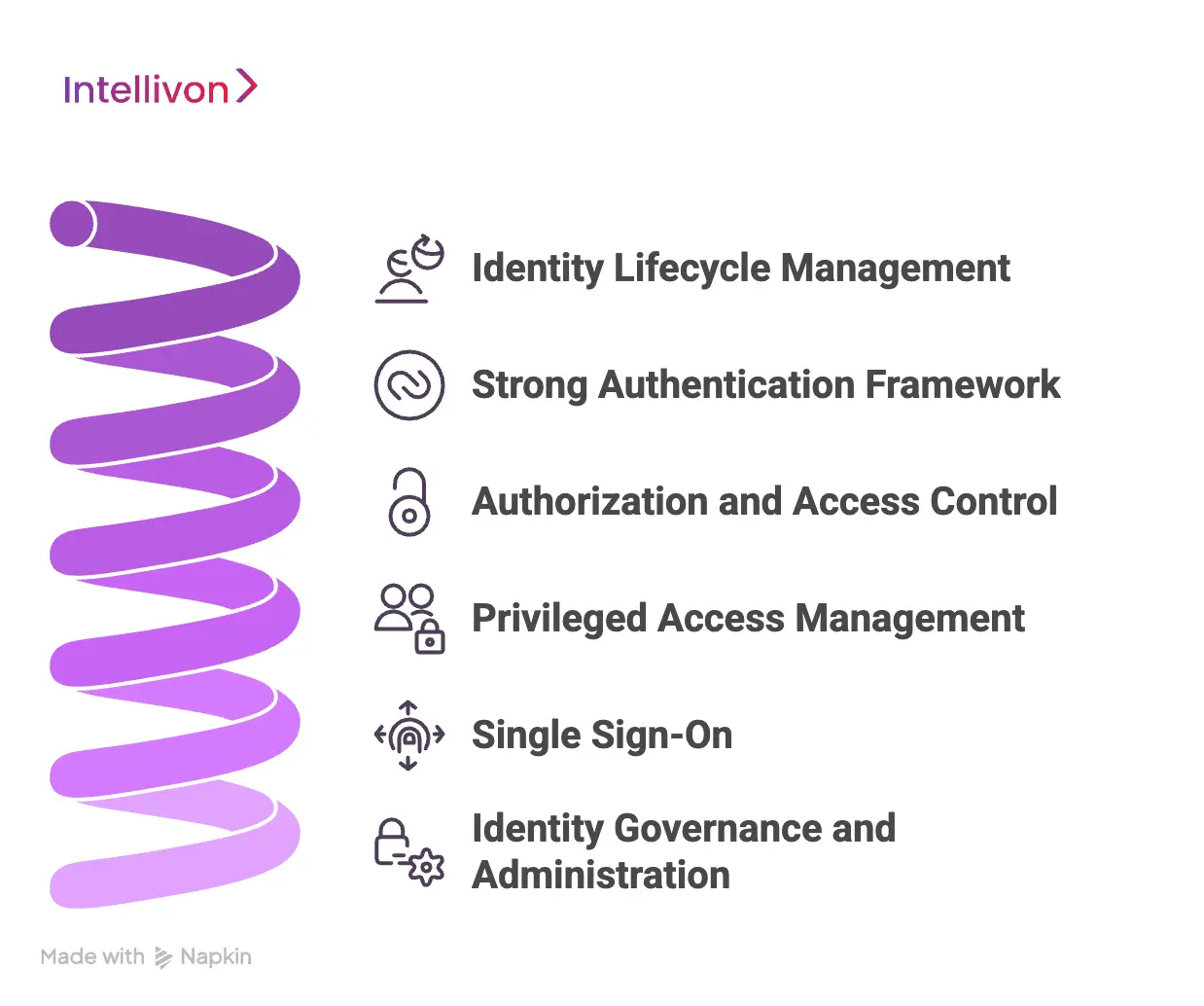
1. Identity Lifecycle Management
This component manages the full user journey from onboarding to offboarding. It ensures the right access is granted and removed at the right time.
Key functions include:
- Automated provisioning for new users
- Role updates when responsibilities change
- Immediate deprovisioning when users leave
- Joiner, mover, leaver workflows
When lifecycle management is automated, organizations reduce orphaned accounts and manual errors.
2. Strong Authentication Framework
Authentication verifies that users are who they claim to be. In healthcare, this step must be both secure and fast for clinicians.
Modern IAM systems typically support:
- Multi-factor authentication
- Passwordless login options
- Biometric verification
- Risk-based authentication
Stronger authentication reduces credential abuse while keeping workflows efficient.
3. Authorization and Access Control
After authentication, the system must decide what each user can access. This is where authorization policies apply.
Most healthcare IAM platforms use:
- Role-Based Access Control
- Attribute-Based Access Control
- Policy-based access rules
- Context-aware access decisions
Well-designed access control enforces least privilege without slowing clinical work.
4. Privileged Access Management
Privileged accounts carry the highest risk in any environment. Therefore, they require additional controls and monitoring.
PAM capabilities typically include:
- Secure admin credential vaulting
- Session monitoring and recording
- Just-in-time privileged access
- Break-glass emergency access
Strong PAM controls help prevent insider misuse and high-impact breaches.
5. Single Sign-On (SSO)
Single Sign-On improves both security and user experience. It allows users to access multiple systems with one secure login.
In healthcare environments, SSO helps:
- Reduce password fatigue for clinicians
- Speed up access to EHR systems
- Lower helpdesk call volume
- Improve user satisfaction
However, SSO must be implemented carefully to avoid creating a single point of failure.
Identity Governance and Administration
Identity governance provides oversight and policy control across the IAM environment. It ensures access remains appropriate over time.
Core governance capabilities include:
- Access reviews and certifications
- Policy enforcement
- Role mining and optimization
- Audit trail management
With strong governance, organizations stay audit-ready and maintain clean access controls.
When these components operate as a unified architecture, healthcare organizations gain far more than basic security. They build a scalable identity foundation that supports compliance, clinical efficiency, and long-term digital growth.
Step-by-Step: How We Build a Healthcare IAM System
An enterprise healthcare IAM system is built through structured discovery, architecture design, phased rollout, and continuous governance, with tight integration across EHRs, directories, and security monitoring.
Large health systems do not fail because they lack tools. They fail because identity programs start without a clear blueprint, clean data, and rollout discipline. Therefore, we build healthcare IAM systems as a regulated enterprise infrastructure from day one.
At Intellivon, we combine consulting depth with AI-enabled delivery to reduce manual effort, speed up governance, and keep programs predictable at scale. Below is the step-by-step approach we use with large enterprises.
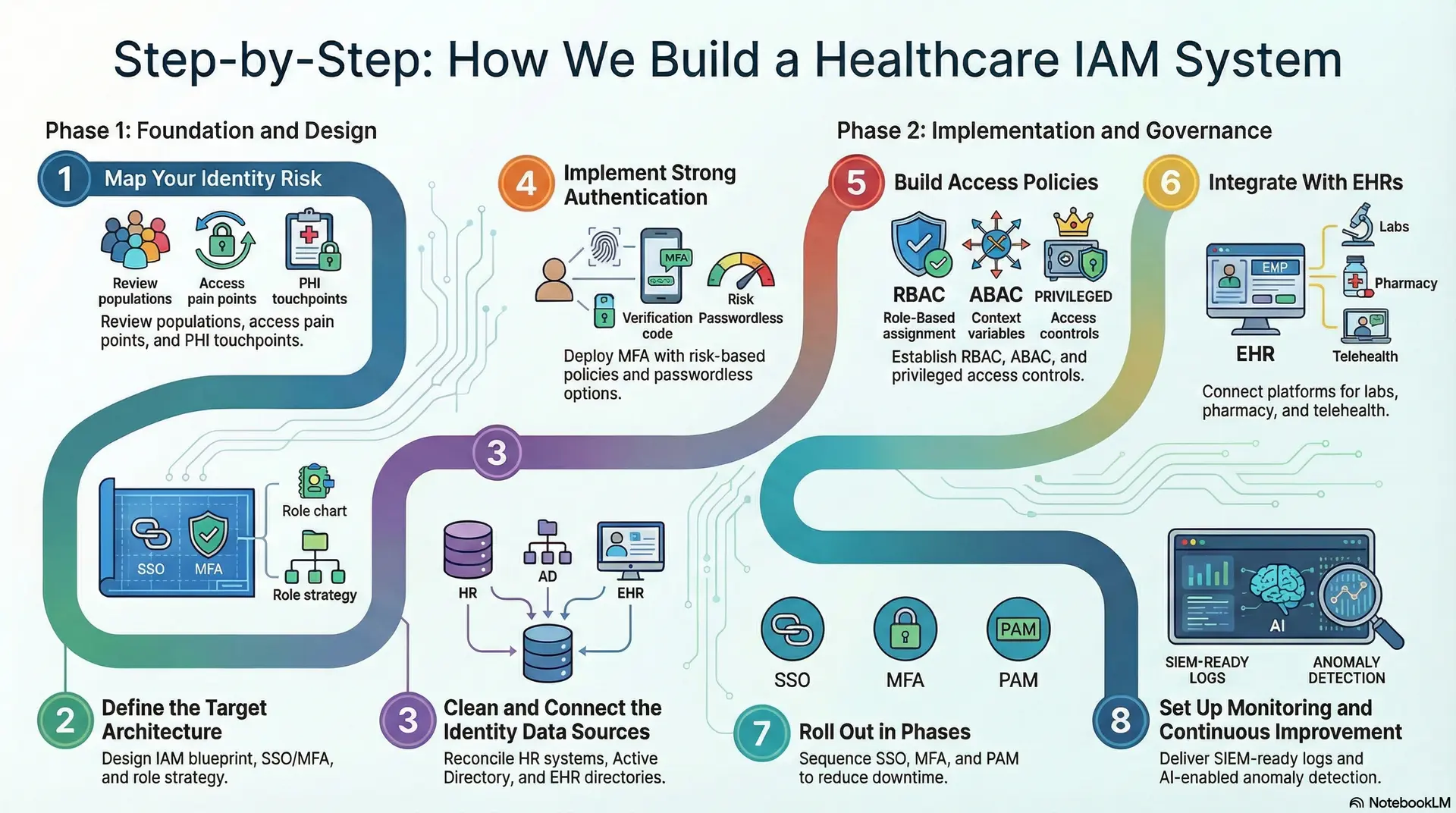
Step 1: Map Your Identity Risk
We start by understanding how access works today across clinical and business systems. Here, we also document where identity risk is hiding.
At the same time, we review:
- User populations, including vendors and contractors
- Current login paths and access pain points
- Orphan accounts and over-permissioning patterns
- Audit findings and security incidents
- PHI touchpoints across systems
This step creates a clear baseline for decisions and prioritization.
Step 2: Define the Target Architecture
Next, we design the IAM blueprint that fits your environment. We align it with your cloud strategy and regulatory posture.
We define:
- Centralized vs federated identity model
- IAM system placement across hospital architecture
- SSO and MFA design for clinical workflows
- Role and attribute strategy for least privilege
- Break-glass access rules for urgent scenarios
This blueprint prevents rework later, which saves time and cost.
Step 3: Clean and Connect the Identity Data Sources
IAM only works when identity data is accurate. Therefore, we connect and reconcile the systems that feed identities and roles.
Common sources include:
- HR systems for joiner and leaver events
- Active Directory or Entra ID for authentication
- EHR user directories and role mappings
- Vendor access systems and ticket workflows
We also fix duplication and inconsistent role naming early.
Step 4: Implement Strong Authentication
We deploy authentication controls in a way that supports speed and safety. Clinicians should not lose time due to security friction.
We implement:
- MFA with risk-based policies
- Passwordless options were appropriate
- Device trust and session controls
- Step-up authentication for sensitive actions
This reduces credential risk while maintaining workflow efficiency.
Step 5: Build Access Policies
Access rules must reflect real clinical work. They also need to remain consistent across facilities and partner sites.
We build:
- RBAC for core job functions
- ABAC for context, such as location and shift
- Privileged access controls for admin roles
- Just-in-time access for high-risk systems
We test these policies with real users before expanding the scope.
Step 6: Integrate With EHRs
Integration is where many programs stall. Therefore, we plan and execute integrations in a controlled sequence.
We typically integrate:
- EHR systems and patient portals
- Lab, pharmacy, and imaging platforms
- Billing and revenue cycle systems
- Telehealth and remote care tools
- Partner systems and HIE connections
When legacy systems create barriers, we use secure connectors and middleware patterns to avoid disruption.
Step 7: Roll Out in Phases
Large-scale rollouts require careful sequencing. We start with the controls that reduce risk quickly, then expand governance.
A typical rollout sequence is:
- SSO rollout for high-use systems
- MFA enforcement for key user groups
- PAM for privileged and admin access
- IGA for access reviews and certifications
This approach reduces downtime and builds trust with clinical teams.
Step 8: Set Up Monitoringand Continuous Improvement
IAM is never “done.” It must adapt as roles, systems, and threats change. Therefore, we set up continuous monitoring and governance.
We deliver:
- SIEM-ready logs and access visibility
- Real-time alerts for risky behavior
- Automated access reviews and reporting
- Audit evidence packages for compliance teams
We also use AI to highlight anomalies and assess drift faster.
This step-by-step approach helps enterprises build an IAM system that scales across hospitals, partners, and digital channels. It also reduces long-term operational risk while supporting faster, safer growth.
Best Middleware Solutions for IAM–Legacy Integration in Hospitals
Middleware solutions help healthcare IAM systems connect with legacy hospital applications by translating protocols, normalizing identity data, and enabling secure API-based access without full system replacement.
Many hospitals still depend on legacy EHRs, lab systems, and mainframe applications. However, these systems were not designed for modern identity orchestration. As a result, direct IAM integration often becomes slow, costly, and risky.
Middleware solves this problem by acting as a secure translation layer. It connects modern IAM platforms with older systems without forcing a full rip-and-replace. Therefore, organizations can modernize access controls while keeping critical clinical systems stable. Below are the most effective middleware approaches used in large healthcare environments:
1. Healthcare Integration Engines
Healthcare-specific integration engines are often the fastest path to IAM connectivity. These platforms understand clinical data standards and common EHR patterns.
Common capabilities include:
- HL7 and FHIR message handling
- Prebuilt EHR connectors
- Real-time data transformation
- Identity attribute mapping
Tools such as Mirth Connect and Redox are widely used in complex hospital environments. They reduce custom coding and speed up deployment timelines.
2. Enterprise Health Data Platforms
Some organizations prefer broader interoperability platforms that unify data across the enterprise. These solutions help normalize identity information coming from fragmented systems.
Key strengths include:
- Cross-system identity consolidation
- Legacy adapter support
- FHIR-enabled data services
- Scalable data exchange across facilities
Platforms like InterSystems HealthShare are often used in multi-hospital networks that need strong data consistency along with IAM integration.
3. API Gateways and Event Streaming Platforms
In modern architectures, API gateways and event platforms play a growing role. They allow IAM systems to interact with legacy databases indirectly and securely.
Typical use cases include:
- Secure API exposure for older systems
- Message queuing for identity events
- Real-time provisioning triggers
- Traffic control and rate limiting
Technologies such as Kafka and RabbitMQ support high-volume environments where identity events must flow reliably between systems.
4. Open Source and Lightweight Options
Some health systems explore open-source middleware to control costs. These tools can work well in targeted use cases but usually require more engineering effort.
Common examples include:
- HAPI FHIR servers
- Custom REST wrappers
- Lightweight message brokers
These options provide flexibility. However, they often demand stronger in-house expertise and ongoing maintenance discipline.
The right middleware strategy allows healthcare organizations to modernize identity controls without disrupting critical legacy systems. When chosen carefully, it reduces integration risk, speeds up IAM rollout, and creates a cleaner path toward long-term Zero Trust maturity.
How to Ensure HIPAA Compliance During IAM Integration
HIPAA-compliant IAM integration requires risk assessment, strong access controls, encryption, continuous monitoring, and workforce governance to protect PHI across legacy and modern systems.
Integrating an IAM system into a healthcare environment introduces both opportunity and risk. If done correctly, it strengthens PHI protection and audit readiness. However, poor execution can create new compliance gaps. Therefore, organizations must treat HIPAA alignment as a core design requirement, not a final checklist.
Below are the key practices that help large health systems stay compliant during IAM modernization.
1. Conduct Risk Assessment and PHI Mapping
Start by identifying where protected health information lives and how users access it today. This step helps expose hidden access paths and weak controls.
Key actions include:
- Map PHI touchpoints across clinical and business systems
- Review existing access policies and gaps
- Identify high-risk privileged accounts
- Validate vendor and partner access paths
- Align with HITRUST CSF where applicable
A structured assessment reduces surprises later in the program.
2. Implement Strong Technical Safeguards
HIPAA expects strict control over identity, access, and data protection. Modern IAM platforms help enforce these controls consistently.
Essential safeguards include:
- Multi-factor authentication for sensitive access
- Role-based and attribute-based access controls
- Zero Trust verification at the login and session level
- Automated provisioning and deprovisioning
- Encryption of PHI in transit and at rest using FIPS 140-2 validated modules
- Secure API gateways for legacy system access
- FHIR and SMART-based authorization were supported
When these controls are automated, compliance becomes easier to maintain.
3. Enable Continuous Monitoring and Audit Readiness
HIPAA compliance is not a one-time activity. Organizations must maintain ongoing visibility into access behavior.
Recommended practices include:
- Stream IAM logs into SIEM platforms
- Monitor anomalous user behavior in real time
- Maintain immutable audit trails
- Run regular penetration tests
- Conduct periodic mock audits
Continuous monitoring helps security teams detect and respond faster.
4. Strengthen Workforce Training and Governance
Technology alone does not ensure compliance. Human behavior remains a major risk factor.
Organizations should:
- Provide role-based security training
- Run phishing simulation programs
- Enforce periodic access reviews
- Establish clear access governance policies
- Maintain Business Associate Agreements with IAM vendors and middleware partners
Strong governance reduces policy drift over time.
When healthcare organizations embed these controls into their IAM program, HIPAA compliance becomes far more sustainable. More importantly, they build an identity foundation that supports secure growth, stronger audit confidence, and long-term Zero Trust maturity.
Healthcare IAM Use Cases Across the Ecosystem
Real-world healthcare IAM deployments show that phased integration, strong middleware, and automated governance can reduce orphaned accounts, speed clinician access, and strengthen HIPAA compliance.
Enterprise IAM programs prove their value when they work inside real hospital environments. Across large health systems, middleware-driven IAM deployments have helped teams modernize access without disrupting legacy clinical platforms.
The following examples show how structured IAM execution delivers measurable security and operational gains.
1. Teaching Hospital IAM Modernization
A U.S. non-profit teaching hospital moved from a legacy on-prem IAM to SailPoint Identity Security Cloud with Non-Employee Risk Management. Epic SER connectors and middleware linked the EHR, SumTotal LMS, and ServiceNow.
Key outcomes included centralized user lifecycle management, automated clinician onboarding, and better scalability for future mergers. Manual effort dropped significantly while access governance improved.
2. Regional Healthcare Network Identity Transformation
A healthcare network with more than 25,000 employees addressed HIPAA gaps, orphaned accounts, and slow clinical access. IAMCompass middleware enabled RBAC with just-in-time provisioning across legacy systems.
The results were clear. Orphaned accounts fell by 98 percent, full audit visibility was achieved, and clinician access times dropped from hours to minutes without workflow disruption.
3. Midwest Multi-Hospital Provisioning Automation
A 12-hospital system deployed NetIQ Identity Manager to connect Kronos, Epic, Active Directory, and Lotus Notes through automated workflows.
This integration delivered cross-site provisioning automation, stronger identity orchestration for legacy applications, and measurable efficiency gains across the network.
4. Major Hospital Network IAM Optimization
A large hospital network implemented a healthcare-specific IAM platform from Avatier, including shift-change protocols and legacy clinical integrations.
The organization reported 70% less administrative time, 85% faster clinician access, 99.9% HIPAA logging coverage, and 65% fewer helpdesk calls. The deployment also handled complex cases such as locum tenens access.
5. Privileged Access Modernization in Healthcare
A hospital client working with Integral Partners implemented SailPoint and CyberArk together to automate privileged lifecycle management across legacy environments.
The program enforced least-privilege access, resolved audit findings, and reduced operational disruption through automated password rotation and approval workflows.
These examples show that when healthcare IAM is implemented with the right architecture, middleware, and governance model, organizations reduce risk quickly while improving access speed and operational control.
Key Challenges in Healthcare IAM Implementation
Healthcare IAM programs often struggle with legacy fragmentation, clinical workflow sensitivity, identity data quality, and governance complexity across large hospital ecosystems.
Building an IAM system in healthcare is rarely a clean, linear project. Most large providers operate in environments shaped by decades of system growth, mergers, and regulatory pressure.
Therefore, even well-funded programs can face delays and hidden risks if these challenges are not addressed early. Below are the most common barriers enterprises encounter during IAM implementation:
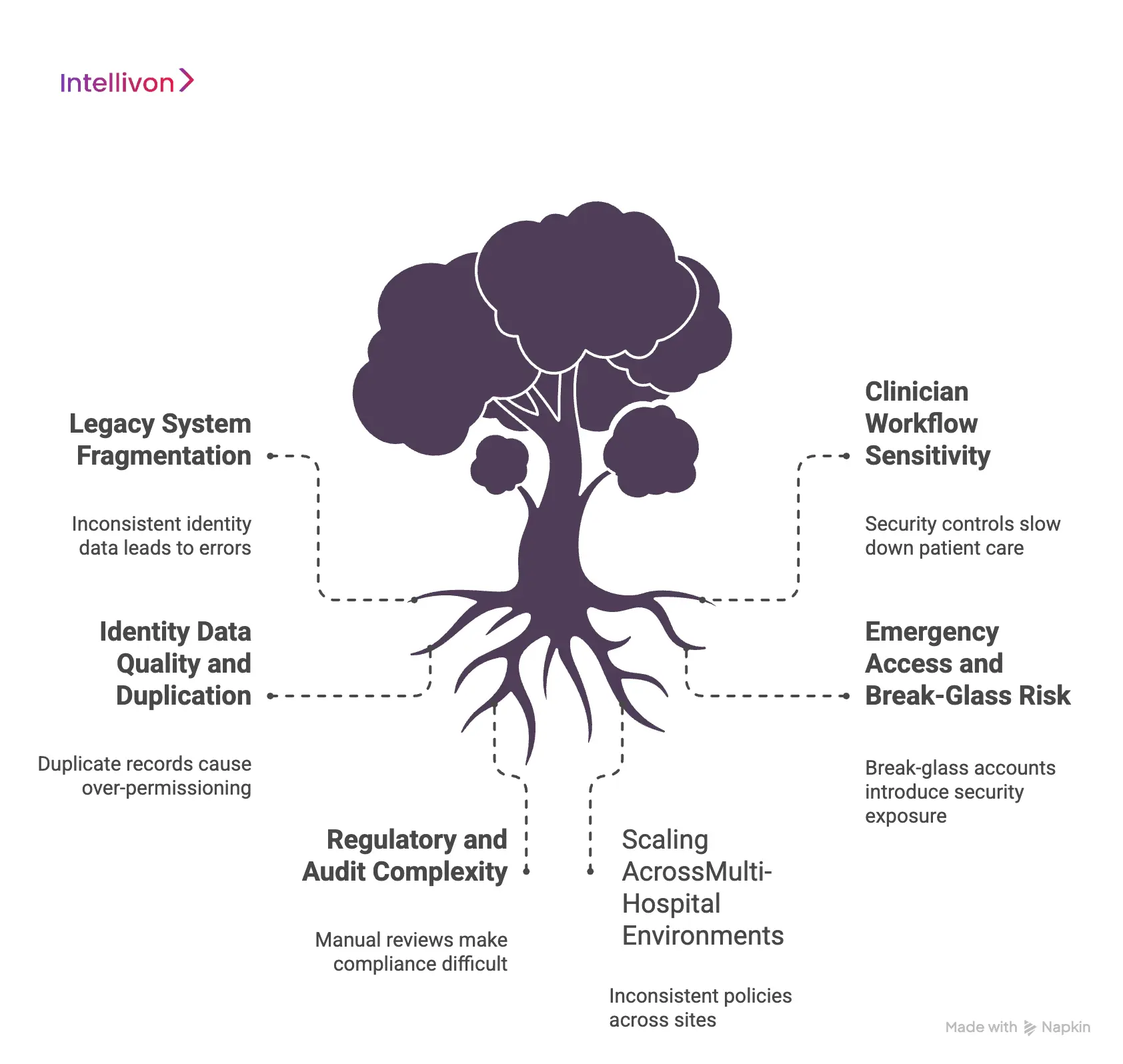
1. Legacy System Fragmentation
Many hospitals still run older EHRs, departmental systems, and custom applications that were never designed for modern identity controls. As a result, integration often requires adapters, middleware, and careful sequencing.
Without a clear plan, identity data becomes inconsistent across systems. Over time, this creates provisioning errors, duplicate accounts, and audit gaps. Successful programs usually invest early in integration strategy and data cleanup.
2. Clinician Workflow Sensitivity
Healthcare access controls must move at the speed of care. Even small login delays can frustrate clinicians and impact productivity. Therefore, security teams cannot deploy controls that slow frontline workflows.
Balancing strong authentication with fast access is one of the hardest parts of IAM design. Organizations that involve clinical stakeholders early typically see smoother adoption and fewer workarounds.
3. Identity Data Quality and Duplication
IAM systems depend on clean and reliable identity data. However, many health systems struggle with duplicate records, inconsistent role naming, and fragmented directories.
Poor data quality leads to over-permissioning and access drift. It also makes automation unreliable. Leading organizations address this by standardizing identity sources and fixing data issues before large-scale rollout.
4. Emergency Access and Break-Glass Risk
Hospitals must support emergency access for urgent care situations. However, break-glass accounts can introduce significant security exposure if not tightly governed.
Organizations need clear policies, strong monitoring, and automatic review of emergency access events. Without these controls, temporary access often becomes a permanent risk.
5. Regulatory and Audit Complexity
Healthcare IAM operates under constant scrutiny from internal auditors and external regulators. Requirements from HIPAA, HITRUST, and regional privacy laws continue to evolve.
Manual access reviews and fragmented logs make compliance harder. Modern IAM programs must build audit readiness directly into the architecture rather than treating it as an afterthought.
6. Scaling Across Multi-Hospital Environments
Large health systems often span multiple hospitals, clinics, and partner networks. Each environment may have different identity sources and access rules.
Without a unified control plane, access policies become inconsistent across sites. Therefore, scalability planning must happen early. Organizations that design for growth from the start avoid costly rework later.
Healthcare IAM implementation succeeds when these challenges are anticipated, not discovered mid-project. Organizations that address integration, workflow fit, data quality, and governance early build identity programs that remain stable as the enterprise grows.
Best Practices for Building Enterprise-Grade Healthcare IAM
Enterprise healthcare IAM succeeds when organizations design around clinical workflows, enforce least-privilege access, automate lifecycle management, and build compliance visibility into the core architecture.
Building a strong IAM system in healthcare requires more than selecting the right tool. Success depends on disciplined architecture, clean identity data, and rollout strategies that respect clinical realities.
Organizations that follow proven practices typically reduce risk faster and avoid expensive rework later. Below are the best practices large health systems should prioritize.
1. Design Around Clinical Workflows
Access controls must support the pace of care. If login steps slow clinicians, workarounds will appear quickly. Therefore, IAM design should begin with real workflow mapping across departments.
Leading teams:
- Study clinician access patterns before enforcing MFA
- Support fast user switching in shared environments
- Align role models with actual job responsibilities
- Test changes in live clinical scenarios
When security fits the workflow, adoption improves significantly.
2. Enforce Least-Privilege by Default
Over-permissioning remains one of the biggest identity risks in healthcare. Many users accumulate access over time that they no longer need.
Modern IAM programs reduce this risk by:
- Using role-based and attribute-based access controls
- Applying just-in-time access for sensitive systems
- Reviewing privileged roles more frequently
- Removing standing access where possible
This approach limits the blast radius if credentials are compromised.
3. Automate Identity Lifecycle Management
Manual provisioning creates delays and errors. It also increases the risk of orphaned accounts. Automation is essential at enterprise scale.
Strong programs typically:
- Sync directly with HR systems for joiner and leaver events
- Trigger automatic role updates when users move
- Deprovision access immediately upon termination
- Maintain clear audit trails for every change
Automation improves both security and operational efficiency.
4. Build Compliance Into the Architecture
Audit readiness should not depend on manual reporting. Instead, compliance controls must be embedded directly into the IAM system.
Best-in-class organizations:
- Stream identity logs into SIEM platforms
- Maintain immutable access histories
- Run scheduled access certifications
- Align controls with HIPAA and HITRUST requirements
As a result, audits become faster and less disruptive.
5. Plan for Hybrid and Multi-EHR Environments
Most large health systems operate across multiple platforms and facilities. IAM must work consistently across this complexity.
Effective strategies include:
- Using identity federation across environments
- Standardizing role definitions across sites
- Supporting cloud, hybrid, and on-prem systems
- Designing for partner and vendor access early
Planning for scale from the start prevents fragmentation later.
6. Use AI and Analytics for Continuous Improvement
Identity risk changes over time. Static controls are no longer enough in large healthcare environments.
Forward-looking organizations now:
- Monitor user behavior for anomalies
- Detect access drift automatically
- Prioritize high-risk identities for review
- Use analytics to refine role models
These capabilities help security teams stay ahead of emerging threats.
Enterprise healthcare IAM is most effective when it is treated as long-term infrastructure rather than a one-time project. Organizations that follow these best practices build identity programs that remain secure, compliant, and scalable as digital healthcare continues to evolve.
Future Trends in Healthcare Identity and Access Management
Healthcare IAM is evolving toward passwordless access, decentralized identity, AI-driven risk scoring, and unified identity fabrics that support patients, clinicians, and connected devices at scale.
Identity strategy in healthcare is entering a new phase. The focus is shifting from basic access control to intelligent, adaptive identity ecosystems. Organizations that plan early for these trends will be better positioned to scale securely and support future digital models.
Below are the developments enterprise leaders should be watching closely.
1. Passwordless Healthcare Environments
Passwords continue to create friction and risk. Therefore, many health systems are moving toward passwordless authentication using biometrics, device trust, and secure tokens.
This shift helps:
- Reduce credential theft risk
- Speed clinician login workflows
- Lower password reset volumes
- Improve user experience
Over time, passwordless access will become standard in high-maturity environments.
2. Decentralized Identity (DID)
Decentralized identity gives users more control over their credentials. Instead of storing identity data in one central directory, DID uses verifiable digital credentials that users can present when needed.
In healthcare, this model may support:
- Portable patient identity
- Cross-organization trust
- Secure data sharing across networks
- Reduced identity duplication
However, most enterprises are still in early evaluation stages.
3. AI-Driven Identity Risk Scoring
Static access rules are no longer sufficient in complex environments. As a result, IAM platforms are adding AI-driven risk scoring to evaluate user behavior in real time.
These capabilities help organizations:
- Detect unusual login patterns
- Identify high-risk identities faster
- Trigger step-up authentication dynamically
- Prioritize access reviews
AI-driven identity intelligence is becoming a key part of Zero Trust strategies.
4. Identity Fabric Architectures
Large health systems often struggle with fragmented identity tools. Identity fabric architecture addresses this by creating a unified layer that connects IAM, PAM, IGA, and federation services.
The benefits include:
- Consistent policy enforcement
- Better cross-system visibility
- Simplified integration across environments
- Improved scalability for mergers and growth
Many enterprises now view identity fabric as the long-term architectural direction.
5. Device and IoMT Identity Expansion
The number of connected medical devices continues to grow rapidly. Each device introduces a new identity that must be trusted and monitored.
Modern IAM programs are expanding to include:
- IoMT device authentication
- Device trust validation
- Network-level identity enforcement
- Continuous monitoring of device behavior
Organizations that ignore device identity often leave major security gaps.
6. Patient-Controlled Identity Models
Patients increasingly expect control over how their data is accessed and shared. New identity models are emerging to support consent-driven access and portable digital credentials.
These models may enable:
- Self-managed patient identities
- Granular consent management
- Cross-provider data portability
- Stronger digital front door experiences
While adoption is still evolving, forward-looking providers are already preparing their architecture.
For enterprise leaders, these trends signal a clear shift. Healthcare IAM is moving from static access management toward intelligent identity ecosystems. Organizations that align their IAM strategy now will be better prepared to support AI initiatives, digital care expansion, and long-term enterprise growth.
Conclusion
Healthcare identity and access management has moved far beyond basic login control. It now sits at the core of security, compliance, and digital care delivery. Organizations that treat IAM as strategic infrastructure are better positioned to reduce risk, support clinicians, and scale new digital services with confidence.
However, success depends on architecture, not just tools. Programs built with clean identity data, strong governance, and phased execution consistently deliver better outcomes. This is where the right partner matters.
Intellivon helps enterprises design and implement enterprise-grade IAM systems that hold up in real healthcare environments. Connect with our team to build a secure and scalable identity foundation.
Build a Healthcare Identity & Access Management Platform With Intellivon
At Intellivon, healthcare IAM platforms are engineered as regulated identity infrastructure, not access tools layered onto fragmented environments. Every architectural and delivery decision focuses on clinical workflow fit, strong governance, and long-term operational stability.
As identity programs expand across hospitals, partner networks, and digital care channels, consistency becomes critical. Access policies, audit visibility, and performance must remain stable even as user populations, device connections, and integration points grow. This disciplined approach helps healthcare organizations modernize securely without introducing hidden identity risk or compliance gaps.
Why Partner With Intellivon?
- Enterprise-grade IAM architecture designed for complex healthcare ecosystems
- Proven delivery across multi-hospital and multi-EHR environments
- Compliance-by-design model with embedded audit readiness and policy enforcement
- Secure, modular platform supporting cloud, hybrid, and on-prem deployments
- AI-ready identity foundation enabling advanced analytics and adaptive access controls
Book a strategy call to explore how Intellivon can help you design and scale a healthcare IAM platform with confidence, control, and long-term enterprise value.
FAQs
Q1. What is identity and access management in healthcare?
A1. Identity and access management in healthcare is the framework that verifies user identities and controls what clinicians, staff, patients, and partners can access. A modern IAM system automates provisioning, enforces least-privilege access, and maintains audit-ready visibility across clinical and business systems.
Q2. Why is IAM important for hospitals and health systems?
A2. IAM is critical because identity misuse is a leading cause of healthcare breaches. A strong IAM system reduces credential risk, supports compliance requirements, speeds clinician access, and improves overall operational control across complex hospital environments.
Q3. How does healthcare IAM support HIPAA compliance?
Healthcare IAM supports HIPAA by enforcing role-based access, enabling strong authentication, maintaining detailed audit logs, and automating user lifecycle management. These controls help organizations protect PHI and demonstrate compliance during audits.
Q4. Can IAM integrate with EHR systems like Epic and Cerner?
A4. Yes. Modern IAM platforms integrate with major EHR systems using APIs, federation, and healthcare middleware. With the right architecture, organizations can enable single sign-on, automated provisioning, and consistent access policies across EHR environments.
Q5. How long does it take to implement a healthcare IAM system?
A5. Implementation timelines vary based on system complexity, data quality, and integration scope. Large health systems typically follow a phased rollout that can take 12 to 24 months, although targeted IAM improvements can deliver value much earlier.