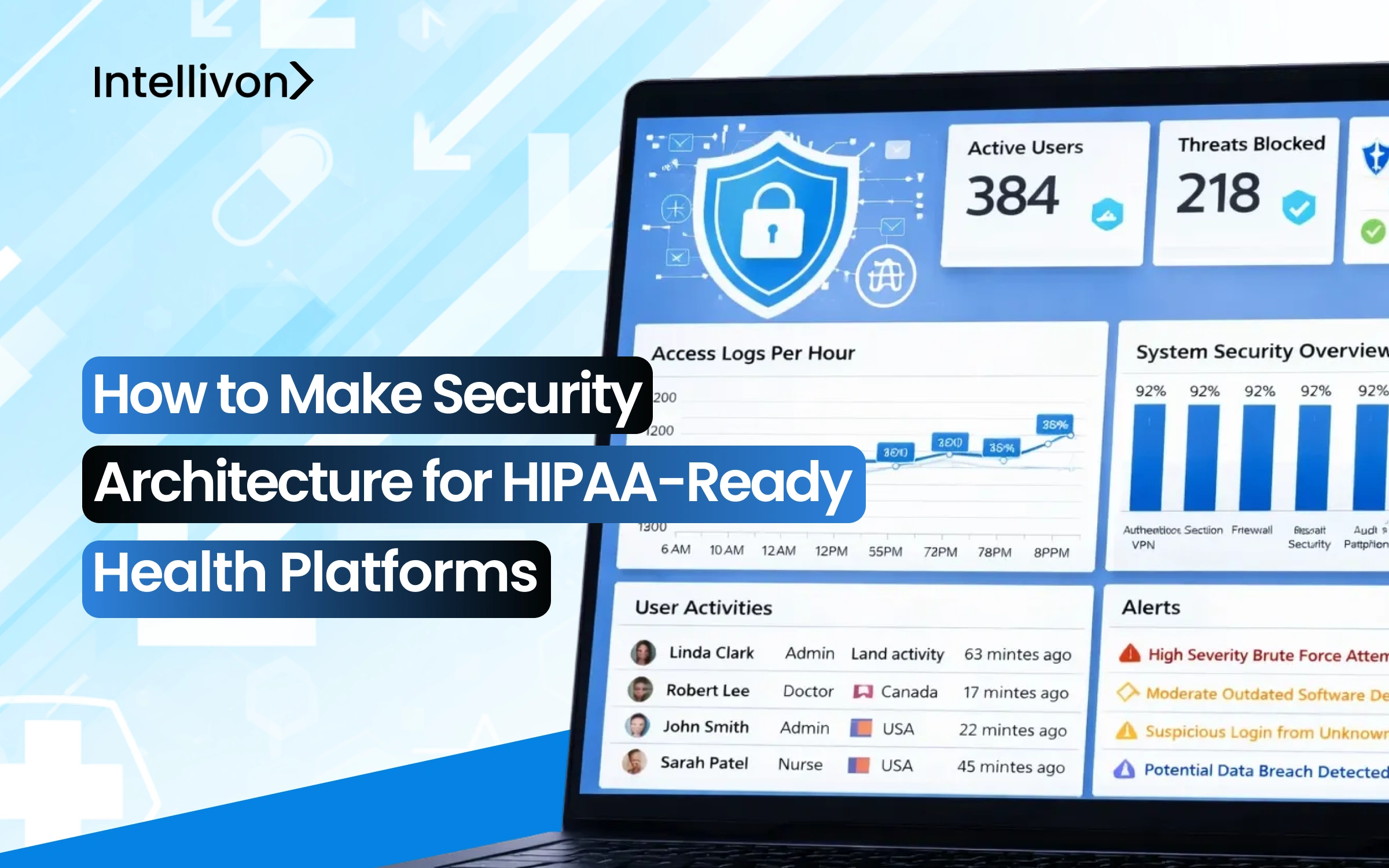
If a healthcare app is HIPAA compliant, it can feel like you have already reached the finishing line. However, rather than risks appearing at launch, they build gradually as the platform expands beyond its original design. Every new EHR connection, partner integration, cloud workload, or analytics project creates another way for protected health information (PHI) to be shared.
Over time, identities multiply, data copies spread into new environments, and maintaining audit visibility from start to finish becomes difficult. When such problems occur in established healthcare systems, it is an indicator that the security framework was never designed to handle this level of complexity.
Strengthening security at the architectural level changes this trend. Doing this enforces trust boundaries, tracking PHI movement becomes manageable, and the platform stays stable as it grows. At Intellivon, we design HIPAA-ready platforms with this discipline in mind. This blog will cover our expertise in creating a security architecture that performs well during real enterprise growth.
Why HIPAA-Compliant Platforms Require Strong Security
HIPAA-compliant platforms require strong security to protect sensitive patient health information (PHI) from growing breach activity across the healthcare sector. Recent data shows more than 725 major incidents reported annually, exposing millions of records and driving costs that can reach up to $11 million per breach.
This trend is reshaping how healthcare organizations approach platform design. Robust security not only protects patient data but also strengthens trust, reduces compliance exposure, and supports sustainable growth in a tightly regulated environment.
The global healthcare compliance software market is shifting quickly as regulatory scrutiny intensifies and AI becomes central to governance. The market reached USD 3.35 billion in 2024 and is projected to grow to USD 11.88 billion by 2034, expanding at a steady 13.5% CAGR.
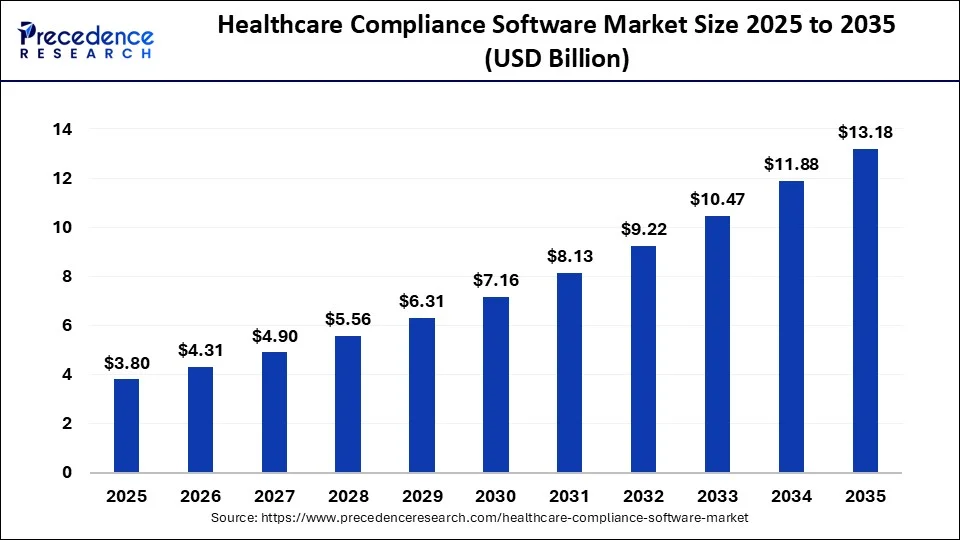
Market Insights:
- The HIPAA compliance software market is projected to grow at a 7.8% CAGR through 2033, driven by AI adoption, cloud expansion, and rising telehealth demand.
- North America continues to lead the market due to stricter regulatory enforcement and higher enterprise compliance maturity across healthcare ecosystems.
- Vendors increasingly prioritize automated risk assessments and strong tenant isolation to reduce exposure from expanding third-party and partner integrations.
- Healthcare still carries the highest breach costs across industries, making identity-aware platforms critical for controlling loss and strengthening long-term risk posture.
Healthcare platforms cannot achieve HIPAA readiness through policy alone. Security architecture is what turns regulatory intent into operational protection. As digital health ecosystems expand, the ability to protect PHI consistently becomes a core platform requirement and not an optional enhancement.
Below are the key reasons security remains foundational to HIPAA-compliant platforms.
1. PHI Has High Exposure and Long-Term Impact
PHI carries deep clinical, financial, and identity value. Unlike payment data, medical records cannot simply be reissued after exposure. The impact on patients and providers can persist for years.
Because of this sensitivity, healthcare platforms remain attractive targets. Strong security controls help keep PHI protected across storage, transmission, and active use.
2. Platform Complexity Expands the Attack Surface
Healthcare platforms rarely operate in isolation today. EHR integrations, partner APIs, cloud services, mobile apps, and analytics tools steadily expand the environment.
Each new connection introduces another trust boundary that must be enforced. Without architectural discipline, small control gaps can grow into meaningful exposure as the platform scales.
3. Checklist Compliance Does Not Scale With Growth
Many teams implement the required safeguards and assume protection is complete. Over time, identity sprawl, permission drift, and uncontrolled data movement begin to surface.
These risks rarely appear immediately. They tend to emerge during audits, incidents, or partner reviews. Embedding security into the architecture helps maintain protection as complexity increases.
4. Patient Care Depends on Platform Stability
Security incidents in healthcare rarely affect data alone. System outages, data integrity problems, or ransomware events can disrupt clinical workflows and delay care.
A strong security architecture supports both privacy and availability. It helps ensure clinicians, staff, and patients can rely on the platform even under stress.
5. Regulatory and Business Risks Continue to Rise
HIPAA enforcement remains active, and breach reporting requirements are strict. When incidents occur, organizations face regulatory scrutiny, contractual pressure, financial loss, and reputational damage.
A well-designed security architecture lowers the likelihood of reportable events. It also demonstrates due diligence during audits and partner evaluations.
HIPAA compliance establishes an essential baseline, but it is not the finish line. As healthcare platforms become more interconnected, a strong security architecture is what preserves PHI protection, sustains audit readiness, and supports safe enterprise-scale growth.
What Makes a Health Platform Truly HIPAA-Ready
HIPAA readiness is not proven by passing a single audit. It shows up in how consistently a platform protects PHI as usage grows and integrations expand. The strongest healthcare platforms treat compliance as an architectural discipline, not a checklist. They build controls that continue working under real production pressure.
Below are the core elements that separate baseline compliance from true HIPAA readiness.
1. Clear Identity and Access Controls
Access must be tightly governed across workforce users, patients, vendors, and system services. Each group should follow least-privilege rules and strong authentication.
When identity controls are structured correctly, unauthorized access becomes harder, and investigations become faster. This is the first line of defense in any HIPAA security architecture.
2. End-to-End PHI Protection
PHI should remain protected wherever it moves. That includes databases, APIs, analytics pipelines, backups, and archives.
Encryption alone is not enough. Mature platforms also enforce data classification, controlled handling, and traceable movement. These controls prevent sensitive information from spreading into unmanaged environments.
3. Secure and Governed Integrations
Healthcare platforms rely heavily on external connections. EHR systems, partner apps, and digital front doors all exchange regulated data.
Each integration must enforce consistent authentication, authorization, and consent rules. Strong governance allows organizations to scale interoperability without losing control of PHI.
4. Continuous Monitoring and Audit Visibility
Security teams need more than basic logs. They need clear visibility into who accessed PHI, when it happened, and through which pathway.
Continuous monitoring improves breach detection and simplifies audits. It also gives leadership confidence that the platform remains under control as activity grows.
A platform becomes truly HIPAA-ready when identity, data protection, integrations, and monitoring work together as one system. Organizations that invest in this level of architectural discipline are better prepared to scale securely, pass audits with confidence, and support long-term digital health growth.
Core Security Architecture Layers for HIPAA Platforms
A HIPAA-ready platform stays secure when protection works as a coordinated system, not as isolated tools. Each layer in the architecture controls a different risk surface. Together, they keep PHI protected as the environment grows in users, integrations, and data volume.
The model below outlines the core layers that help healthcare platforms maintain consistent security under real-world enterprise pressure.
1. Identity Trust Architecture
Identity is now the primary security boundary. Healthcare environments include workforce users, patients, vendors, and machine services. Each group must be governed with clear separation and least-privilege access.
Mature platforms enforce zero trust principles, strong authentication, and just-in-time provisioning. They also control privileged accounts and machine identities with the same discipline applied to human users.
When identity is structured correctly, unauthorized access becomes harder, and incident impact stays contained.
2. PHI Data Protection Architecture
PHI must remain protected wherever it lives and wherever it travels. This includes databases, APIs, analytics pipelines, backups, and archives.
Strong architectures go beyond basic encryption. They apply field-level protection, tokenization where appropriate, and clear data classification pipelines.
They also maintain lineage tracking so teams can see how sensitive data moves across the environment. Multi-tenant isolation and compliant archival practices further reduce long-term exposure.
3. Application and API Security Layer
Modern healthcare platforms depend heavily on APIs and external connections. Every FHIR endpoint, partner integration, and mobile workflow introduces another access path.
Effective platforms enforce gateway policies, validate payloads, and apply consent-aware authorization. They also secure SMART on FHIR implementations and sandbox third-party applications.
Tight control over tokens and sessions ensures external connectivity does not weaken the overall posture.
4. Infrastructure and Network Security
Cloud adoption and containerized workloads have expanded the healthcare attack surface. Security must extend deep into runtime environments.
Leading platforms implement zero-trust network segmentation and inspect east-west traffic inside the environment. They govern workload identities in Kubernetes, protect secrets carefully, and secure CI/CD pipelines.
Container runtime controls and strict environment isolation help prevent misconfigurations from turning into data exposure.
5. Governance, Monitoring, and Audit Resilience
Strong security depends on continuous visibility. Basic logging is no longer enough for regulated healthcare environments.
Mature platforms maintain immutable audit logs and correlate activity across systems. They can reconstruct PHI access end-to-end when questions arise. Real-time anomaly detection and behavior analytics help surface threats early.
Automated evidence collection also reduces audit friction and supports faster regulatory response.
A HIPAA-ready health platform depends on how well these layers work together. When identity, data protection, APIs, infrastructure, and monitoring operate as one system, organizations gain stronger control over PHI, better audit confidence, and a more resilient foundation for future growth.
Securing PHI Across Interoperability and FHIR Ecosystems
FHIR-based interoperability has expanded how healthcare platforms exchange data. As more apps, partners, and patient tools connect, PHI moves across far more boundaries than before. Security must keep pace with this shift.
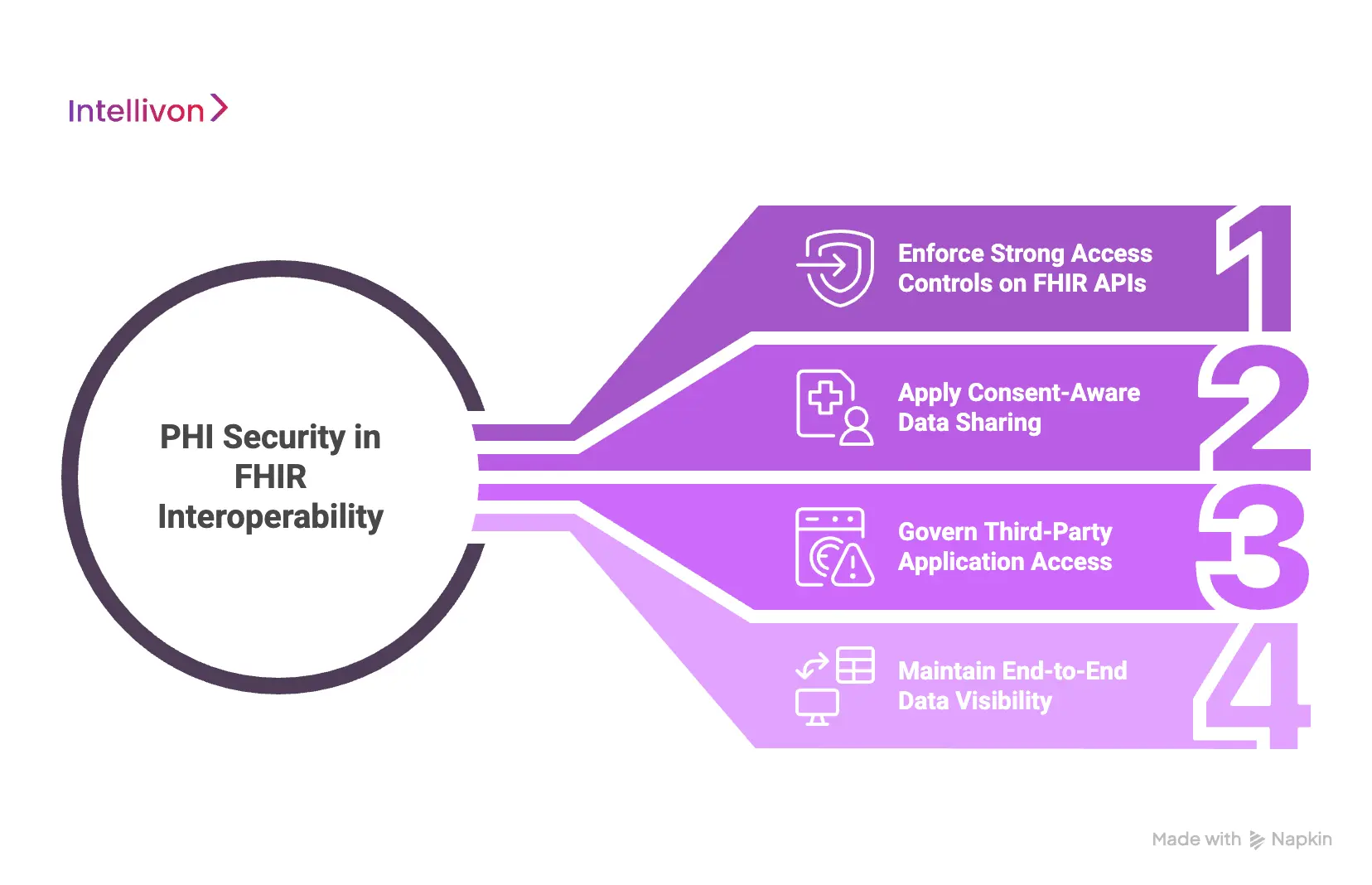
1. Enforce Strong Access Controls on FHIR APIs
FHIR endpoints expose clinical data through standardized APIs. Because these interfaces are widely accessible, weak scope design or over-permissioned tokens can create silent exposure.
Mature platforms validate OAuth scopes tightly and enforce least-privilege access for every client. They also monitor token lifetime, refresh patterns, and dynamic client behavior. This level of control ensures that only approved applications retrieve the minimum data required.
Over time, strong FHIR access governance reduces the risk of partner misuse and limits the blast radius if credentials are compromised.
2. Apply Consent-Aware Data Sharing
Technical authorization does not always reflect patient intent. In regulated environments, access decisions must align with what the patient has actually approved.
Leading platforms embed consent checks directly into SMART on FHIR workflows and downstream API calls. They continuously validate whether the requested data falls within approved consent boundaries.
This approach protects patient trust and prevents over-disclosure during cross-organization exchange. It also strengthens audit defensibility when regulators review data access patterns.
3. Govern Third-Party Application Access
Third-party apps are now a major source of PHI risk. Each connected partner brings its own security posture, release cycle, and operational discipline.
Strong platforms treat partner access as a contained risk zone. They sandbox external apps, restrict scopes carefully, and monitor behavioral patterns over time. They also review partner access regularly as ecosystems evolve.
This containment model limits exposure if a vendor environment is compromised and prevents uncontrolled lateral movement.
4. Maintain End-to-End Data Visibility
Interoperability creates complex data flows that span multiple systems. Without unified visibility, teams cannot easily answer who accessed PHI, when it happened, or how the data moved.
Advanced platforms correlate activity across APIs, identity systems, and downstream services. They maintain traceability that supports both incident response and regulatory review.
As a result, security teams can investigate faster, and leadership gains confidence that PHI movement remains under control.
FHIR interoperability enables powerful care and data exchange. However, it also increases the number of PHI exposure points. Platforms that enforce precise access control, align consent, contain partners, and provide full traceability are better prepared to scale interoperability without weakening their HIPAA security posture.
Designing HIPAA-Ready Platforms for AI and Advanced Analytics
AI and analytics programs are now embedded in many healthcare platforms. Risk scoring, clinical decision support, population health models, and fraud detection all depend on large data pipelines. As these workloads expand, PHI begins to flow into environments that were not part of the original compliance design.
Security must extend into these pipelines early. Otherwise, sensitive data can spread into training, feature engineering, and inference workflows without proper controls.
1. Control PHI Entry Into Training Pipelines
AI models depend on large datasets. Without strict intake controls, PHI can enter training environments in raw or overexposed form.
Mature platforms define clear ingestion gates. They validate data classification, apply masking or tokenization where required, and restrict who can stage training datasets. Teams also separate research environments from production PHI stores.
This approach reduces the chance that sensitive records become widely replicated across data science workflows.
2. Secure Feature Stores and Analytics Workspaces
Feature stores and analytics environments often aggregate data from many sources. Over time, they can become high-density PHI zones if not governed carefully.
Strong architectures apply the same identity and access discipline used in clinical systems. They enforce least-privilege access, segment workloads, and monitor query behavior continuously.
As a result, analytics teams can work efficiently while the organization retains tight control over sensitive data exposure.
3. Enforce De-Identification and Re-Identification Controls
Not every AI use case requires direct identifiers. However, improper de-identification can still create re-identification risk, especially when datasets are combined.
Forward-looking platforms define clear de-identification standards and validate them during data preparation. They also track when re-identification is permitted and who can perform it.
This balance supports innovation while keeping regulatory exposure in check.
4. Govern Model Access and Inference Workflows
Risk does not stop after model training. Inference endpoints and model APIs can also expose sensitive signals if access is loosely controlled.
Mature platforms authenticate every model request, enforce usage policies, and monitor abnormal query patterns. They also review how downstream applications consume model outputs.
These controls help prevent model misuse and reduce the chance of unintended PHI leakage.
5. Maintain Auditability Across AI Workflows
AI pipelines introduce new audit challenges. Data moves through feature engineering, model training, evaluation, and deployment stages.
Strong platforms maintain traceability across this lifecycle. They log dataset lineage, model access, and inference activity in a way that supports regulatory review.
With this visibility in place, organizations can innovate with AI while preserving HIPAA readiness.
AI and advanced analytics create significant clinical and operational value. At the same time, they expand the PHI risk surface beyond traditional application boundaries. Platforms that govern training pipelines, analytics environments, model access, and audit visibility can support AI innovation without weakening their HIPAA security architecture.
Third-Party and Vendor Risk in HIPAA Architectures
Healthcare platforms rarely operate alone. Payers, labs, digital health apps, cloud providers, and support vendors all interact with regulated data. As these relationships expand, PHI exposure often shifts outside the organization’s direct control.
Security architecture must account for this extended ecosystem. Without clear technical guardrails, one over-permissioned partner or compromised vendor account can widen the blast radius quickly.
1. Enforce Least-Privilege Vendor Access
Vendors typically require targeted access to perform specific functions. Problems arise when permissions are broad or left in place longer than needed.
Mature platforms grant vendors only the minimum access required and review those privileges regularly. They also apply strong authentication and session controls to external accounts.
This discipline reduces unnecessary exposure and limits what an attacker could reach through a compromised partner credential.
2. Isolate Partner and Vendor Workloads
Shared environments increase risk when vendor activities are not clearly separated from core clinical systems.
Strong architectures isolate partner workloads through network segmentation, scoped APIs, and tenant boundaries. They prevent vendors from moving laterally across unrelated services.
When isolation is enforced properly, incidents remain contained instead of spreading across the platform.
3. Strengthen BAA and Technical Enforcement Alignment
Business Associate Agreements set legal expectations, but technical controls must reinforce them.
Leading organizations map BAA obligations directly to access policies, logging requirements, and data handling rules. They also verify that vendors meet required security baselines before granting access.
This alignment ensures contractual protections translate into real operational safeguards.
4. Monitor Third-Party Activity Continuously
Vendor access should never be treated as a set-and-forget decision. Usage patterns change, and partner environments evolve.
Advanced platforms monitor external activity in real time. They flag unusual access patterns, unexpected data volumes, or abnormal query behavior.
Continuous oversight allows teams to respond quickly if partner activity deviates from expected norms.
5. Prepare for Vendor Incident Containment
Even well-managed partners can experience security events. Architecture should assume that a vendor environment may eventually be compromised.
Prepared platforms define containment controls in advance. They can revoke access quickly, rotate credentials, and trace PHI exposure paths without delay.
This readiness reduces response time and helps protect the broader ecosystem when incidents occur.
Third-party relationships are essential to modern healthcare delivery. However, they also expand the PHI risk surface. Platforms that enforce least-privilege access, isolate partner activity, align technical controls with BAAs, and monitor vendors continuously are better positioned to manage ecosystem risk while maintaining HIPAA security integrity.
Common Security Architecture Mistakes That Break HIPAA at Scale
Most healthcare platforms do not fail because safeguards are missing. They fail because the architecture cannot sustain control as the environment grows. Small design shortcuts that seem manageable early can create serious exposure later.
The patterns below appear repeatedly in large healthcare ecosystems. Addressing them early helps prevent costly remediation and audit pressure.
1. Identity Models Built Only for Workforce Users
Many platforms design access controls around internal staff first. Over time, patients, partners, vendors, and machine identities enter the environment and stretch the original model. This creates inconsistent policies, over-permissioned accounts, and blind spots across service access. As identity types multiply, unauthorized access becomes harder to detect and contain.
Intellivon solves this by designing a unified identity architecture from the start. Workforce, patient, partner, and machine identities are governed through a single zero-trust framework. Access remains least-privileged and consistently enforced as the ecosystem expands.
2. Over-Permissioned Service and API Accounts
Service accounts and API credentials often accumulate broad access over time. Teams grant extra permissions for speed, then rarely revisit them. In large environments, these machine identities become quite high-risk entry points. Attackers frequently target them because monitoring is weaker than for human users.
We address this through strict machine identity governance. The platform enforces scoped access, short-lived credentials, and continuous monitoring of service behavior. This keeps automated access tightly controlled and reduces hidden exposure.
3. Flat Network Trust Zones
Some healthcare environments still rely on wide internal trust zones. Once inside the network, workloads may communicate with minimal restriction. At scale, this design increases lateral movement risk during an incident. A single compromised workload can potentially reach sensitive systems.
Intellivon implements zero-trust network segmentation across environments. East-west traffic is inspected, and workloads communicate only through explicitly approved paths. This architecture sharply limits the blast radius if a breach occurs.
4. Uncontrolled PHI Replication Into Analytics Environments
Analytics and reporting teams often copy PHI into data lakes or research environments. Over time, these secondary stores become poorly governed and difficult to audit. Sensitive data spreads beyond the controls applied to core clinical systems. This pattern creates significant compliance and breach risk.
Our experts prevent this through governed data pipelines and classification controls. PHI movement is tracked, minimized, and protected with tokenization or masking where appropriate. Analytics teams still gain insight, but exposure stays tightly contained.
5. Fragmented Logging Without Correlation
Many platforms generate large volumes of logs but lack unified visibility. During investigations, teams struggle to reconstruct who accessed PHI across systems. This slows incident response and complicates regulatory reviews. Basic logging alone does not provide true audit readiness.
Intellivon builds centralized observability with cross-system traceability. Identity events, API activity, and data access signals are correlated in one view. Security teams can quickly follow PHI movement and respond with confidence.
6. Weak Third-Party Containment
Partner and vendor access often grows faster than governance. External apps may receive broad scopes or operate in shared environments. If a partner environment is compromised, exposure can spread quickly. This risk increases as digital ecosystems expand.
We apply strict partner isolation and continuous vendor monitoring. External access is tightly scoped, behavior is observed in real time, and containment controls are pre-defined. This keeps ecosystem growth from weakening the platform’s HIPAA security posture.
HIPAA failures at scale usually trace back to architectural gaps, not missing controls. Organizations that address identity sprawl, machine access, network segmentation, data movement, observability, and partner containment early are far better positioned to sustain compliance as they grow.
How We Design HIPAA-Ready Security Architectures
HIPAA readiness holds up when security is treated as an engineering process, not a checklist exercise. The work starts with clarity on where PHI lives, how it moves, and who touches it. From there, the architecture is designed to enforce control as the platform scales across users, partners, and regions.
Below is the step-by-step process followed to design HIPAA-ready security architecture for enterprise health platforms.
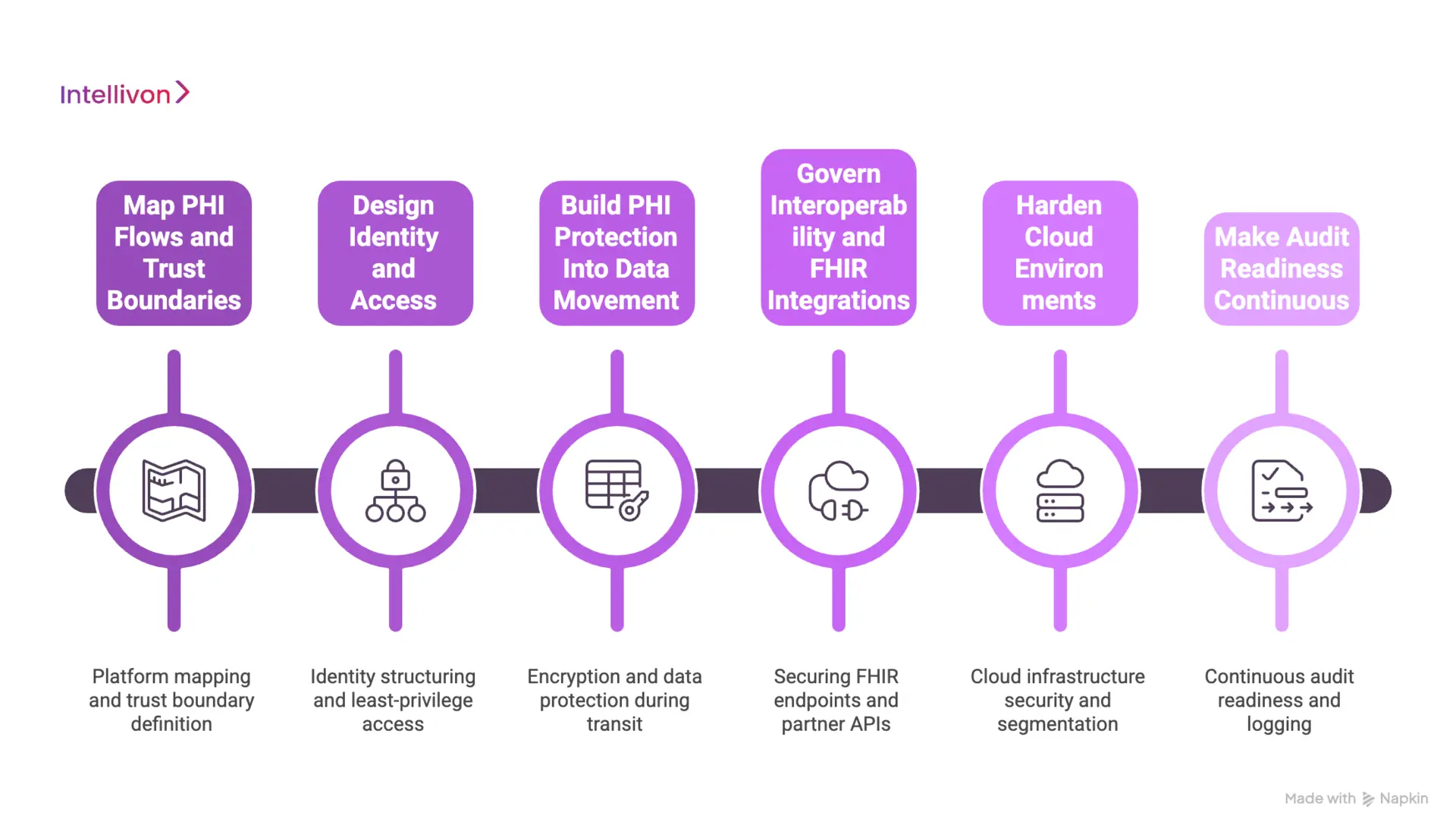
Step 1: Map PHI Flows and Trust Boundaries
First, the platform is mapped end-to-end. This includes data sources, integrations, storage layers, and user groups. PHI pathways are identified across APIs, messaging, analytics, and third-party connections.
Next, trust boundaries are defined. These boundaries show where risk enters the platform and where controls must be strongest. This step prevents blind spots that appear later during audits or incidents.
Step 2: Design Identity and Access
Then, identity is structured as the main security layer. Workforce users, patients, vendors, and machine services are separated and governed with clear rules.
Least-privilege access is enforced across the platform. Strong authentication, session controls, and privileged access governance are designed into the architecture. This ensures access remains consistent even as new apps and partners are added.
Step 3: Build PHI Protection Into Data Movement
After that, PHI protection is designed around how data actually travels. Encryption is applied, but the focus also stays on classification, minimization, and traceability.
Field-level protection, tokenization where appropriate, and lineage tracking are built into workflows. This reduces uncontrolled PHI replication into pipelines, caches, and downstream systems.
Step 4: Govern Interoperability and FHIR Integrations
Next, interoperability is treated as a high-risk boundary. FHIR endpoints, partner APIs, and patient app access are secured with strict policy enforcement.
Consent-aware access controls are embedded into exchange workflows. Payload validation and scope controls ensure external connections do not widen PHI exposure. This enables safe data sharing without weakening compliance posture.
Step 5: Harden Cloud Environments
Then, infrastructure security is applied where platforms run today. Cloud, hybrid, and container environments are segmented and protected.
Network isolation, workload identity, secrets management, and secure CI/CD controls are enforced. Runtime protections help prevent misconfigurations from becoming production incidents.
Step 6: Make Audit Readiness Continuous
Finally, audit readiness is built into operations. Logging is structured for traceability, not just volume. Signals from identity, APIs, and data access are correlated into one view.
Teams can reconstruct PHI access quickly and respond faster during reviews or incidents. This reduces audit stress and strengthens long-term security governance.
HIPAA-ready security architecture is achieved through disciplined design steps. When PHI flows are mapped, identity is governed, data movement is controlled, integrations are secured, infrastructure is hardened, and audit readiness is continuous, the platform stays resilient as enterprise ecosystems grow.
Conclusion
HIPAA readiness is not achieved by enabling a few controls and moving on. It depends on how well the platform is designed to manage risk as it grows. As healthcare ecosystems become more connected, security must stay consistent across identities, data flows, integrations, and infrastructure.
Organizations that focus on architecture early avoid costly fixes later. They gain stronger audit confidence, safer interoperability, and better operational stability. With the right security foundation in place, healthcare platforms can scale innovation while keeping protected health information secure and compliant over time.
Build HIPAA-Ready Health Platforms With Intellivon
At Intellivon, HIPAA-ready health platforms are engineered as regulated healthcare infrastructure, not as security layers added after development. Every architectural and delivery decision focuses on protecting PHI, governing identity, and controlling interoperability at scale. This approach helps platforms operate safely across providers, partners, regions, and evolving regulatory expectations, not just during initial deployment.
As enterprise healthcare environments expand, consistency becomes critical. Governance, performance, and audit readiness remain stable even as user volume, integrations, and data exchange grow. Organizations maintain firm control over patient data, access permissions, and compliance posture without introducing operational friction or hidden risk.
Why Partner With Intellivon?
- Enterprise-grade HIPAA security architecture built for regulated healthcare ecosystems
- Proven delivery across hospitals, health networks, and digital health platforms
- Compliance-by-design approach with embedded audit visibility and policy enforcement
- Secure modular infrastructure supporting cloud, hybrid, and on-prem deployments
- AI-enabled monitoring, risk detection, and automation with strong governance controls
Book a strategy call to explore how Intellivon can help you build and scale HIPAA-ready health platforms with confidence, control, and long-term enterprise value.
FAQs
Q1 What is HIPAA security architecture in healthcare platforms?
A1. HIPAA security architecture is the structured way a healthcare platform protects PHI across users, systems, and data flows. It includes identity controls, data protection, API security, infrastructure safeguards, and continuous monitoring. The goal is to keep patient information secure as the platform scales and connects with partners.
Q2. Why is HIPAA compliance alone not enough for healthcare platforms?
A2. HIPAA compliance confirms that required safeguards exist at a point in time. However, risk grows as integrations, users, and data movement increase. Without strong architecture, gaps can appear across APIs, identities, and analytics pipelines. A well-designed security foundation helps maintain protection as the environment evolves.
Q3. What are the core layers of HIPAA security architecture?
A3. Most enterprise platforms rely on five core layers. These include identity and access control, PHI data protection, application and API security, infrastructure and network protection, and continuous monitoring. When these layers work together, organizations gain stronger control over PHI and better audit readiness.
Q4. How does FHIR interoperability increase PHI risk?
A4. FHIR APIs make it easier to exchange healthcare data across apps and partners. However, each new connection creates another path where PHI can be exposed. Without strong access controls, consent checks, and monitoring, data can travel further than intended. Proper governance keeps interoperability safe and compliant.
Q5. How can healthcare organizations strengthen their HIPAA security posture?
A5. Organizations should start by mapping PHI flows and reviewing trust boundaries. Next, they should enforce least-privilege access, secure APIs, segment infrastructure, and improve monitoring.Therefore, taking an architectural approach helps reduce breach risk, simplify audits, and support safe platform growth.